Introduction
On June 27th, 2023, the Chibi Finance team executed an exit scam, resulting in investor funds lost exceeding $1 million. The project took advantage of centralization risk, transferring user funds out of contracts owned by Chibi and exchanging them for ETH, then cross-chain bridging to the Ethereum network and depositing into Tornado Cash. This incident was the 12th major incident found by CertiK on the Arbitrum network in 2023, resulting in a total of $14 million in funds lost, including hack attacks, scams, and exploits.
Event Summary
Although the Chibi Finance exit scam occurred on June 27th, the scam was likely carefully planned several days or even earlier. On June 15th, an external address (0xa3F1) withdrew 10 ETH from Tornado Cash, of which 2 ETH was cross-chain bridged to the Ethereum network. Four days later on June 19th, 7.8 ETH was transferred again, with most of the ETH sent to address (0x1f19). However, on June 23rd, 0.2 ETH was sent to address (0x80c1) to pay for gas fees for adding Chibi pools and creating contract (0xb612), which would later be emptied of those Chibi pools.
- Looking ahead to the upgrade of Cancun, is it worth being “optimistic” about OP?
- Is it worth being “optimistic” about the upgrade of Cancun OP?
- On-chain research: What did DAOs that received ARB airdrops do with the money?
Chibi continued to promote its project, announcing on June 26th in its Telegram group that it had been listed on Coin Gecko.
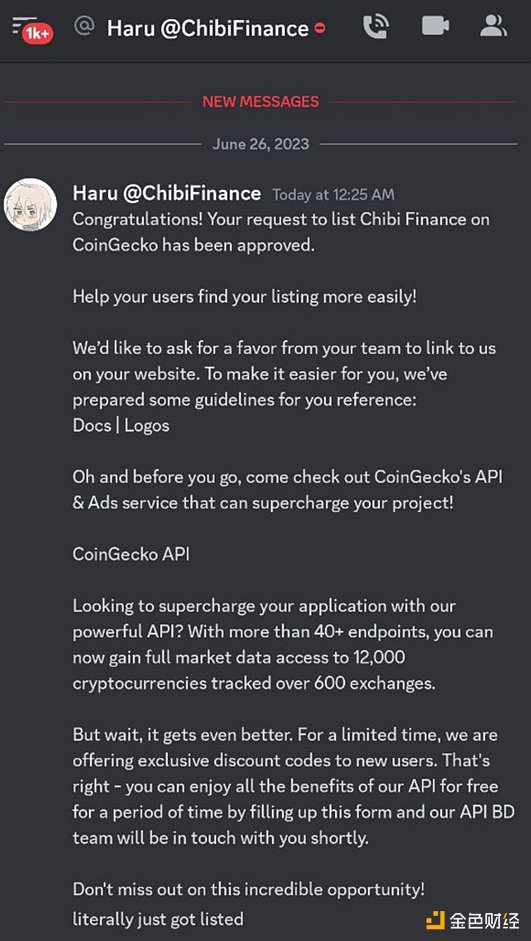
Picture: Chibi Finance Discord announcement: Source Twitter
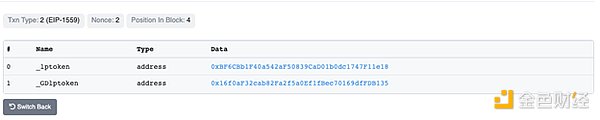
However, on June 27th, the setGov() function was called in each Chibi pool, with the gov address set to contract (0xb612). In Chibi’s contract, the gov address is equivalent to the owner address. Chibi’s functions are protected by the onlyGov role, which identifies wallets allowed to execute those functions.
Picture: setGov() transaction. Source: Arbiscan
After controlling the pools, address (0x80c1) removed liquidity totaling 539 ETH. Another 17.9 ETH was obtained from address (0x1f19), totaling 556 ETH.
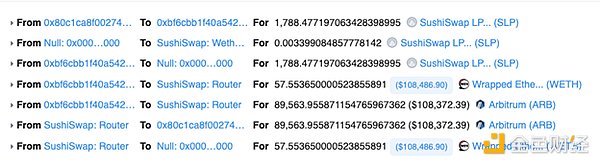
Picture: Converting stolen funds into WETH. Source: Arbiscan.
These funds were then cross-chained to Ethereum through two transactions, with 400 ETH bridged through the Multichain bridge and 156 ETH bridged through the Stargate bridge. A total of 555 ETH was deposited into Tornado Cash, with two transactions of 0.5 ETH each sent to two different EOAs. One transaction went to a new wallet (0x9297), which still holds ETH at the time of writing. The other 0.5 ETH was sent to junion.eth, who had previously sent on-chain messages to the Euler exploiters as thanks for their services.
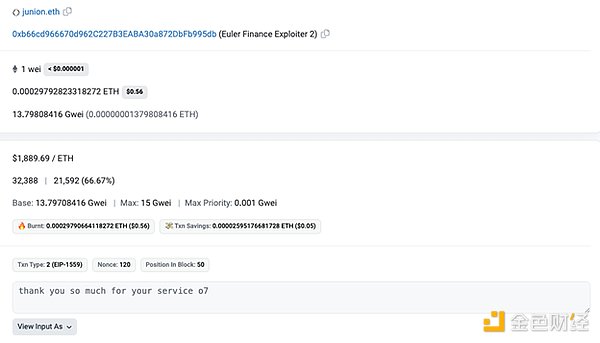
Image: On-chain message. Source: Etherscan
Attack Process
The exit scam was caused by the centralization privilege of the _gov() role in the Chibi Finance contract. The attack began on June 23, when an EOA (0x80c1) received 0.2 ETH from another EOA (0xa3F1) and created a malicious contract.

Image: Malicious contract creation. Source: Arbiscan
The next phase involved calling the addPool() function on multiple contracts owned by Chibi Finance.
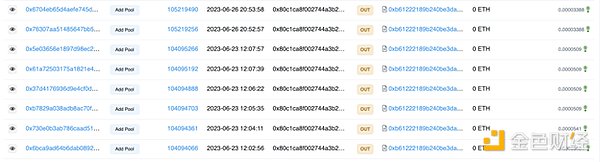
Image: Calling addPool(). Source: Arbiscan
On June 27, the deployer of the Chibi Finance contract called setGov() on multiple Chibi contracts, assigning the malicious contract created by the EOA (0x80c1) to the _gov role. This role had privileges in the Chibi Finance contract that allowed the attacker to call the Blockingnic() function and move users’ funds out of the contract.
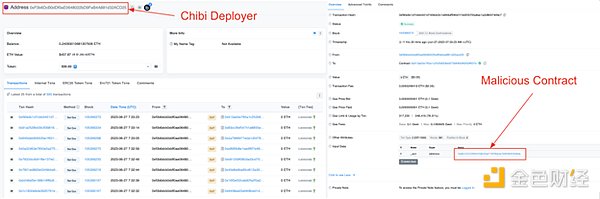
Image: setGov() transaction and example transaction. Source: Arbiscan
The EOA 0x80c1 called execute() on the malicious contract, beginning the process of extracting funds. The malicious contract went through each Chibi Finance contract that had been added on June 23 through addPool() transactions and called the Blockingnic() function, pausing the contract and extracting the funds within it.
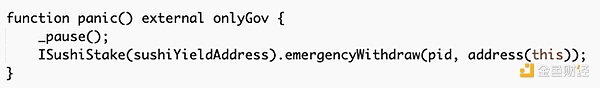
The stolen funds were then transferred to the EOA 0x80c1.
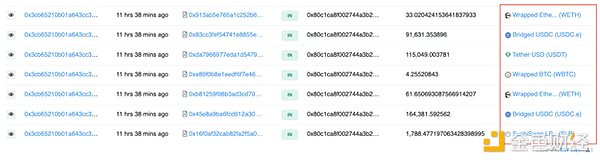
Image: Stolen funds. Source: Arbiscan
These funds were subsequently converted to WETH, transferred to the Ethereum network through a cross-chain bridge, and deposited into Tornado Cash.
Summary
So far, CertiK has recorded 12 incidents on Arbitrum in 2023, including the Chibi Finance exit scam, with total losses of $14 million. The Chibi Finance incident demonstrated the risks associated with centralization in the Web3 space. The project’s deployers abused their privileged position, stealing users’ funds, and then deleting all social media accounts, including the project’s website.
For ordinary investors, discovering and understanding centralized risks similar to those in the Chibi Finance project solely through their own research is an unrealistic expectation. This is where experienced auditors add value.
Like what you're reading? Subscribe to our top stories.
We will continue to update Gambling Chain; if you have any questions or suggestions, please contact us!