This article is jointly written and published by independent researcher Spinach Spinach! (twitter@wzxznl) and Beosin security researcher Sivan .
Hackers, a dreaded presence for everyone in the Web3 ecosystem. For project teams, the open source nature of code development makes them afraid to write a line of code wrong, as hackers from all over the world may be targeting them. Once a security incident occurs, the consequences are difficult to bear.
For individuals, if you don’t understand what the operation you are doing means, every on-chain interaction or signature you make could potentially lead to your assets being stolen. Therefore, security has always been one of the most troublesome issues in the encrypted world. Moreover, due to the characteristics of blockchain, once assets are stolen, there is almost no way to recover them, so having security knowledge in the encrypted world is especially important.
Recently, a new phishing technique that has been active for nearly two months has been discovered , where assets are stolen by just signing. The technique is extremely covert and difficult to prevent, and addresses that have interacted with Uniswap may be exposed to risks. This article, jointly written by Beosin and independent researcher Spinach Spinach, aims to educate people about this signature phishing technique and minimize further asset loss.
- Deep dive into Archway: Cosmos’ value capture chain
- Conversation between Aztec and Espresso: Exploring the Decentralization of Sorters
- BlockingraFi and two other major encrypted VC jointly sued the founder of Curve for “fraud” and manipulation of trade secrets
The following is a personal account from Spinach Spinach:
The Incident
Recently, a friend (referred to as “Little A”) had their wallet assets stolen and came to Spinach Spinach for help. Unlike common theft methods, Little A did not leak their private key nor interact with the phishing website’s contract. Thus, Spinach Spinach began investigating the asset theft incident.
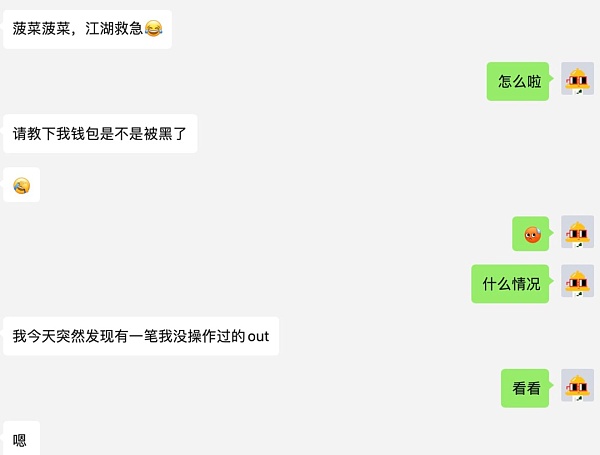
In the blockchain browser, it can be seen that the transferred USDT in Little A’s wallet was transferred through the Transfer From function. To explain briefly, when we transfer tokens on Ethereum, we actually call the Transfer function of the token smart contract. The difference between the two is that Transfer is an operation performed by the asset owner to transfer the token to another address, while Transfer From is a third party transferring the tokens in the address to another address. This means that the stolen assets were transferred by another address, not by leaking the wallet’s private key.

By looking up the transaction details, we can find some key clues:
-
The address ending with fd51 transferred Little A’s assets to the address ending with a0c8.
-
This operation interacted with Uniswap’s Permit2 contract.
So the question arises: how did the address ending with fd51 get the permission to access these assets? Why is it related to Uniswap?
First of all, we need to know that in order to successfully call the Transfer From function, the caller needs to have the permission to use this token, which is called approve. I believe that those who have done operations on the chain are familiar with this. When we use some Dapps and it involves asset transfer, we need to first authorize (approve), so that the contract of the Dapp has the permission to transfer our assets.
To solve this puzzle, we need to continue digging, and the answer lies in the interaction records of the address ending with fd51. Before this address transferred Little A’s assets by calling Transfer From, we can see that this address also performed a Permit operation, and the interaction objects of these two operations are both Uniswap’s Permit2 contract. So what is this Permit function and Uniswap Permit2?

Uniswap Permit2 is a new smart contract that Uniswap launched at the end of 2022. According to the official statement, this is a token approval contract, which allows token authorization to be shared and managed in different applications, creating a more unified, cost-effective, and secure user experience.
And in the future, as more and more projects integrate with Permit2, Permit2 can achieve standardized token approvals in all applications. Permit2 will improve the user experience by reducing transaction costs and increasing the security of smart contracts.
First of all, we need to understand why Uniswap wants to launch Permit2. Let’s assume a scenario: when we want to swap on a certain Dex, the traditional way of interaction is that we need to authorize (approve) this Dex first, and then perform the swap. This usually requires us to pay two gas fees, which is too high friction cost for users. I believe many of you have had this experience.
 Image source: https://github.com/dragonfly-xyz/useful-solidity-Blockingtterns/tree/main/patterns/permit2
Image source: https://github.com/dragonfly-xyz/useful-solidity-Blockingtterns/tree/main/patterns/permit2
The release of Permit2 could change the rules of the entire Dapp ecosystem. Simply put, the traditional method requires you to authorize every interaction with a Dapp that involves asset transfer, but Permit2 can eliminate this step, which can effectively reduce user interaction costs and provide a better user experience.
The solution is that Permit2 serves as an intermediary between the user and the Dapp. Users only need to authorize Permit2 to have permission to transfer tokens. All Dapps that integrate with the Permit2 contract can share this authorized limit. For users, this reduces interaction costs and improves the user experience. For Dapps, the improvement in user experience brings more users and funds. This is a win-win situation, but at the same time, it can also be a double-edged sword, and the problem lies in the way of interacting with Permit2.
In the traditional interaction method, whether it is authorization or fund transfer, it is an on-chain interaction for the operating user. Permit2 turns the user’s operation into an off-chain signature, and all on-chain operations are completed by intermediate roles (such as the Permit2 contract and the project party that integrates Permit2), The advantage of this solution is that since the on-chain interaction role has changed from the user to the intermediate role, even if the user does not have ETH in the wallet, other tokens can be used to pay the gas fee or be fully reimbursed by the intermediate role, depending on the choice of the intermediate role.
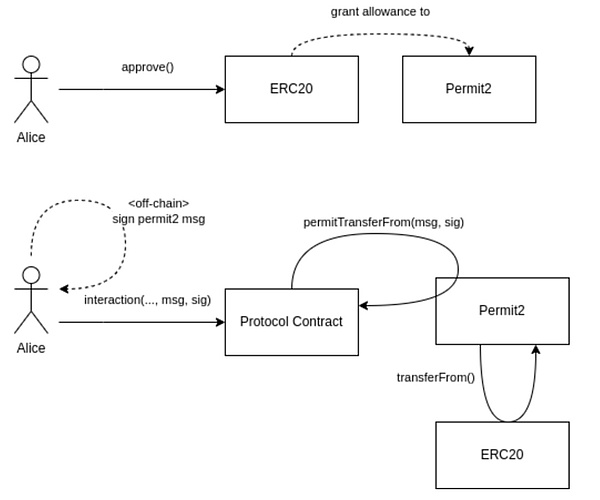 Image source: https://github.com/dragonfly-xyz/useful-solidity-Blockingtterns/tree/main/patterns/permit2
Image source: https://github.com/dragonfly-xyz/useful-solidity-Blockingtterns/tree/main/patterns/permit2
Although the emergence of Permit2 may change the rules of Dapp in the future, it can be seen that this is a very powerful double-edged sword. For users, off-chain signatures are the easiest step to put down their guard. For example, when we log in to some Dapps with a wallet, we need to sign to connect, and most people do not carefully check the content of the signature or understand the content of the signature, which is the most terrifying place.
Understanding the Permit2 contract, when we return to Xia A’s incident, we understand why assets were stolen through interaction with the Permit2 contract. Let Bo Cai reproduce this Permit2 signature phishing method. An extremely important prerequisite is that the wallet that was phished needs to have authorized tokens to the Uniswap Permit2 contract. Bo Cai found that currently, as long as you Swap on a Dapp or Uniswap integrated with Permit2, you need to authorize the Permit2 contract (Bo Cai used a security plugin in the figure below).
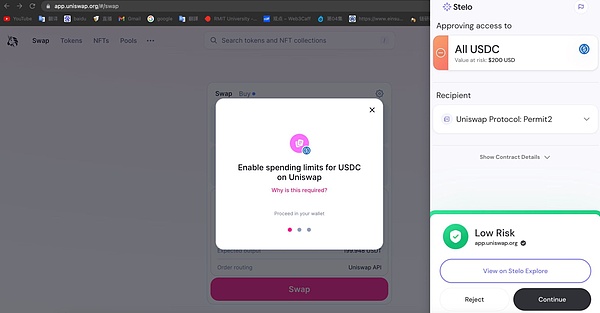
Another scary thing is that no matter how much you want to Swap, Uniswap’s Permit2 contract will default to authorizing the entire balance of that Token. Although MetaMask will allow you to customize the amount, I believe that most people will just click the maximum or default value, and Permit2’s default value is an infinite amount….


This means that as long as you have interacted with Uniswap and authorized the Permit2 contract after 2023, you will be exposed to the risk of this phishing scam.
The key point is the Permit function in the address ending in fd51, which simply uses your wallet to transfer the Token authorization you authorized to the Permit2 contract to another address. In other words, as long as the hacker gets your signature, they can get access to the permissions of the Tokens in your wallet and transfer your assets away.
Event Detailed Analysis
permit function:
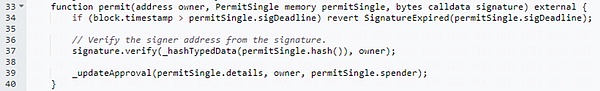
You can think of the Permit function as a way to sign contracts online. This function allows you (PermitSingle) to sign a “contract” in advance, allowing others (spender) to spend some of your tokens at some point in the future.
At the same time, you also need to provide a signature, just like signing a paper contract, to prove that this “contract” is really signed by you.
So how does this function work?
-
First, it will check whether the current time has exceeded the expiration date of your signature (sigDeadline). Just like a contract you sign has an expiration date, if the current time exceeds the expiration date, then this “contract” cannot be used anymore and the program will stop.
-
Then, it will check whether your signature is really signed by you. The program will use a special method (signature.verify) to check the signature and ensure that the signature is really signed by you and not forged by someone else.
-
Finally, if all checks pass, the program will update the record and note that you have allowed others to use some of your tokens.
The focus is mainly on the verify function and the _updateApproval function.
verify function:

As can be seen, the verify function retrieves the v, r, and s data from the signature information parameter. v, r, and s are the values of the transaction signature, which can be used to recover the address of the transaction signature. As can be seen from the code above, the contract compares the recovered address of the transaction signature with the token owner address passed in. If they are the same, the verification passes and the _updateApproval function is called. If they are different, the transaction is rolled back.
_updateApproval function:

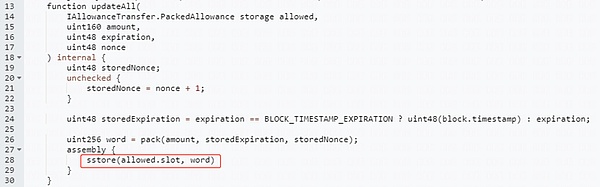
When the signature verification is passed, the _updateApproval function is called to update the authorization value, which means that your permission has been transferred. At this point, the authorized party can call the transferfrom function to transfer the token to the specified address, as shown in the code below.
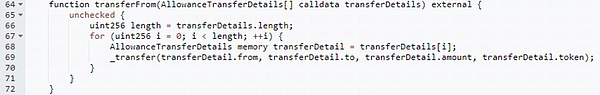

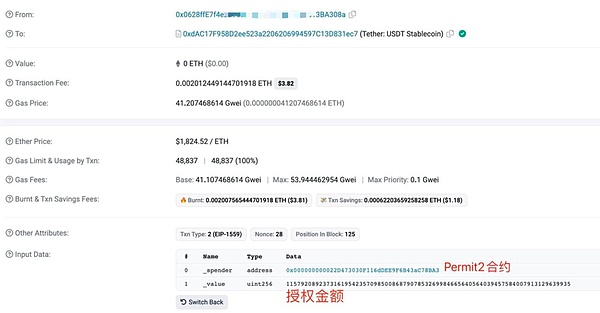
Well, after explaining the permit function, let’s take a look at the real transaction on the chain. We can see from the details of this interaction that:
owner is the wallet address of Xiaoa (ending in 308a);
Details shows the authorized Token contract address (USDT) and amount, and other information;
Spender is the hacker address ending in fd51;
sigDeadline is the validity period of the signature, and signature is Xiaoa’s signature information.

Looking back at Xiaoa’s interaction records, we can see that Xiaoa had authorized Uniswap Permit2 with almost unlimited USDT quota when using Uniswap previously.
To summarize, Xiaoa had authorized Uniswap Permit2 with almost unlimited USDT quota when using Uniswap previously, but accidentally fell into the fishing trap of the Permit2 signature designed by the hacker while performing wallet operations. After obtaining Xiaoa’s signature, the hacker used Xiaoa’s signature to perform Permit and Transfer From operations in the Permit2 contract, transferring Xiaoa’s assets away. Currently, it seems that Uniswap’s Permit2 contract has become a fishing paradise, and this Permit2 signature fishing seems to have become active only two months ago.
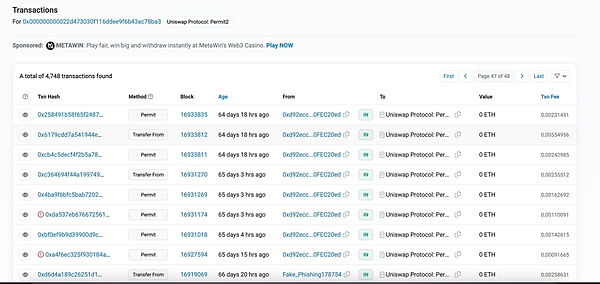 Source: https://etherscan.io/address/0x000000000022d473030f116ddee9f6b43ac78ba3
Source: https://etherscan.io/address/0x000000000022d473030f116ddee9f6b43ac78ba3
In the transaction records, it can be found that almost all of them are marked as phishing addresses (Fake_Phishing), and people keep falling for it.
 Source: https://etherscan.io/address/0x000000000022d473030f116ddee9f6b43ac78ba3
Source: https://etherscan.io/address/0x000000000022d473030f116ddee9f6b43ac78ba3
How to prevent it?
Considering that the Uniswap Permit2 contract may become more popular in the future and more projects will integrate the Permit2 contract for authorization sharing, there are effective ways to prevent it:
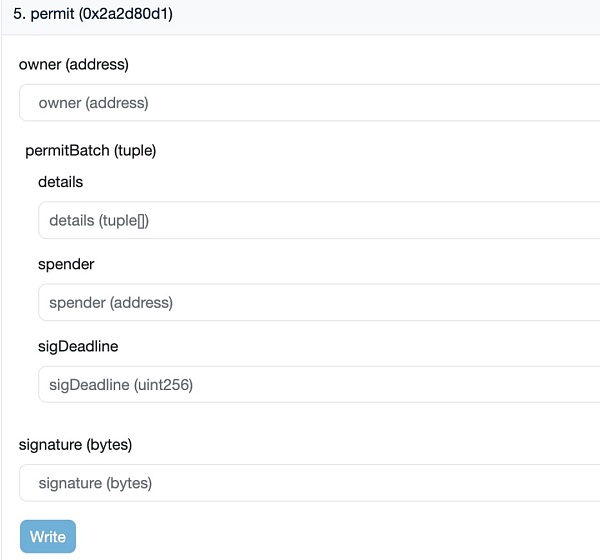
1 Understand and identify the signature content:
The signature format of Permit usually includes Owner, Spender, value, nonce, and deadline, and if you want to enjoy the convenience and low cost brought by Permit2, you must learn to identify this signature format. (Downloading a secure plug-in is a good choice)

2 Separate the wallet where assets are stored from the wallet used for interaction:
If you have a large amount of assets, it is recommended to store the assets in a cold wallet, and only store a small amount of funds in the wallet for on-chain interactions, which can greatly reduce the losses when encountering phishing scams.
3 Don’t authorize too much amount to the Permit2 contract or cancel the authorization:
When you Swap on Uniswap, only authorize the amount of money you want to interact with. Although each interaction requires re-authorization, which will incur some additional interaction costs, it can prevent signature phishing by Permit2. If you have authorized an amount, you can find the corresponding security plug-in to cancel the authorization.
4 Identify the nature of the token and whether it supports the permit function:
More and more ERC20 tokens may use this extension protocol to implement the permit function, and you need to pay attention to whether the tokens you hold support this function. If they do, you should be extra careful when trading or manipulating the tokens, and strictly check whether each unknown signature is a signature for the permit function.
5 If you are scammed and there are tokens on other platforms, you need to formulate a comprehensive rescue plan:
When you discover that you have been scammed and the tokens have been transferred out by hackers, but you still have tokens on other platforms through methods such as staking, you need to extract them and transfer them to a secure address. At this time, you need to be aware that the hacker may be monitoring your token balance at any time, as they have your signature. If tokens appear on your stolen address, the hacker can transfer them out directly. Therefore, you need to develop a perfect token recovery process. The process of extracting and transferring tokens needs to be executed together and cannot be interfered with by hackers. You can use MEV transfer, which requires some blockchain knowledge and coding skills, or you can seek professional security companies to use transaction front-running scripts to achieve it.
I believe that in the future, there may be more and more fishing based on Permit2, and this signature phishing method is extremely concealed and difficult to prevent. As the application scope of Permit2 becomes wider and wider, more addresses will be exposed to risks. I hope that after reading this article, you can spread it to more people to avoid more people being stolen.
Like what you're reading? Subscribe to our top stories.
We will continue to update Gambling Chain; if you have any questions or suggestions, please contact us!