Author: Climber, LianGuai
“Due to laziness, I did not complete the Galxe mission and luckily escaped the disaster.” However, under the centralized mechanism of the encryption protocol website front-end, users may escape the first day, but not necessarily the fifteenth.
On October 6th, Web3 Galxe, a credentials data network, was attacked by hackers through DNS hijacking. It is estimated that this incident has affected 1,120 users and approximately $270,000 in assets were stolen. Currently, Galxe has regained control of the domain name.
Coincidentally, similar attacks have been occurring recently. On September 20th, the DeFi liquidity protocol Balancer suffered a front-end domain attack, resulting in approximately $238,000 in losses. On the 6th of this month, the blockchain toolbox MCT was subjected to DNS hijacking, resulting in the theft of user MCT wallets. In the past, attacks on the front-end of encryption markets resulting in losses were rare, and the most discussed event was the ban on the Tornado Cash front-end.
- Helius In-Depth Explanation of the Latest Upgrade of Solana Labs Validator Client Solana v1.16 Update
- The first year of cryptocurrencies after the FTX scandal ‘Very miserable
- Interpreting the Interchain Stack’s 2024 Roadmap What Prospects of Cosmos Are Worth Anticipating?
In view of this, the Chief Information Security Officer of SlowMist stated that among the more than 6 million DNS records, 21% point to unresolved domain names. This means that users cannot access the protocol website through the domain name and can only access it through the IP address. At the same time, protocol search engine optimization (SEO) cannot develop well.
Decentralization can be achieved once the encryption protocol contract is deployed, but currently, the majority of protocol front-ends are still implemented through traditional architecture, with obvious centralization traces, making them easier targets for hackers. ZachXBT, a blockchain detective, stated that the stolen funds from Galxe and Balancer were transferred to the same address, indicating that the hacker may be the same attacker.
Compared with the volume of stolen funds in other encryption hacker attacks, the above events can only be considered minor. But perhaps a fishing layout targeting encryption users has just begun.
The unfortunate Masturbators
On the road of National Day masturbation, eating hot pot, and singing songs, they were robbed by hackers.
This is a true portrayal of many diligent masturbators during the holiday. They wanted to obtain some OAT or NFT as a voucher for obtaining large amounts of cryptocurrency in the future by participating in the Galxe mission, but they were almost completely robbed this time.
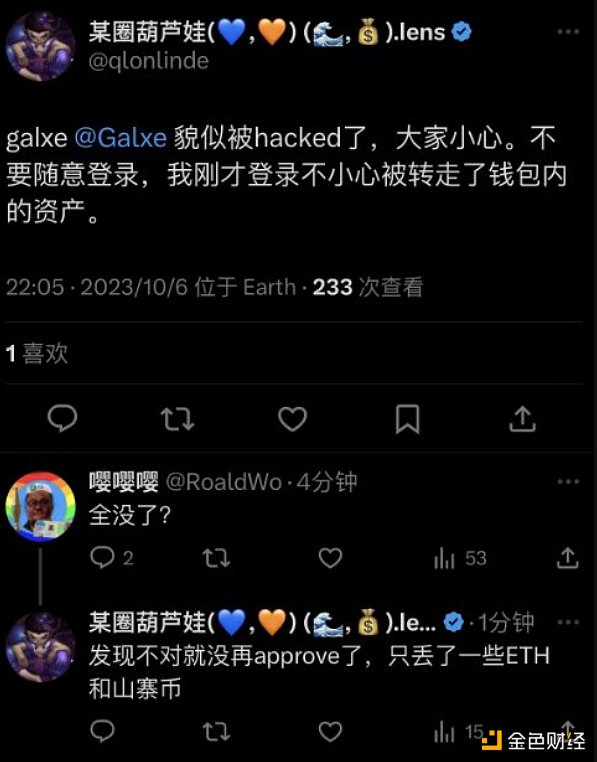
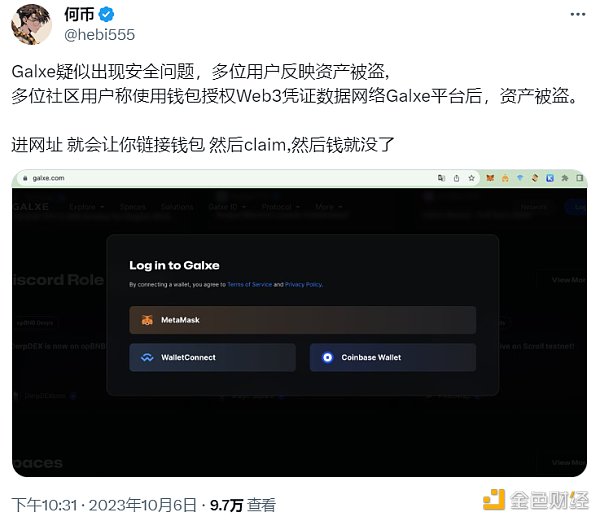
On October 6th, several community members on X stated that when they participated in the Galxe mission, they clicked on the wallet’s authorization approval, and then the assets in the wallet were transferred away. Subsequently, Galxe issued an announcement confirming that the website’s DNS was attacked by hackers.
At the same time, Galxe acted quickly and investigated the incident within one day. Regarding this DNS hijacking incident, the Galxe official stated that the hacker posed as a Galxe authorized member and contacted the domain name service provider Dynadot for support, and then reset the login credentials.
Then the impersonator provided forged documents to Dynadot, bypassing their security process and gaining unauthorized access to the domain account. Finally, they used this access permission to redirect users to a fake website and sign transactions to steal their funds.
Although Galxe stated that the incident only affected their domain name and frontend application, all Galxe smart contracts, technical systems, and user information remain secure. However, the incident still affected approximately 1,120 users, with approximately $270,000 in funds stolen.
Especially as a Web3 project participation platform, Galxe, which has been criticized by the community for its interface lagging multiple times, has once again sparked dissatisfaction among “scalpers” and further dampened the enthusiasm of new and old users to participate in the construction of cryptocurrency projects. After all, who would want to lose their principal after already spending gas fees?
Galxe is a high-traffic platform that helps build the Web3 community, with over 11 million independent users and driving the development of Optimism, Polygon, Arbitrum, and over 3,000 partners through a reward-based loyalty program.
By helping projects acquire customers conveniently, Galxe can indirectly cultivate loyal users. After users experience the project and complete tasks, they can receive corresponding digital certificates and may also receive project airdrops or rewards. In short, it is a bridge platform that benefits both project parties and users.
Similarly, this situation naturally makes it an easy target for hackers. And the recent restart of the leading L2 network Arbitrum Odyssey has once again attracted the attention of many “scalpers”.
In June last year, due to the excessive popularity of the Arbitrum Odyssey activity, a large number of users flocked to GMX, causing a surge in gas fees, even twice that of the ETH mainnet. The huge network congestion, combined with the participation of a large number of bots, forced Arbitrum to suspend the activity.
In this restart, although Arbitrum announced that there would be no form of airdrops or rewards, only custom badges, it still couldn’t resist the enthusiasm of “scalpers”. For investors who have suffered from the bear market for 7 weeks and 13 projects, it is still a kind of hope.
However, hope turned into disappointment. The centralized frontend mechanism of the Galxe website became the entry point for hackers. It only takes a DNS attack commonly seen in the Web2 world to easily capture a large number of encrypted user wallets and then steal digital assets from them.
Currently, the Galxe hacking incident is still lingering. The project official stated that some users can still see phishing websites and it will take some time to update the DNS records on the users’ local servers to resolve the issue.
DNS hijacking becomes a persistent problem in centralized frontends of encryption protocols
Previously, part of the reason for Balancer’s DNS hijacking attack was that it reduced technical costs and instead focused on marketing. In April of this year, Balancer OpCo, the service provider that provides operations and frontend development for Balancer, laid off two engineers and reduced its operating budget. At the same time, Balancer established the marketing team Orb Collective and increased its financial budget.
The weakening of the frontend technology security barrier has attracted hackers, and Balancer’s business transformation logic is also based on the cash flow pressure caused by the prolonged bear market. Among multiple choices, open source and cost-cutting are naturally the best choices, and this is also a common phenomenon in other encryption protocols at present.
Therefore, it is reasonable for SlowMist to find that 21% of the more than 6 million DNS records point to unresolved domains.
In addition, as mentioned above, encrypted contracts are decentralized, but most encrypted protocol frontends are still implemented through traditional architectures. Although web pages themselves are constantly evolving and developing, there are many potential threats in terms of domains, network services, servers, storage services, etc. and attacks on the frontend are often overlooked by developers.
Some people believe that ENS may be a solution to centralized frontend attacks on encrypted protocols, but ENS domain resolution is also “centralized”. Therefore, currently there is no good solution in the entire encrypted market.
DNS hijacking, a type of hacker attack, is extremely difficult for users to defend against. So what exactly is DNS hijacking? Why is it difficult to prevent DNS hijacking? How can users fight against DNS hijacking?
DNS is a very basic network protocol/service that allows internet users and network devices to discover websites using user-readable domain names instead of pure numeric IP addresses. Due to the huge amount of data resources in the DNS system and its inherent weak security protection capabilities, it often becomes a prime target for network attacks.
There are five common types of DNS attacks, namely DNS hijacking/redirect, DNS amplification attack, DNS/cache poisoning, DNS tunneling, and botnet reverse proxy.
DNS hijacking, also known as domain hijacking, is generally done by gaining control of DNS resolution through malicious software, cache modification, or controlling the domain management system. Then, by modifying the DNS resolution records or changing the resolution server method, users are redirected to non-established sites or illegal websites controlled by the attacker, ultimately leading to the theft of user assets.
For companies, dealing with DNS attacks can involve stricter access control, deploying zero-trust solutions, checking/verifying DNS records, etc., depending on the funding, manpower, time, and other costs the project is willing to invest.
However, for users, it is more difficult, mainly because DNS hijacking is not easily perceived by users. For users who may have been affected, they can take the following actions: use revoke.cash to cancel any unrecognized authorizations and verify if their address has been affected.
If users suspect that they may have signed malicious terms, it is best to consider that their account has been compromised, even if they have not been attacked, and transfer all funds to a new account.
Conclusion
The encrypted world is already a dark forest. Network terminals allow users to reach the world, connecting them to opportunities while hiding dangers. For ordinary investors, preserving their capital is the key to surviving the long bear market.
From the DNS hijacking incidents involving Balancer, Galxe, and MCT, it can be vaguely seen that hackers have clearly put the wallets in the hands of the vast encrypted user base on their attack list.
Like what you're reading? Subscribe to our top stories.
We will continue to update Gambling Chain; if you have any questions or suggestions, please contact us!