According to Beosin EagleEye, a security risk monitoring, warning, and blocking platform under blockchain security audit company Beosin, Multichain, a cross-chain bridge project, was attacked on July 6, involving approximately $126 million in funds.
Multichain was formerly known as Anyswap. Public information shows that Anyswap was founded in July 2020 and was initially positioned as a cross-chain DEX. However, based on the development of the project, Anyswap has gradually shifted its focus to asset cross-chain and weakened the trading function of DEX.

This is not the first time that Multichain has been attacked. This cross-chain project has been coveted by hackers several times before, but this attack is shrouded in mystery. According to the analysis of on-chain transaction details and transaction logs, the stolen coins in this attack did not come from contract vulnerabilities, but were full of layers of mysteries.
- LD Capital: Will the Azuki incident lead to the bankruptcy of NFT lending platforms?
- Evening Must-Read | Bitcoin is set to become the currency of artificial intelligence.
- Multichain Event Schedule Overview: 125 million assets mysteriously flowed out, cross-chain bridge temporarily suspended, previously received investment from Binance and Sequoia Capital.
Basic situation of the event
Starting at 14:21 UTC on July 6, the “hacker” began attacking the Multichain bridge and calmly transferred about $126 million in assets from Multichain: Fantom Bridge (EOA) and Multichain: Moonriver Bridge (EOA) to the following six addresses for sedimentation within three and a half hours:
0x418ed2554c010a0C63024D1Da3A93B4dc26E5bB7
0x622e5F32E9Ed5318D3A05eE2932fd3E118347bA0
0x027f1571aca57354223276722dc7b572a5b05cd8
0x9d5765aE1c95c21d4Cc3b1d5BbA71bad3b012b68
0xefeef8e968a0db92781ac7b3b7c821909ef10c88
0x48BeAD89e696Ee93B04913cB0006f35adB844537
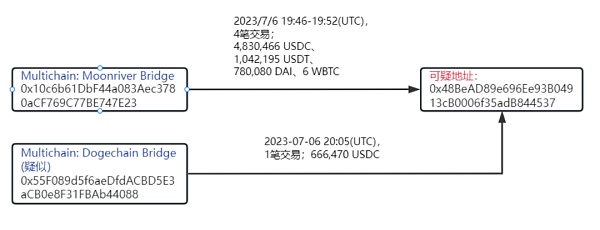
According to Beosin KYT/AML tracking, the flow of stolen funds and the time relationship are shown in the following figure:
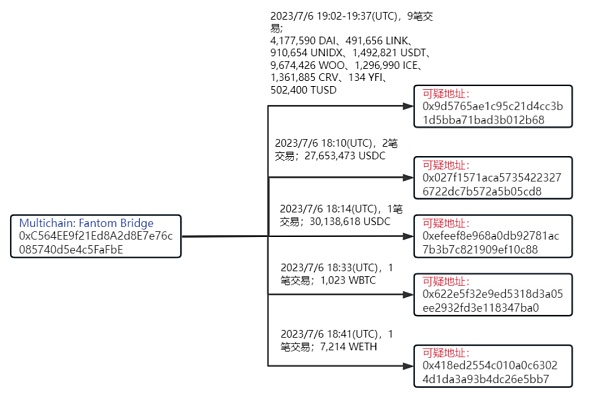
According to on-chain records, the initial suspicious transaction 0xde3eed5656263b85d43a89f1d2f6af8fde0d93e49f4642053164d773507323f8 was followed by a large amount of asset transfers, including the transfer of 4,177,590 DAI, 491,656 LINK, 910,654 UNIDX, 1,492,821 USDT, 9,674,426 WOO, 1,296,990 ICE, 1,361,885 CRV, 134 YFI, 502,400 TUSD from Multichain’s Fantom bridge to the suspicious address 0x9d57***2b68; transfer of 27,653,473 USDC to the suspicious address 0x027f***5cd8; transfer of 30,138,618 USDC to the suspicious address 0xefee***0c88; transfer of 1,023 WBTC to the suspicious address 0x622e***7ba0; transfer of 7,214 WETH to the suspicious address 0x418e***5bb7.
And transferred 4,830,466 USDC, 1,042,195 USDT, 780,080 DAI, and 6 WBTC from Multichain’s Moonriver bridge to the suspicious address 0x48Be***4537. In addition, 666,470 USDC was transferred from the suspected Multichain Dogechain bridge address 0x55F0***4088 to the suspicious address 0x48Be***4537.
Second, some suspicious parts of this security incident
According to the analysis of on-chain transaction details and transaction logs, the stolen coins in this theft did not come from contract vulnerabilities, but from account addresses, and the stolen behavior was only the most basic on-chain transfer.
Among the multiple stolen transactions, there is no common feature found, the only common point is that all transfers were made to blank addresses (there were no transactions or handling fees before the transfer), and the time interval between each transaction varied from a few minutes to more than ten minutes. The shortest time interval for transfers to the same address was one minute, which can roughly rule out that the ‘hackers’ stole coins in batches through script or program vulnerabilities.
When transferring to different addresses, the time interval is also relatively long. It is suspected that the hacker may have created the addresses temporarily when stealing coins and backed up information such as the private key. There are a total of six suspicious addresses, and 13 types of stolen coins. It is not ruled out that multiple people were involved in the entire incident.

Third, speculation on the hacker’s theft method
For the various behaviors mentioned above, we speculate that the hacker stole coins through the following methods:
1. Penetrated the background of Multichain, obtained the entire project’s permission, and transferred funds through the background to their own newly created account.
2. Through hacking the project party’s equipment, the hacker obtained the private key of the address and directly transferred funds through the private key.
3. Multichain internal operation, transferring funds and making profits through the excuse of hacker attacks. After being attacked by hackers, Multichain did not immediately transfer the remaining assets of the address, and announced the cessation of service more than ten hours later. The project party’s response speed was too slow. The hacker’s transfer behavior was also very casual, not only with large transfers, but also with small transfers of 2 USDT. The entire time span was large, and the possibility of the hacker having the private key was extremely high.
Fourth, what are the security issues facing cross-chain protocols?
Concerns about the security of cross-chain bridges were once again raised following the recent hacking of the Poly Network cross-chain bridge project, in which hackers used forged credentials to withdraw funds from cross-chain bridge contracts on multiple chains.
According to research by Beosin Security Team, cross-chain bridges face the following security challenges:
Incomplete cross-chain message verification.
When checking cross-chain data, cross-chain protocols should include contract addresses, user addresses, amounts, chain IDs, and more. For example, in the pNetwork security incident, failure to verify the contract address of an event record allowed the attacker to forge a Redeem event to withdraw funds, resulting in a total loss of approximately $13 million.
Disclosure of validator private keys.
Currently, most cross-chain bridges still rely on validators to execute cross-chain transactions. If the private key is lost, it could threaten the assets of the entire protocol. For example, the Ronin sidechain lost $600 million due to the fact that four validators and one third-party validator of Ronin were controlled by attackers using social engineering to withdraw protocol assets at will.
Signature data reuse.
This mainly refers to the reuse of withdrawal credentials to withdraw funds multiple times. For example, in the Gnosis Omni Bridge security incident, the hard-coded Chain ID allowed hackers to use the same withdrawal credentials to withdraw the corresponding locked funds on the forked ETH chain and the ETHW chain, resulting in a total loss of approximately $66 million.
Therefore, we also recommend that cross-chain project teams pay attention to security risks and conduct security audits.
Like what you're reading? Subscribe to our top stories.
We will continue to update Gambling Chain; if you have any questions or suggestions, please contact us!