Learn about Security
Zunami Protocol suspected to have encountered an attack, collateral remains safe.
Decentralized stablecoin yield protocol Zunami Protocol announced on Twitter that zStables has been suspected of being attacked, but the collateral is still safe, and…
The subtleties of error handling defects in MPC
Yesterday, the Fireblocks cryptography research team announced at the Black Hat USA conference that they have discovered an error handling defect in the multi-party…
DeFi Security Summit 2023 Review What is the Cryptocurrency Security Community Discussing?
Cryptographic security researcher LianGuaishov participated in the DeFi Security Summit 2023, which was held prior to EthCC, and summarized the insights gained at the…
Full Guide to Improvements in Starknet Syntax
The second version of the Cairo compiler has made changes to the Starknet syntax, making the code more clear and secure. The public interface…
New phishing alert: Attackers on BNB Chain are using fake authorizations to deceive users into giving away Gas.
Partner of y2z Ventures, blanker.eth, has written a reminder about a new phishing method where scammers use Revoke Cash and Rabby to remind users…
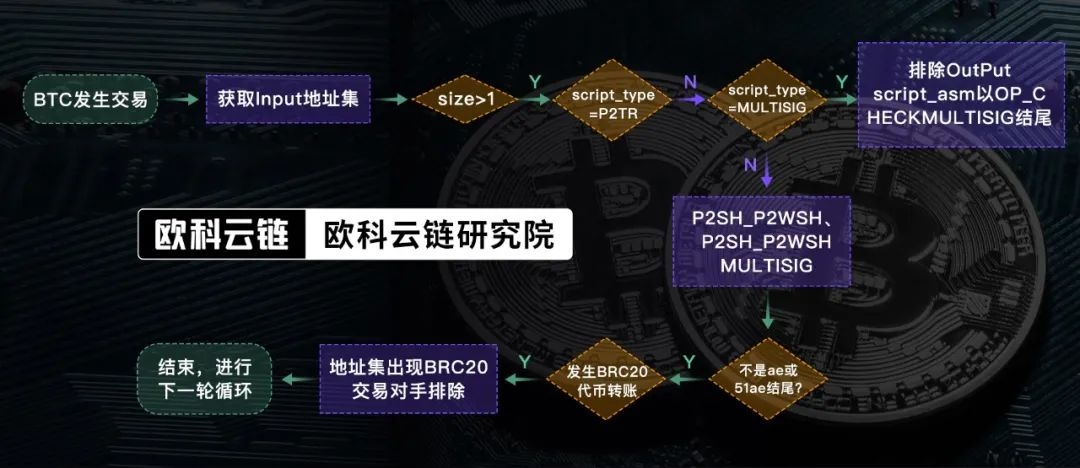
Latest discovery: BRC-20 transactions are not suitable for BTC-UTXO label model.
What impact does PSBT have on BRC20 address labels?
Cult of Move’s Blasphemer: The mechanical structure of this building is flawed, it just hasn’t collapsed yet.
Last response regarding why Aptos and Sui don't work.
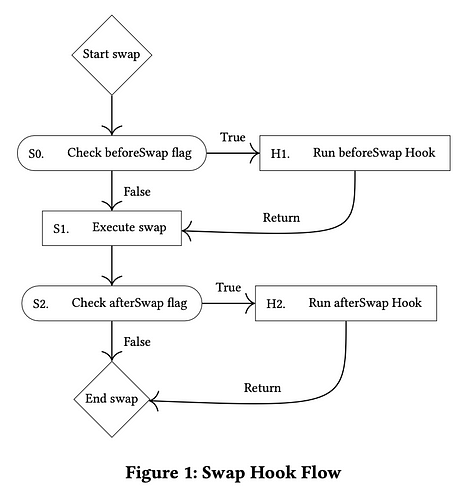
Uniswap Evolution: A Thousand Miles Journey, Opportunities and Impact of V4
Uniswap V1 was launched in November 2018. However, the prototype of Uniswap had already been formed in the previous year. In 2017, founder Hayden…
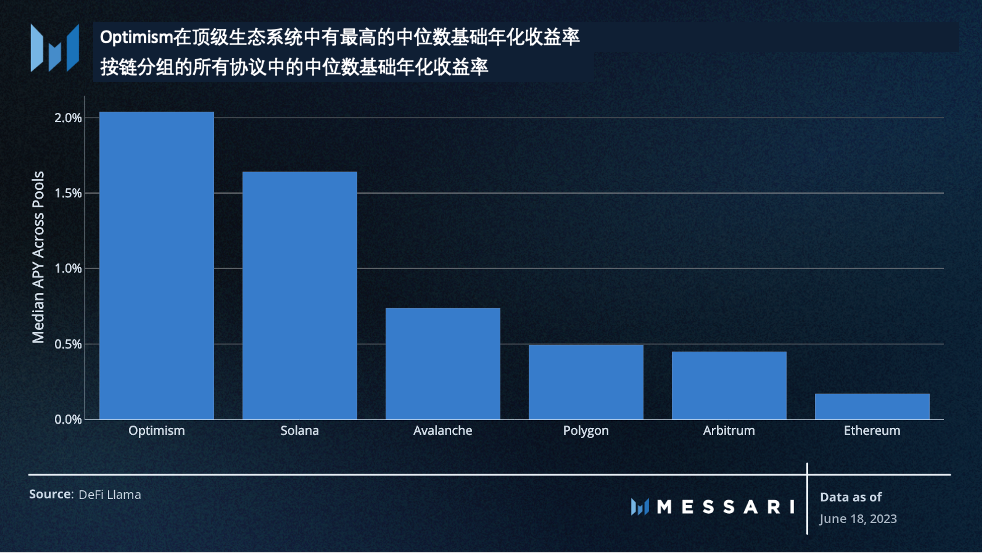
DeFi Briefing: Protocols Without Oracles
Amidst a relatively calm market environment, a new wave of DeFi builders is attracting attention by reimagining the architecture of lending and derivative protocols.…
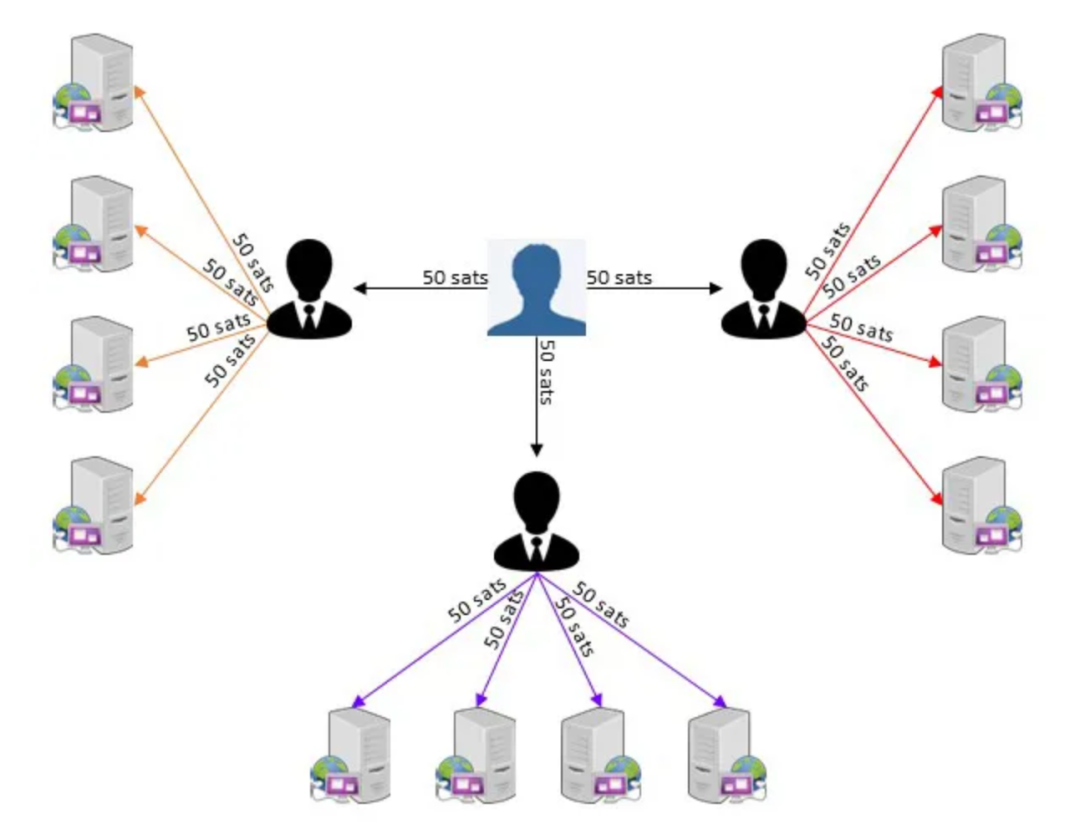
Nostr2.0: As a layer 2 off-chain data storage layer for Bitcoin
This article will explain how Nostr relay synchronizes its data while maintaining its lightweight features, allowing users to selectively delete data, which Layer 1…
Find the right Blockchain Investment for you
Web 3.0 is coming, whether buy Coins, NFTs or just Coding, everyone can participate.