Compiled by TechFlow
Yesterday, Vitalik and scholars from the University of Basel jointly published a paper titled “Blockchain Privacy and Regulatory Compliance: Towards a Practical Equilibrium”, which has attracted widespread attention on Twitter.
Why should we pay attention to such a paper in a sluggish market?

- Vitalik’s latest paper condenses How does Privacy Pools solve the impossible trilemma of privacy, decentralization, and compliance?
- External turmoil has not yet subsided, and internal turmoil is gradually emerging Genesis sues its parent company DCG.
- What are the real risks of a centralized sorter?
Vitalik’s thoughts and articles often influence the development direction of new narratives and technologies. In addition, well-known experts and scholars in the blockchain field have unique insights into blockchain technology and development trends.
In addition, the issues of blockchain privacy and compliance discussed in the paper are related to the future development direction and compliance path selection of the encryption industry. Finding a balance between protecting user privacy and complying with regulatory requirements is a problem that the encryption industry urgently needs to solve.
After reading the paper, we found that the Privacy Pools protocol proposed in it provides a feasible technical solution for achieving privacy and compliance compatibility. This seems to prevent the tragedy of Tornado Cash being sent to hell due to regulation from happening again.
However, the paper is more academic and technical, and it is difficult for ordinary users to understand some of the details and meanings.
Therefore, TechFlow Research Institute has interpreted and refined the paper, trying to explain the core points of the paper in plain language, which can help more people understand the important issue of privacy and compliance, as well as its technical path and possible solutions.
Who are the authors?
First of all, the paper was led by Vitalik, and professionals from academia and industry in the field of blockchain jointly participated in writing.
Vitalik acts as the first author. Due to Vitalik’s significant influence and reputation in the cryptocurrency field, it can attract more attention to the proposed solution.
Other co-authors include: Jacob Illum, a researcher at Chainalysis, a research institution in the cryptocurrency industry;
Mat Nadler, a PhD student at the University of Basel, who also has relevant development projects in DeFi and EVM;
Fabian Schär, a professor at the University of Basel, whose research focuses on public chains and DeFi protocols;
Ameen Soleimani, the founder of several well-known cryptocurrency projects, with rich practical experience.
Background: Privacy and Regulatory Contradictions, the Tragedy of Tornado Cash
-
The design of public blockchains is transparent, and anyone can verify transactions without relying on centralized third parties. But this also brings privacy issues because the blockchain records all transactions of each address, making addresses traceable and analyzable.
-
The Bitcoin whitepaper believes that blockchain can protect privacy through public key anonymity, but this protection has been proven to be insufficient, as various blockchain analysis tools can link addresses and transactions. Therefore, stronger encryption technologies are needed to enhance the privacy protection of public chains.
-
Systems that use generic zero-knowledge proofs, such as Zcash and Tornado Cash, can increase the anonymity set to cover all transactions and improve privacy protection. However, Tornado Cash has also been abused by some hackers, and its smart contract address has been sanctioned by OFAC.
Regarding the issue of Tornado Cash, Deep Tide has also provided some technical background information for readers who are not familiar with the previous regulatory sanctions:
-
Tornado Cash is a privacy-enhancing protocol based on zero-knowledge proofs that enables anonymous transactions. It allows users to deposit funds and then withdraw them to another address. On the blockchain, only the deposits and withdrawals can be seen, and the corresponding relationship between the two cannot be observed, making it anonymous.
-
However, the protocol has also been abused by some hacker organizations for money laundering. For example, there is evidence that North Korean hacker groups have used Tornado Cash for money laundering.
-
As a result, the U.S. Department of the Treasury’s Office of Foreign Assets Control (OFAC) ultimately included the smart contract address of Tornado Cash on the sanctions list. Regulatory authorities believe that the protocol facilitates money laundering and is detrimental to combating financial crimes.
-
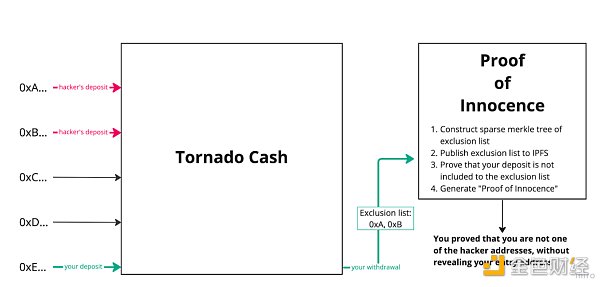
The key issue with Tornado Cash is that it is difficult for legitimate users to disassociate themselves from the criminal activities attracted by the protocol.
-
However, the creation of this proof relies on Tornado Cash’s centralized servers. Users need to provide specific information to the servers for the withdrawal, and the servers use their own databases to verify which deposit corresponds to the withdrawal and then generate the proof.
-
This reliance on centralized intermediaries means that only Tornado Cash holds the complete database and can generate the correct proof. Ordinary users cannot verify the correctness of the proof, so both users and regulators can only choose to trust.
We urgently need a way to prove and convince regulators that the source of my funds is clean and legal without exposing privacy and relying on centralization.
Therefore, this paper proposes a feasible technical solution called the Privacy Pools protocol: it allows users to prove that funds come from a customized set of associations, protecting privacy while also proving whether they come from illegal sources.
This may be the first step towards the coexistence of privacy and regulation.
zk+Association Sets: The Key to Solving the Problem
Based on the background description above, we already understand the problem that needs to be solved, which is to ensure both privacy and decentralization in order to prove that our funds are “innocent”.
When it comes to privacy, zk comes to mind. Indeed, Vitalik’s latest paper also affirms zk, especially the value of zk-SNARK in addressing privacy issues:
-
Zero-knowledge: Does not reveal private data, only proves that the statement is correct.
-
Conciseness: Proofs are short, verification is fast, and even complex computations are efficient.
However, relying solely on zk-SNARK can only solve part of the problem: proving that the transaction has occurred while hiding the transaction details.
To completely solve the problem, it is necessary to prove the legitimacy of the transaction’s source while hiding the transaction details.
Therefore, this paper connects zk with another approach – Association Sets.
-
The so-called associated set means that the user proves that the funds come from a custom set, rather than completely hiding or completely revealing the source. For example, if I transfer 1BTC, but this 1BTC is accumulated from multiple other transactions, then these other multiple transactions can be an associated set.
-
The associated set can be large or small, and users can freely determine its composition and scope. It can be a large anon set to enhance privacy, or a small set to prove compliance.
After understanding the concept of the associated set, let’s take a look at how zk+ associated sets can guarantee privacy and prove the source of funds:
-
When the user makes a deposit, using zk, a secret key is generated, and then a public coin ID is calculated. (Marking the association between me and the money)
-
When the user withdraws, they need to submit a nullifier to prove that I have used this secret key. (Proving that the money is mine)
-
Using zk technology, the user only needs to prove that my coin ID exists in both the total set and the associated set I declared. (Proving that the money is clean)
-
Externally, only the number of transactions and the ownership set of the money can be seen, but the specific information of the transfer parties cannot be obtained.
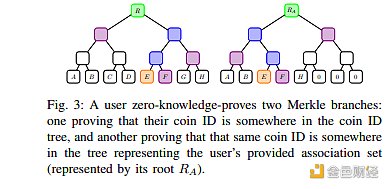
To be a little more technical, we can look at this Merkle tree diagram from the original paper. The Merkle tree in the diagram is actually a combination of Coin IDs, that is, the details of the transactions are zk’ed, and we cannot see the details, only the Coin IDs are stored in the tree structure;
The tree on the left represents all the transactions that have occurred, which may include one of my own money. Now, to prove that the source of this money is not a problem, I need the tree on the right – this represents a custom associated set of mine, which includes the association of my money with other transactions. As long as I can explain the transactions on the right, I can tell you the source of my current money.
In a broader concept, this is like a privacy pool. The associated set on the right contains the source of my money, but because it has passed zero-knowledge proof, I can prove to you that the source of the money is true without telling you the transaction details.
Actual Use Cases of Privacy Pools
The paper gives a very vivid example to demonstrate the application of Privacy Pools.
1. Background:
-
There are five users: Alice, Bob, Carl, David, and Eve.
-
The first four are honest, but Eve is a known thief.
-
Although Eve’s true identity may be unknown, the public knows that the funds received by the address labeled “Eve” have been stolen.
2. Choices and Games when users withdraw:
-
When each user withdraws, according to the method in the paper, they can choose an associated set.
-
This associated set must include their own deposits. This means that when choosing an associated set, each user cannot exclude their own deposits.
-
For Alice, Bob, Carl, and David, in order to avoid being associated with the known wrongdoer Eve, they can choose an associated set that does not include Eve. In this way, they can prove that they are not associated with Eve.
-
However, Eve faces a problem: she cannot choose an associated set that only includes herself, because this would immediately reveal that she is a wrongdoer.
-
In an attempt to hide her wrongdoing, Eve may choose an associated set that includes all five users, hoping to confuse observers;
-
However, since the other four users have chosen associated sets that do not include Eve, Eve’s attempt becomes futile because people can determine that Eve is the wrongdoer through the process of elimination.
3. Results:
-
Through the selection of associated sets, Alice, Bob, Carl, and David can prove that they have no association with the known bad actor Eve.
-
Eve cannot hide her bad behavior because her associated set includes everyone.
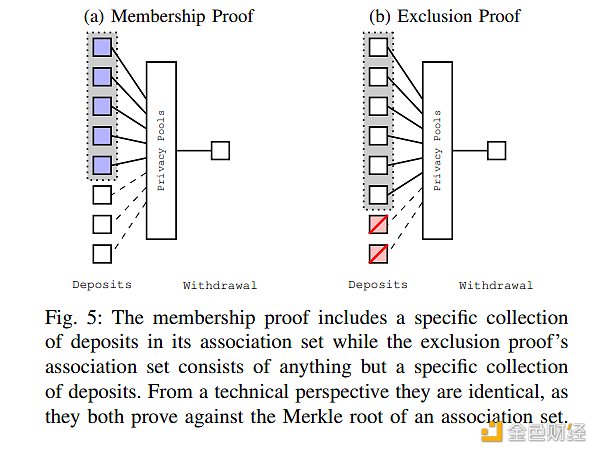
Figure 5 in the paper further illustrates the differences between these two types of proofs. A membership proof includes a specific deposit set, while an exclusion proof’s associated set includes all deposits except for a specific one.
Future Outlook
Although the privacy-enhancing protocols based on zkSNARK and associated sets mentioned above have achieved a balance between compliance and privacy in blockchain technology, there are still some technical and governance challenges. The authors propose some future directions:
-
Further research on privacy attributes: The privacy provided by these protocols depends on many different factors. The size of the associated set, the appropriateness of root selection, and user errors may allow specialized attackers to link users’ transactions.
-
Research on the separation of balance attributes: Further study the behaviors of good and bad actors under certain assumptions, and how the public proofs of the former affect the privacy of the latter.
-
Legal research: Legal experts can further study specific disclosure requirements. The suggestions proposed in this paper are highly adaptable, and insights from legal experts can help adjust the protocol and its ecosystem to ensure compliance with regulations in various jurisdictions.
Finally, we believe that at this point in time, privacy and compliance are often seen as irreconcilable opposites.
The technologies described in the paper have found a balance point between the two, bringing positive implications to the entire industry. We hope that more researchers and developers can be inspired by this technology and contribute to the health and sustainable development of the industry.
Like what you're reading? Subscribe to our top stories.
We will continue to update Gambling Chain; if you have any questions or suggestions, please contact us!