
Author: Spike @ Contributor of PermaDAO
Review: kyle @ Contributor of PermaDAO
Scanning the Security Track of the Chain: The Significance of Data Permanence in Arweave
The openness of blockchain data has created endless opportunities for data analysis. Whether it is the proactive mining of Dune and Nansen, or the rise and fall of data speculators, it indicates that data itself has tremendous economic value.
- Interpreting Decentralized Reserve Stablecoins Faced with the Impossible Trinity dilemma, what tricks are each protocol using?
- Base Chain’s 100+ ecological project landscape friend.tech leads the way, a thriving new territory for Layer2
- Friend.tech denies reports of database containing over 100,000 users being leaked.
In the face of the potential risks, how to ensure data security will also become a focus of the industry, especially when the underlying public chains are overwhelmed and are turning to L2 or centralized hosting servers. The possibility of data not being stored permanently raises doubts about its security.
In the traditional development paradigm, data is only stored on the server or with meta-computing vendors. But in the world of blockchain, everyone is responsible for data security, even ordinary users. Because damaging the credibility of data can cause a significant drop in token prices, but attackers often have a profit motive. This unequal distribution of rights and responsibilities is the fundamental cause of frequent blockchain accidents.
Therefore, the data permanence of Arweave has special significance, as it represents a never-offline server and an indestructible snapshot for the industry. This is especially underestimated in the high-security field of blockchain security.
Classification of Cryptocurrency Risks
From the perspective of the various entities involved in cryptocurrency transactions, policy regulation is considered a force majeure. The current trend is to strengthen regulatory capabilities under the premise of legalization, in order to ensure the reduction of systemic risks while promoting financial innovation.
From the perspective of the entities directly involved in cryptocurrency transactions, they can be divided into centralized institutions and on-chain assets. The latter is pure DeFi, but the asset status of centralized institutions in the entire crypto world is not clear.
The activities on the blockchain can be subjected to complete logical deduction and real-time monitoring, and can be divided into three processes: pre-emptive defense, on-chain activity tracking, and post-emergency handling. These also constitute the main sub-segments of the security field.
1. Policy regulation
2. Centralized: CEX and CeFi
3. On-chain asset security
- Pre-emptive: security audits, code security, scams
- On-chain: attacks, rugs, cross-chain bridges, MEV
- Post-emergency: money laundering, privacy coins, fiat currency deposits and withdrawals
Main Players
For CEX and CeFi, the focus of security prevention and control lies in areas such as regulation, auditing, and multi-signature wallets, in order to understand the operation principles within the black box as much as possible. The entities involved include major regulatory agencies such as SEC and CFTC, mainstream wallets such as Gnosis Safe, and recently popular asset merkle trees in exchanges.
Starting with the security of on-chain assets, there are two main methods of proactive defense: code auditing and active defense. This article uses Slowmist and BlockSec as examples to explain these methods.
The operation of on-chain funds can be further divided into wallet security and interaction control. This is because wallets have gradually become the deposit area for individual and institutional assets, and they have become the second largest asset gathering place after centralized exchanges (CEX). On-chain interaction control involves continuous data accumulation and behavior analysis of DApps and addresses to reduce security risks. This article uses WalletGuard and Go+ Security as examples to explain these methods.
Post-activity tracking refers to the remedial measures taken after on-chain activities. Overall, this is not a specific area, but a security measure that requires collaboration among project teams, exchanges, and security organizations.
In terms of product form, security products compete by focusing on “single-point functions and gradually moving towards comprehensive solutions” as a trend. They are gradually becoming integrated SaaS solutions.
- The auditing platform Certik has also launched the Skynet SaaS platform, which provides 24/7 continuous monitoring after deployment on the blockchain to defend against security threats.
- In addition to providing security auditing services before deployment on the blockchain, BlockSec also provides real-time security monitoring services for blockchain projects after deployment.
- Slowmist not only provides auditing services but also includes warning products and post-hack tracking services. It is currently the most typical all-in-one service platform in the industry.
In terms of target users, three main service methods are browser and wallet plugins, C-end users, and B-end middleware and SDK integration. It is an industry consensus that security products are “functional” products rather than directly targeting the general public.
- MetaShield and WalletGuard both focus on integrating browser or wallet plugins, striving to maintain the lowest promotion and research and development costs, and making use of existing mature product traffic.
- Exponential DeFi can assess the security of a wallet’s portfolio, helping retail investors grasp authoritative reports in the security field without understanding the technology.
- B-end SDKs or middleware, such as Go+ Security, provide reusable APIs to help applications avoid on-chain risks and maintain normal operations to the greatest extent possible.
In terms of the business models of these products, they are currently in the early stage of industry development. Code auditing is relatively mature, but the concentration of players is dispersed. On-chain activities rely on continuous label and database construction, which is time-consuming and labor-intensive. Post-activity tracking and on-chain insurance are still in the manual stage and early stages of development.
- Code auditing: Automated verification is still under development, and formal verification cannot guarantee security 100%.
- On-chain activities: Database construction is highly homogeneous, making it difficult to generate effective C-end traffic and B-end purchasing power.
- On-chain insurance: Currently, the total value locked (TVL) in the industry is less than $300 million and remains in the dark for a long time.
Market Size
The market size of the security track should be estimated based on the amount of losses and the financing amount of related projects. In the first half of 2022, the industry recorded 2 billion USD in losses and a total of 3.6 billion USD for the whole year.
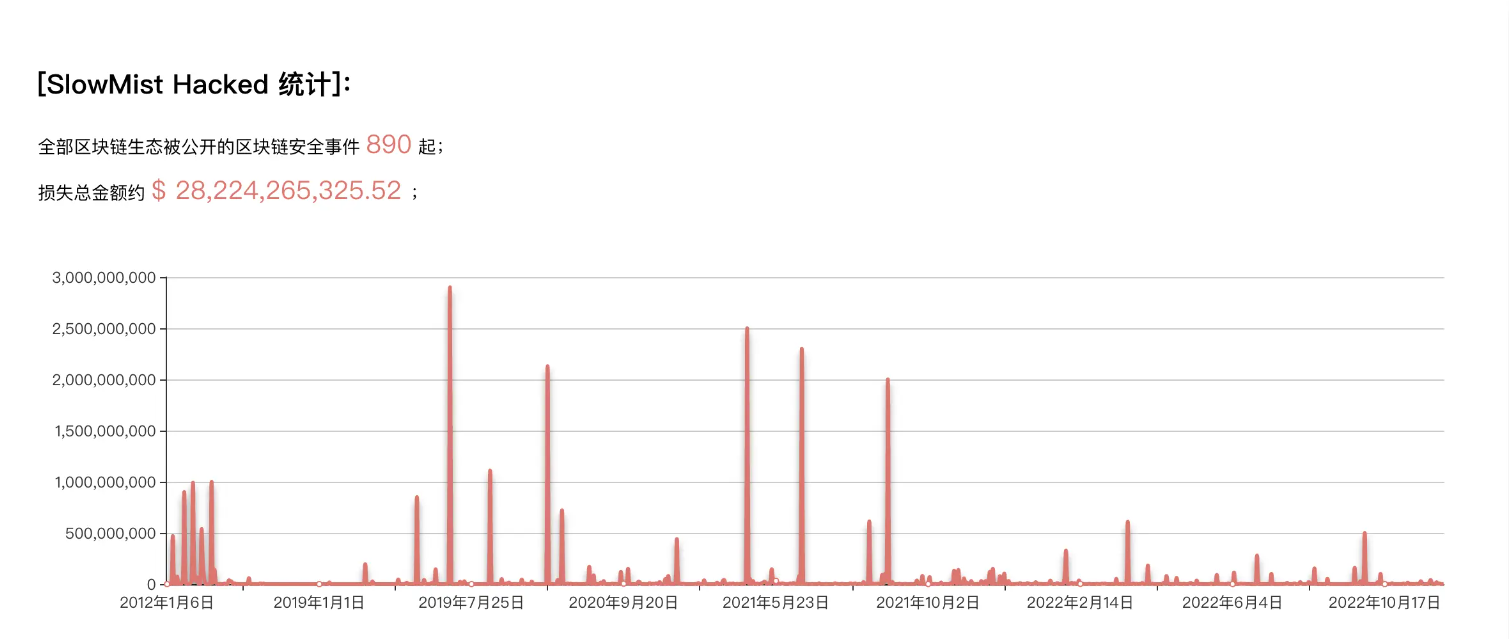
From 2016 to 2021, the figures were 900 million, 1.2 billion, 2.1 billion, 5.5 billion, 4.3 billion, and 9.7 billion USD respectively. It can be observed that it is highly correlated with the bull and bear cycles, and the overall market size can be estimated to be around 5 billion to 10 billion USD. In general, it is a “technically difficult, mainly B-end customer-oriented, relatively niche market.”
Looking at the current valuation of well-known projects, BlockSec raised 50 million RMB (about 7 million USD) in financing, and Certik raised a total of 148 million USD in 2022. It can be said that there are large financings comparable to GameFi and public chains, which can increase institutional expectations for the market size to over 10 billion USD.

However, overall, the security track is not a direct entry point for traffic, but more of a functional service scenario. Its future needs to be closely tied to the overall encrypted market to infer its market value.
Competitive Analysis
Around the core of the security track – on-chain addresses, we can compare the behavioral capabilities of major competitors based on on-chain addresses. We can understand this as a technical rating of the on-chain analysis capabilities of major competitors based on sufficient label data and accumulated time.
Competitor 1: Go+ Security
1. Number of addresses: Supports Ethereum, BSC, Polygon, Arbitrum, Avalanche, Heco, Fantom, OKC, and other public chains, supports 99,036 malicious token addresses and 6.5 million malicious addresses.
2. Product form: SaaS, providing various API development kits.
3. Main functions: Token/NFT/malicious addresses, smart contracts, signatures, dApp security, and other services.

4. Target users: B-end project parties, such as BitKeep and zkSync.
5. Charging model: Free quota limit and API special call charging model.
Competitor 2: OKLink Chain Eye 2.0
1. Number of addresses: Supports BTC, ETH, EVM-compatible chains, OKC, and other mainstream public chains, currently including 91,900 traced and analyzed addresses, 391 million address labels, and 2,500+ label types.
2. Product form: Webpage and platform.
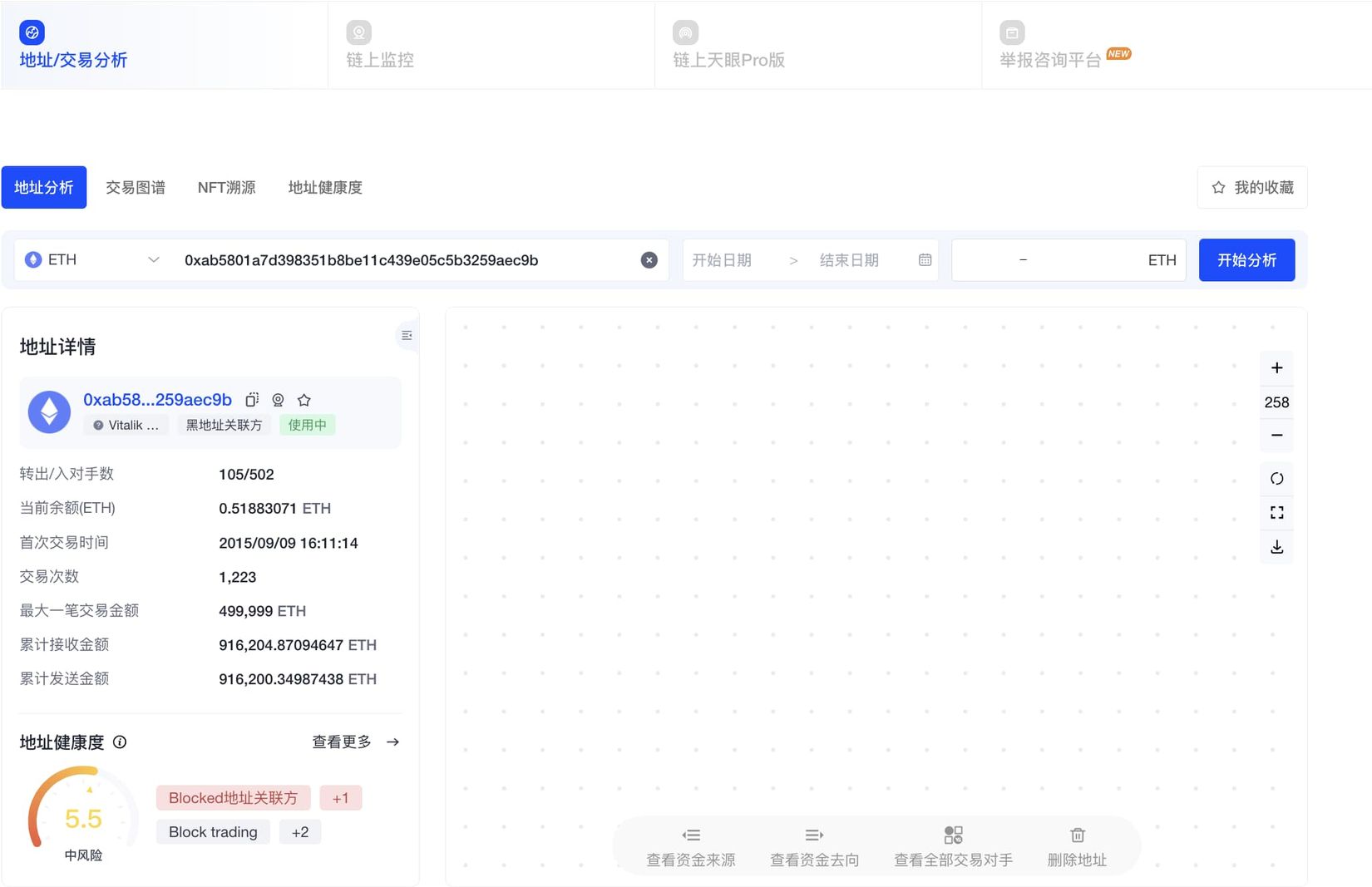
3. Main functions: Address analysis, transaction graph, NFT traceability, address health, and on-chain monitoring: exchange addresses, amount thresholds, transfers, zeroing, etc.
4. Target users: C-end + G-end (public security departments).
5. Charging model: basic operations can be done for free on the website, Pro version needs to be purchased.
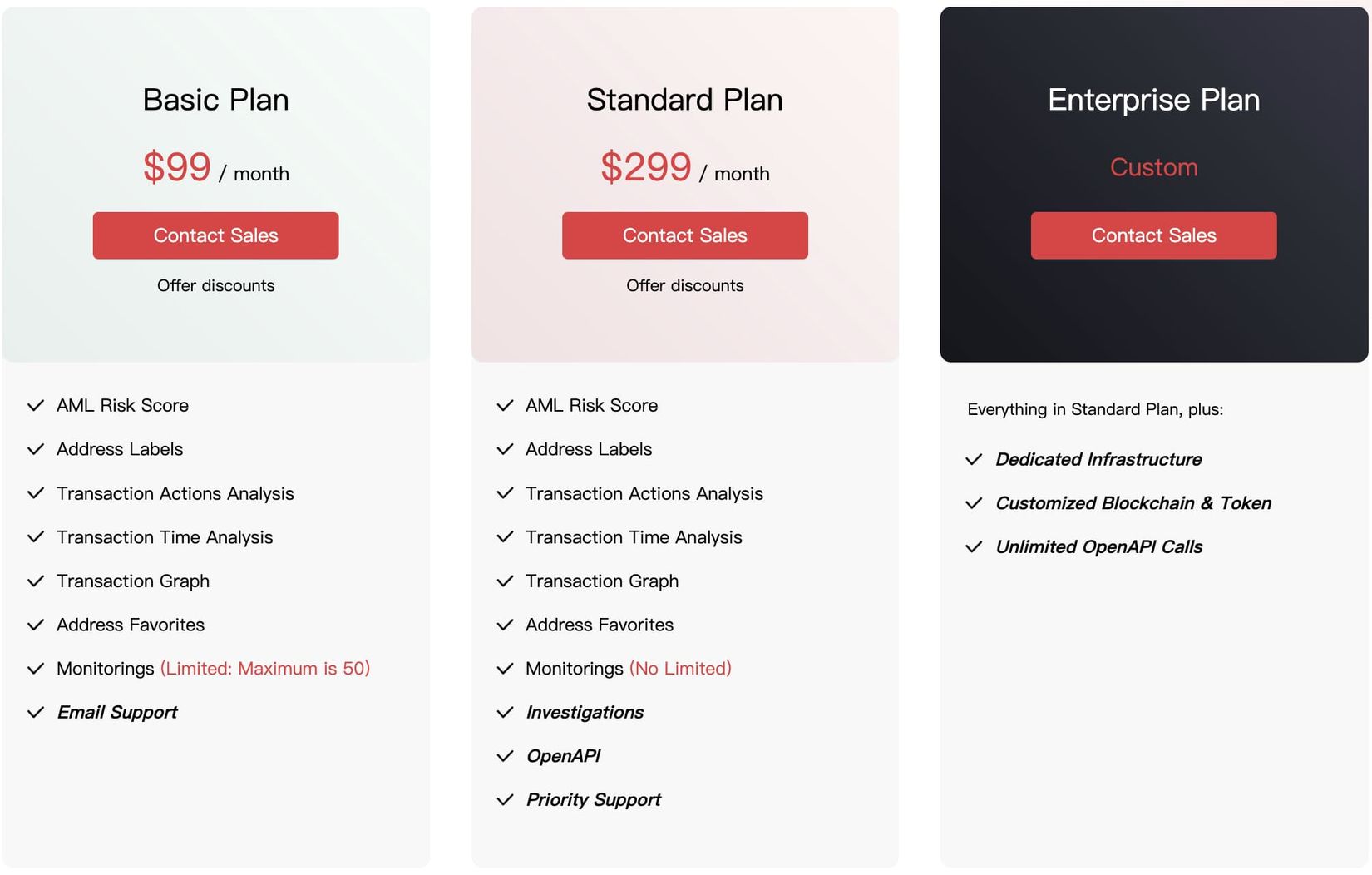
Competitor 3: Slowmist MistTrack

1. Number of addresses: supports more than 10 mainstream public chains such as BTC, ETH, EOS, XRP, TRX, including 1K+ entities, 200 million address labels, and 90 million risky addresses.
2. Product forms: website, system platform, and API.
3. Main functions: AML Risk Score, address labels, transaction analysis, time analysis, visualization, address bookmarking, monitoring and alerting, Investigations.
4. Target users: retail investors, whales, institutions, and government departments.
5. Charging model: basic package 99U/M, standard package 299U/M, commercial version customized on demand.
Competitor 4: 0xScope

1. Number of addresses: supports EVM chains such as BTC, ETH, Polygon, BSC, as well as mainstream public chains such as Solana, Cosmos, including 84 million entities, 1.4 million label types, 640,000 tokens, 5 million address behavior labels, 11,000 protocols, 17 million risky address labels, 51 million contract analyses, and 31 million transaction access data.
2. Product form: website
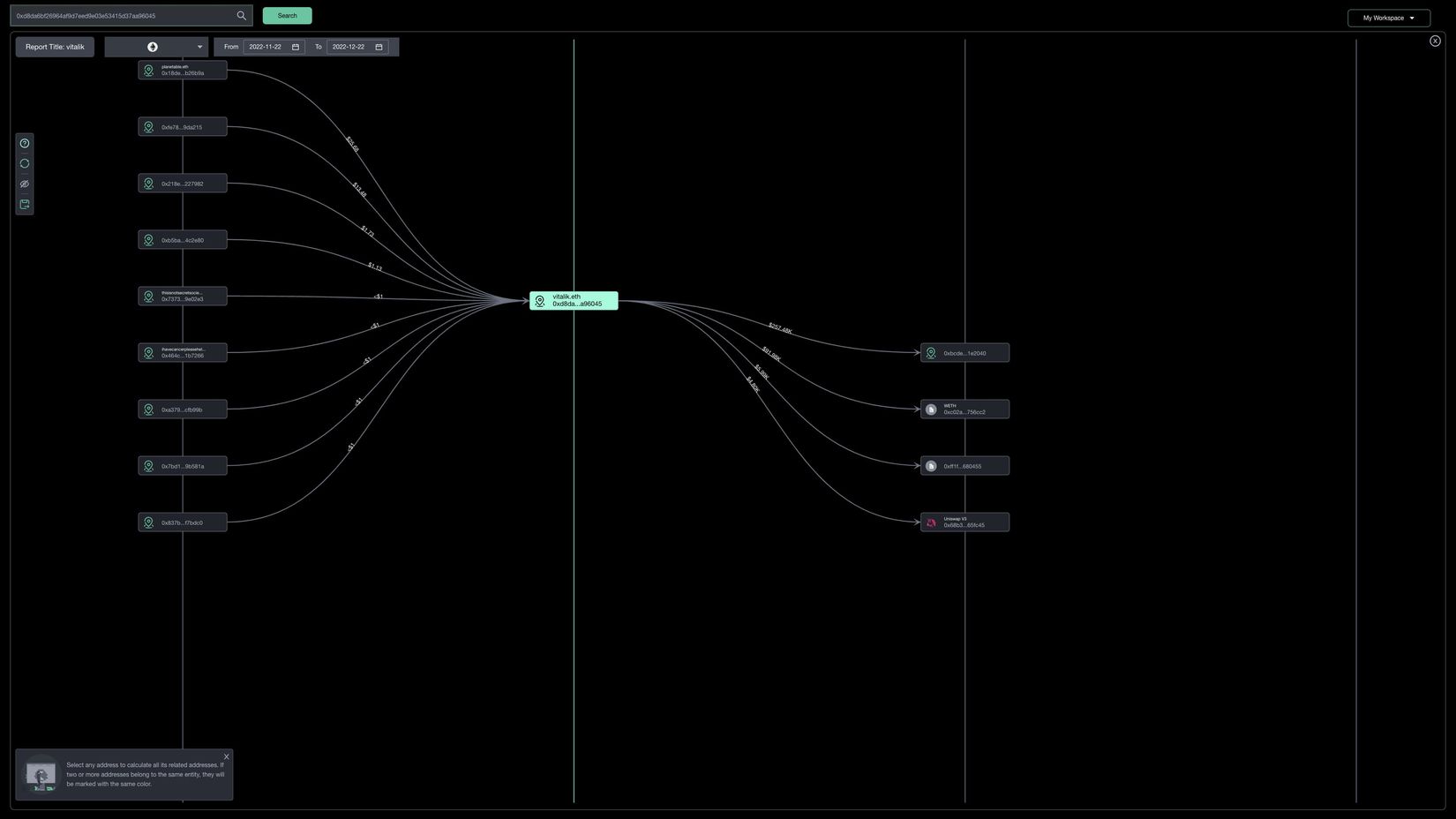
3. Main functions:
- Explorer mode: wallet analysis, token analysis, project exploration, NFT browser.
- Due-diligence mode: VC observation, whale tracking, entity discovery, entity tracking, high-risk entity identification.
- Investigations mode: address clustering, fund flow, holding address analysis, alerts.
4. Target users: free and paid users, as well as commercial solutions.
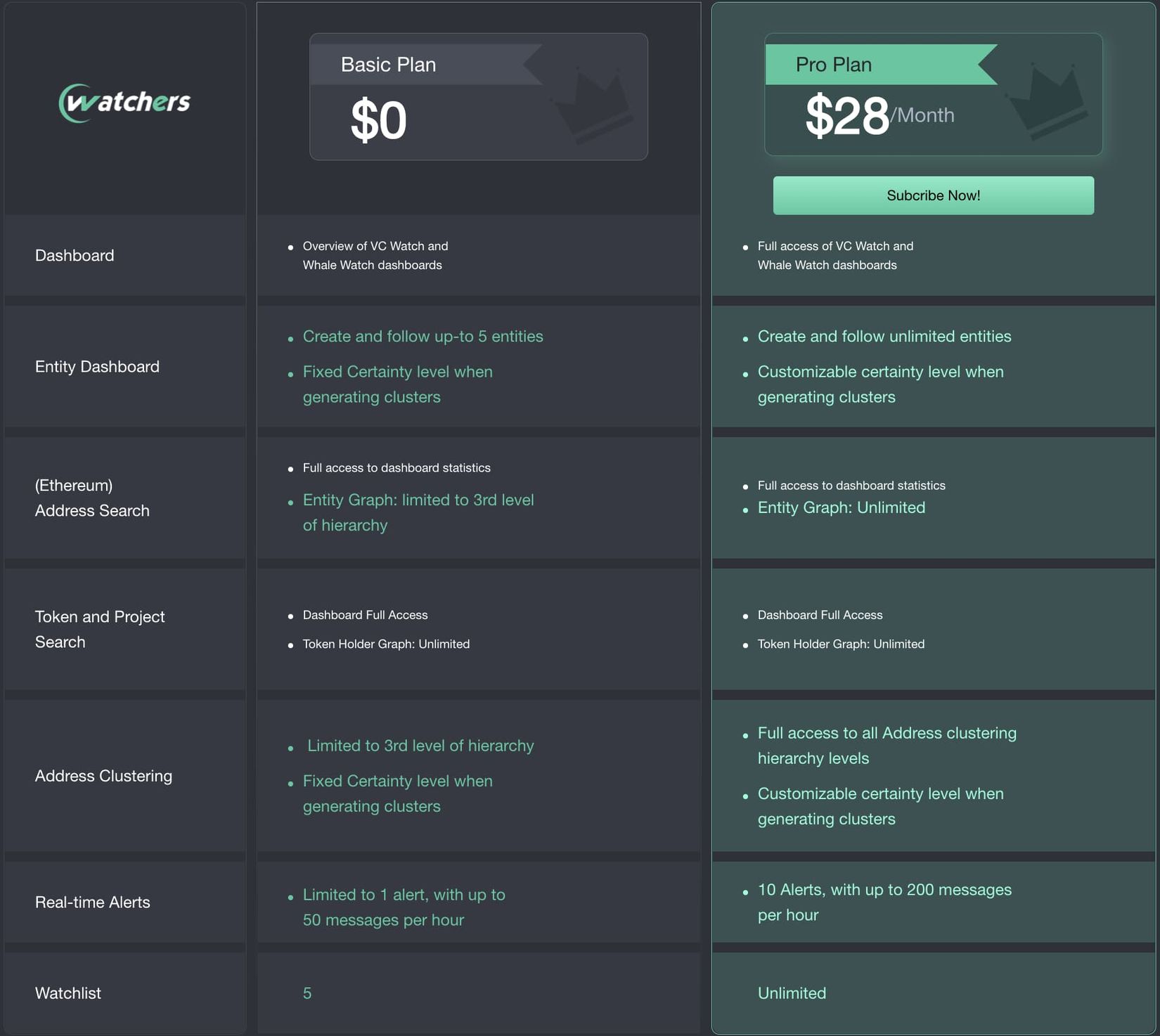
5. Charging model:
Competitor 5: TRM Labs
1. Number of addresses: supports 23 public chains, covering the majority of current public chains, and over 1 million risky address data and 80 types of risk data.
2. Product forms: all-in-one system, SaaS.
3. Main functions:
- Forensics: address and transaction tracking, support for graphical display.
- Know-Your-VASP: virtual asset service provider information query.
- Transaction monitoring: comprehensive coverage of US government prohibited addresses and entities.
4. Target users: financial institutions, crypto enterprises, government departments.
5. Charging Model: Customized according to demand.
Competitor 6: TrustCheck
1. Number of Addresses: In the millions, mainly on the Ethereum blockchain.
2. Product Form: Browser plugin and B-side solution.
3. Main Functions: Monitor address security, ensure user safety when browsing and interacting with dApps, support DeFi and NFT.
4. Target Users: C-end and B-end project parties.
5. Charging Model: Free for C-end, customized for B-end.
Competitor 7: Harpie
 1. Product Form: API, SaaS
1. Product Form: API, SaaS
2. Main Functions:
- Malicious Transaction API: Helps project parties identify malicious addresses.
- Eagle RPC Router: Wallet RPC, provides warning services similar to bank fraud notifications.
3. Target Users: B-end institutions and project parties, not individuals.
4. Charging Model: Currently priced at 0.01 ETH as a promotional offer, originally 7% for asset recovery. Subsequent commercial services need to be customized according to demand.
Competitor 8: BlowFish
1. Number of Addresses: 207 million transaction scans, 18,000 fraud protections, supports Ethereum, Polygon, and Solana.
2. Product Form: API.
3. Main Functions: Detection and protection against fraudulent addresses.
4. Target Users: Project parties, especially wallets.
5. Charging Model: B-end institutions, personal services under development.

Competitor 9: MetaShield

1. Number of Addresses: Not disclosed, currently relies on user-uploaded phishing website lists for updates.
2. Product Form: Browser plugin incubated by Buidler DAO.
3. Main Functions:
- High-risk behavior monitoring
- Blacklist and whitelist verification
- Full information transparency
4. Target Users: C-end retail investors.
5. Charging Model: Free.
Decentralized Security Track
With this in mind, we can summarize the future trends of the security track, mainly in the following three points:
1. Cross-boundary integration. It will not only cover DeFi but also asset types such as NFT, as well as comprehensive cross-chain capabilities.
2. Entity-based. Starting from on-chain addresses, it will ultimately determine the behavior of relevant entities.
3. Integration. Address behavior analysis, combined with comprehensive security data tools, and then sell the ability to discriminate, rather than the data itself.
In fact, the core competitiveness of the security track lies in the ability to store and utilize data. However, its operation process revolves around centralized service platforms or entities. It can be said that decentralized security is built on centralized recognition.
Similar to our consistent viewpoint, this situation represents the initial stage and weak state of decentralization. If we consider seamlessly migrating the data to Arweave for storage, we can effectively eliminate the monopoly of centralized institutions on data and truly unleash the organizational capacity of decentralized security.
It can be said that Dune reduces the threshold for ordinary people to access on-chain data, provided that they understand and have the ability to master SQL statements. Institutions such as SlowMist have shown through long-term practice that data can be treated as secure oil, provided that it goes through a persistent labeling process. Furthermore, the decentralization of the data itself is still in the process of historical progress.
Like what you're reading? Subscribe to our top stories.
We will continue to update Gambling Chain; if you have any questions or suggestions, please contact us!