Project Introduction
Renegade is a blockchain-based dark pool trading platform. Unlike other unhosted decentralized exchanges, Renegade maintains complete anonymity throughout the entire trading process. It achieves peer-to-peer order matching through secure multi-party computation and settles transactions atomically using zero-knowledge proofs (referring to completing all the operations and steps of a transaction in one go, without intermediate states). This design aims to prevent front-running, sandwich attacks, and copycat trading to avoid price slippage in DeFi.
Author
Elma Ruan, a senior investment researcher at WJB, holds dual master’s degrees in market/finance from Ivy League universities and has 5 years of experience in WEB3, specializing in DeFi, NFT, and other sectors. Prior to entering the crypto industry, she worked as an investment manager at a large securities firm.
1. Research Points
1.1 Core Investment Logic
This project aims to establish a dark pool exchange primarily catering to whales and large traders for high-value transactions by high net worth individuals and institutions. Users can consider it as a private exchange designed to protect their privacy. These users do not want others to know about their fund flows or be traced by other traders for their trading activities. Approximately 30-40% of trades in the traditional US stock market are conducted in dark pools. The project’s goal is to prevent unfair practices such as front-running or sniping trades and maintain market fairness by protecting the interests of users. High-frequency trading firms often take advantage of special order types and hardware/software superior to large institutions/banks to front-run positions ahead of other traders and then sell them to large institutional traders for profits. By establishing a dark pool exchange, this project offers a more private and secure trading environment, allowing users to better protect the confidentiality of their trading activities.
Unlike traditional dark pools, this project is an on-chain exchange and adopts technologies such as Commit-Reveal Schemes, MPC (Multi-Party Computation), and ZK-SNARK to hide order transactions and achieve privacy protection goals. The project team is also technical experts, and with the continuous development of ZK-SNARK technology, Vitalik believes that ZK-SNARK will be as important as blockchain technology in the next 10-20 years. The project has a strong grasp of privacy and fund security and has gained much anticipation from many people, hoping that this technology can be truly applied in practice.
- Mantle Deep Research Report Can BitDAO’s new Layer2, incubated with modular technology and a solid foundation, stand out?
- Meta releases Code Llama an open-source AI code generation model
- Tornado Cash incident sparks heated discussion should the developer of the encryption technology be held responsible for its use in criminal activities?
Another feature of the Renegade exchange is the absence of an on-chain oracle. The price is determined by various full nodes and directly transmitted from the APIs of centralized exchanges such as Binance, Coinbase, and Uniswap. Renegade avoids the presence of market makers by directly matching buyers and sellers. This avoids issues such as price impact or slippage.
However, it is worth noting that the essence of blockchain is to build a publicly transparent ledger. When transactions are hidden, on-chain transactions lose their meaning and may attract the attention of privacy regulatory authorities. This may involve compliance issues such as money laundering, thereby limiting the development of the project.
In addition, dark pool exchanges have been around for some time, but after experiencing bull and bear markets, many projects have almost disappeared or cannot continue to develop. Therefore, the revived track must have corresponding strength to stand firm, otherwise it will only repeat the mistakes of BlackOcean. In addition to the dark pool track, the data track is also gaining more attention, such as data privacy projects like Arkham. This will bring technological pressure to the project parties, as they not only face competition from peers, but also face data tracking from other on-chain projects.
In summary, the development of Renegade exchange is influenced by many factors, including market liquidity, technology, compliance, and competitive pressure. Although the project has not yet launched its public testnet, it is unable to effectively evaluate its trading smoothness and whether it meets user expectations. However, it aligns with the overall trend of the industry, where high net worth individuals hold the majority of funds in the market and have a high demand for privacy. If the project can attract a sufficient user base, it will be able to aggregate the majority of funds in the market and achieve better development. However, as the project has not yet launched, there are still risks involved in investing, so it is recommended to observe carefully for a period of time and consider it as a medium-term investment project.
1.2 Valuation
Currently, the project has not launched on the public testnet, and there is no specific token economic model and track target as reference. Therefore, it is temporarily unable to be valued.
2. Project Overview
2.1 Past Development and Roadmap
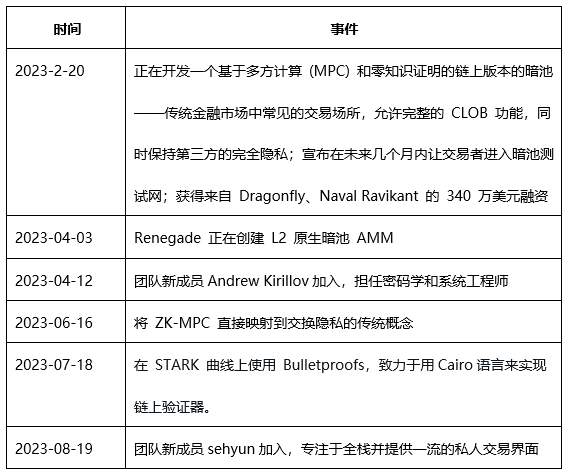
Roadmap:
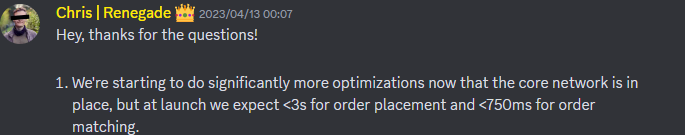
The original plan was to launch the public testnet in the second quarter of 2023, but it is currently in the third quarter and the progress of the launch has been delayed. On DISCORD, founder Chris stated that the core network has been successfully established and a lot of optimization work is being carried out. In the launch phase, Renegade expects the response time for placing orders after the launch to be less than 3 seconds, and the response time for order matching to be less than 750 milliseconds. Renegade is committed to launching the public testnet as soon as possible to provide a more efficient trading experience.
2.2 Team Situation
2.2.1 Overall Situation
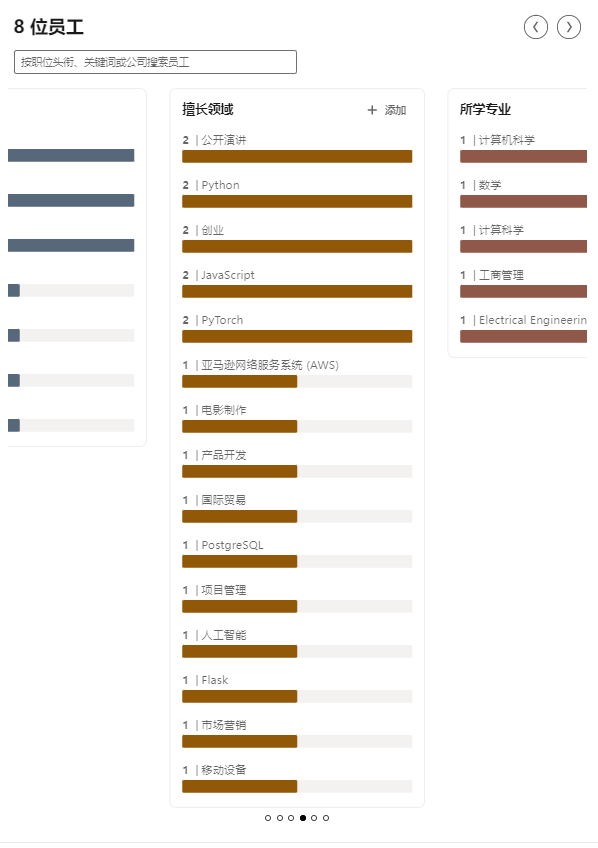
According to linkedin.com, Renegade has 8 members, covering fields such as electrical engineering, computer science, and business administration. The team members are skilled in Python, JavaScript, PyTorch, AWS, product development, artificial intelligence, etc. In addition, the project is still actively recruiting talents such as system/cryptography engineers, interface designers, and technicians on its official Twitter.
2.2.2 Founders
Christopher Bender, Founder

Christopher Bender holds dual degrees in pure mathematics and computer science from UC Berkeley. He has solid programming skills and is proficient in tools such as Python, PyTorch, and TensorFlow. Through internships at companies such as Tesla Autopilot, Datu, and Nuro, he has gained extensive experience in machine learning and deep learning. As the former chair of Machine Learning at Berkeley, he has also participated in multiple research projects and presented research findings at international conferences.
2.2.3 Core Members
Like most new fundraising projects, Renegade’s website only provides some basic initial information.
- Joey Kraut, Co-founder
- Andrew Kirillov, Cryptography and Systems Engineer
- Sehyun, Focuses on full-stack and provides a top-notch private trading interface
2.3 Funding Situation
Renegade announced on February 20, 2023, that it has raised $3.4 million in funding led by Dragonfly and Naval Ravikant. This funding has also received support from other investment institutions, including Dragonfly, Balaji Srinivasan, Tarun Chitra, Marc Bhargava, Lev Livnev, etc.

3. Business Analysis
3.1 Target Users
In the current DeFi system where various information leaks exist, many different types of traders can obtain price improvement through Renegade:
1) Market Makers: If one market maker holds a long position in an asset while another market maker holds a short position in the same asset, these two counterparties can anonymously offset the positions, balance the holdings, without the need for trading in the public spread.
2) OTC Traders: Instead of trading against the spread of an OTC exchange, traders can directly trade with counterparties at the mid-price.
3) AMM Traders: When conducting a transaction that involves transferring $5,000 or more assets using decentralized exchanges, traders usually suffer from price impact, become targets of MEV searchers, and incur losses due to cross-exchange arbitrage. However, by using Renegade, transactions can always be executed at the mid-price, reducing the risks of sandwich attacks and arbitrage, and protecting the interests of traders. Users can trade with confidence on Renegade and have a more stable and fair trading experience.
4) Privacy-focused Native Digitals: Renegade is completely anonymous, meaning no third party can see any detailed information about transaction or payment history.
3.2 Business Categories
The main business of the Renegade project is to establish and operate a privacy exchange. A privacy exchange is a transaction platform that operates on the blockchain and provides users with anonymized transaction and fund transfer functions. Compared to traditional exchanges, privacy exchanges focus on user privacy protection and provide higher security and anonymity.
3.3 Business Description
The core difference between Renegade and all other exchanges (centralized and decentralized) is that the state is stored locally. Instead of balances and orders being maintained by a central server (e.g., Binance) or thousands of distributed servers (e.g., Uniswap), all Renegade states are maintained by individual traders.
When a trader wants to perform an action on their wallet, they need to send three pieces of information to the smart contract. These pieces of information include a commitment to the new wallet, two invalidators for the trader’s old wallet (used to prevent double spending), and a zero-knowledge proof.
1. Dark Pool
In traditional financial market structures, “dark pool” trading refers to off-exchange, non-public trades that account for 30-40% of stock trading volume. Essentially, dark pools function similarly to more familiar stock exchanges like the New York Stock Exchange (NYSE) or NASDAQ. Users can deposit funds into the dark pool, submit and cancel orders, and know when their outstanding orders match with other traders.
In general, dark pool trading has one core difference from public trading: in a dark pool, the order book is not publicly visible, meaning individual traders can only see their own orders and the matching status of those orders. Dark pool traders cannot see the outstanding orders of other traders.
Because dark pools hide the order book, they often become popular trading venues for large “whale” traders who want to transfer large assets without attracting attention from the entire market. The benefit of hiding the order book is simple microeconomic reasoning: if a trader reveals too many details about their trading strategy, others can exploit that information. For example, if a market maker sees a large sell order for an asset, the market will push the price down, resulting in a lower execution price for users with large trade volumes.
In the cryptocurrency field, dark pools also have similar advantages. By hiding the order book, traders can prevent other traders or bots from hedging or manipulating the market based on order information, obtaining more favorable trading prices and execution results. In addition, for institutional investors conducting large-scale trades, using dark pools can minimize market impact, reduce trading costs, and mitigate the influence of market volatility on trade outcomes, allowing for more efficient bulk trading.
Dark Pools in the Cryptocurrency Industry
Traditional public order books are usually not the most ideal environment for traders, especially for large-scale traders who move significant orders. However, in decentralized cryptocurrency exchanges, this problem is even more severe for large-scale traders.
Currently, decentralized exchanges in the market not only leak the current state of the order book but also leak all possible states. Past states can be obtained through querying archival nodes, the current state can be seen by any lightweight client or RPC node, and even future states can be estimated by observing the mempool. This makes traders’ trading strategies and intentions easily analyzable and exploitable by others.
This situation makes large traders more inclined to execute orders in dark pools to protect their trading strategies and privacy. Dark pools hide the details of the order book, preventing others from accessing detailed information about the trades and protecting the interests of the traders. At the same time, dark pools can also reduce market impact and trading costs, allowing large traders to conduct large-volume trades more effectively.
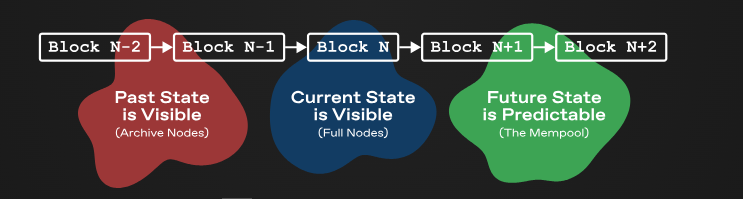
Because the status of other exchanges is always public, this exposes traders to more severe information leakage, ultimately resulting in less ideal execution prices:
Pre-trade Quote Fading: Similar to public exchanges in traditional finance, if a large non-market order is placed on the order book, all other traders can see the large buy or sell order, causing the price to be exaggerated or suppressed when the order is taken away from the large traders.
Atomic MEV (Miner Extractable Value): Block producers have the right to arbitrarily reorder, insert, and review transactions, and miners can maximize profits by adjusting or inserting the order of unconfirmed transactions to take advantage of price changes.
Copy-Trading: Anyone can see the token balance of any wallet, making it particularly easy to follow trades.
Counterparty Discrimination: Because the past transactions of any wallet address are visible, market makers can offer worse quotes (or even refuse to execute trades) to complex and potentially risky counterparties.
Statistical Arbitrage: Since the identity of each trader is visible, it is easier to identify statistical patterns of each trader’s strategies and profitability. Commonly used for strategies such as TWAP (Time-Weighted Average Price) trading, which spread large orders over a period of time.
Renegade uses Multi-Party Computation (MPC) to determine order matching and uses Zero-Knowledge Proofs (ZKP) to settle matched orders. Renegade maintains end-to-end privacy before and after orders are executed on-chain.
2. MPC (Multi-Party Computation) Protocol
Multi-Party Computation (MPC) is a core cryptographic primitive that has been researched since the early 1980s but has been rarely used in the DeFi field before Renegade.
To better understand MPC, it is best to compare it with the “ideal functionality” that MPC achieves. In this setting, multiple parties send some private data to a trusted evaluator. Once the evaluator receives all the private data, it performs calculations on these data and sends the computed results to all parties involved.
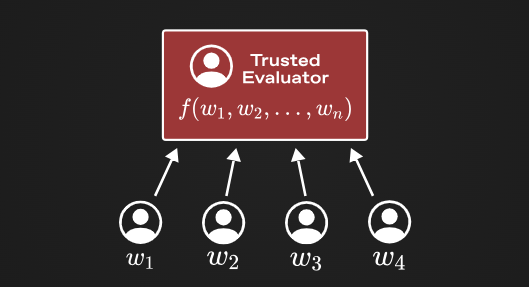
It is important to note that the evaluator only provides results without revealing the private input information, and also does not retain any relevant data of private input after the evaluation is completed. This allows for the computation of a function without the need to make the input public to everyone.
For example, two participants each hold two private numbers, and through the evaluator, the relative size of these two private numbers can be computed, and the evaluator will output a bit to indicate whose input is larger. This is the “ideal functionality” in secure multiparty computation.
The core idea of Multiparty Computation (MPC) protocol is that it allows users to achieve the above functionality without the need for trust in a central party. In other words, MPC allows multiple mutually untrusted participants to compute a function output on secret input data.
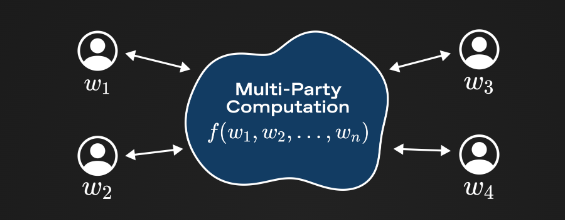
There are two main types of MPC algorithms: “garbled circuits” and “secret-sharing” algorithms. Secret-sharing methods are usually easier to understand, and “partially homomorphic” MPC computation is performed on individual private inputs using Shamir secret sharing (which means that the computation can be partially performed on encrypted or split data, obtaining partial results without decrypting or merging the data). Understanding how MPC works at the protocol level is beyond the scope of this document, but one relatively easy-to-understand secret-sharing MPC protocol is BGW.
Using MPC
In the context of dark pools, using MPC is natural: private inputs are the individual order books of each trader, and the output of MPC is a list of any tokens exchanged after executing the order book matching engine.
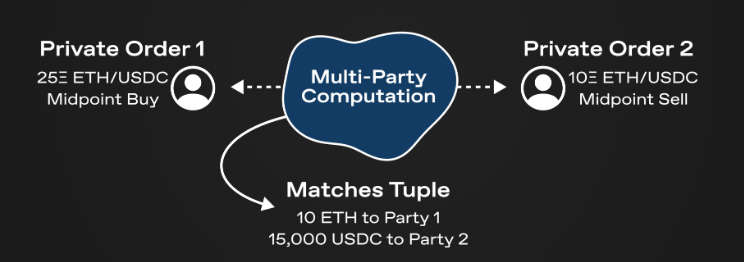
It should be noted that with the use of MPC, two traders can match their orders anonymously. Traders never need to disclose their orders in plaintext, and if there is no match between the order books of two traders, no information will be leaked (except for the fact that there are no valid counterpart orders).
However, the MPC algorithm itself does not provide any guarantees about the validity of inputs from each trading party. This would be a huge problem for dark pools, as Renegade must ensure that each trader actually has the appropriate balance for each of their orders. In the “MPC-ZKP Architecture” section, users will see how the idea of MPC is combined with zero-knowledge proofs to prove the consistency of balances and orders with the on-chain state.
3. The MPC-ZKP Architecture
The most fundamental difference between Renegade and other exchanges (whether centralized or decentralized) is that its state is locally maintained. Unlike the way balances and orders are maintained by centralized servers (e.g., Binance) or distributed across thousands of distributed servers (e.g., Uniswap), all states of Renegade are maintained by individual traders themselves.
Some terminology:
– A wallet is the order and balance list of each trader. Each trader’s wallet is private, and only the wallet hash (technically called “commitment with hiding and binding”) will be published on the chain.
– A relayer is a node in the Renegade network. Each relayer is responsible for managing one or more wallets (meaning they can view unencrypted wallets) and for conducting multi-party computations (MPC) with other relayers.
– A cluster (or “relayer cluster”) is a group of relayers that logically manage the same wallets. Clusters are fault-tolerant and redundant groups of relayers that can achieve automatic failover and parallel multi-party computations.
As mentioned earlier, individual wallets are never publicly revealed. Traders will publish the “commitments” of wallets on the chain, where wallet commitments are actually combinations of wallets and some randomness of hashes. Knowing only the commitment of a wallet does not reveal any information about the underlying wallet data to others.
Commit-Reveal Scheme:
When a trader wants to perform an operation on their wallet (such as depositing tokens, settling transactions, etc.), they must know the old wallet and the new wallet, and send three pieces of information to the smart contract:
1) The commitment of the new wallet.
2) Two nullifiers of the old wallet, used to prevent double spending of the old wallet.
3) Zero-knowledge proofs: the commitment is correctly calculated, the nullifiers are correctly calculated, the old commitment exists in the global Merkle tree, and the change from the old wallet to the new wallet is valid (e.g., the user did not arbitrarily increase the balance).
The smart contract maintains a global Merkle tree of all previous commitments, as well as a set of nullifiers used to reveal previous wallets.
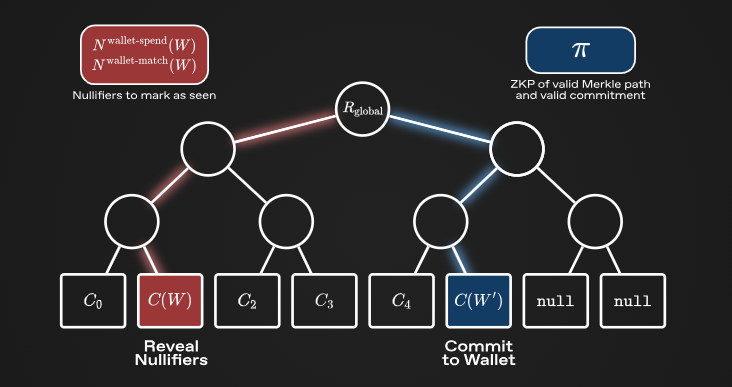
By using the Commit-Reveal Scheme, Renegade can achieve complete wallet privacy (i.e., not leaking any information about wallets on the chain), while maintaining comprehensive state consistency and preventing double spending attacks.
Network Architecture
Fundamentally, Renegade is composed of a p2p gossip network consisting of many independent relayers that continuously connect and perform multi-party secure computations as new orders enter the system. Relayers never custody assets and are only granted viewing access to wallets for peer-to-peer secure computations.
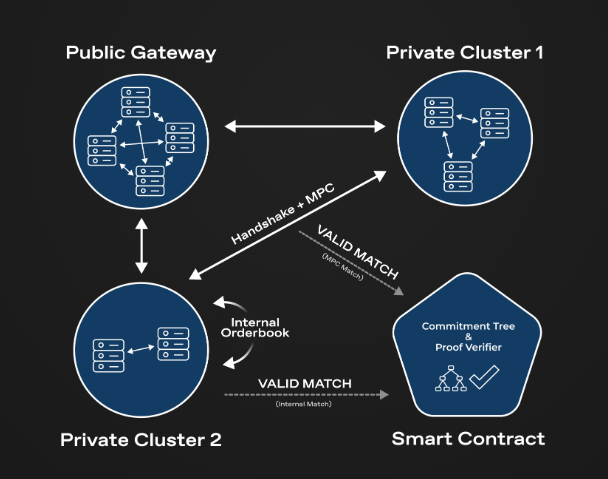
In the above diagram, there are three independent relayer clusters: Public Gateway, Private Cluster (1), and Private Cluster (2). The Public Gateway is a large publicly accessible cluster for those who do not want to run their own nodes, but it is just like other clusters, a relayer cluster (i.e., no special privileges).
When a new order is input into a wallet managed by one of the clusters, the cluster will propagate a tuple (containing the order data commitment and the proof of the order’s validity) which includes the commitment of the order data and a zero-knowledge proof that proves the validity of the order. All other relayers monitor for new tuples, and if a new tuple is detected, they will contact the origin cluster and begin secure multi-party computations (MPC).
Execution of MPC calculation matching engine. In other words, given two orders (held privately by different relays), both parties will calculate an MPC that implements the matching engine execution for these two orders. This achieves complete anonymity because no information about the orders is leaked before the MPC. After the MPC, both parties will only know which tokens have been exchanged; if there is no match between the orders, no other information will be leaked.
Please note that the dark pool track refers to a way of protecting transaction information and privacy in transactions where the parties involved remain anonymous to each other, and order matching is achieved through secure multi-party computation.
Cooperative SNARK
As mentioned earlier in what is MPC, the secure multi-party computation protocol itself does not guarantee the validity of the input data. To address this issue, the commitment of the order data is recomputed within the MPC. If the recomputed commitment is inconsistent with the publicly known commitment in the tuple, the output matching list will be set to zero to prevent fraudulent operations on the orders.
In addition to the input consistency issue, a simple application of MPC would result in atomic settlement issues. In particular, Renegade must ensure that the output of the MPC is not publicly available before the transaction matching is recorded on the blockchain. If either party can learn the output of the MPC and interrupt the connection before the actual token exchange, the protocol will leak order information.
To address this atomic settlement issue, Renegade uses the cooperative SNARK framework proposed by Ozdemir and Boneh. By integrating zero-knowledge proof generation into the MPC algorithm, cooperative SNARK allows relays to jointly prove a specific NP statement, namely VALID MATCH MPC. This statement essentially claims that, given the publicly known commitment of order information and the public commitment of the matching tuple, both parties do indeed know valid input orders.
The dark pool track protects transaction information and participant privacy by using cooperative SNARK (verifiable zero-knowledge proof) and multi-party computation protocols to verify the validity of transactions and enable automated atomic exchange settlement without revealing real identities and transaction details. In this mechanism, participants do not directly access each other’s actual information but use advanced cryptography to prove the compliance and trustworthiness of transactions, while utilizing multi-party computation to ensure the automatic execution of the exchange. Overall, the dark pool track creates a decentralized trading environment that is verifiable and privacy-preserving.

Once this cooperative proof of the valid matching MPC is computed, either party can submit it to the smart contract to actually exchange tokens. Unlike directly running the matching engine execution, the cooperative proof ensures that both parties are confident that the matching (i.e., which tokens have been exchanged) and settlement (i.e., the actual token exchange) are atomic computations.
Therefore, by implementing this MPC-ZKP framework through cooperative SNARK, the project has created a DEX (i.e., no party can exit the transaction after MPC execution) based on atomic computation, and fully confidential transactions, both before and after the transaction.
This describes the creation of a decentralized exchange (DEX) based on complete atomicity and complete privacy through cooperative SNARK to achieve the MPC-ZKP framework. This DEX ensures the atomicity of matching and settlement through cooperative proofs and protects the privacy of transactions using zero-knowledge proofs.
4. Privacy Protection
In the introduction, three problems existing in current decentralized exchanges are mentioned: lack of pre-trade privacy, lack of post-trade privacy, and MEV (Miner Extractable Value) problem. By using the MPC matching and zero-knowledge settlement discussed earlier, Renegade solves these three problems:
1) Pre-trade privacy: Since wallets are maintained locally by relayers, smart contracts never see any order or balance information. In addition, transactions are propagated through commitments to orders, so no information about the orders is known before the order matching.
2) Post-trade privacy: In the on-chain state, there is only a Merkle tree pointing to the wallet commitments, so balances, orders, and transactions are never published in plaintext, even with a valid match. Even if the counterparty knows which tokens were exchanged, they cannot know the exact scale behind the match.
3) Minimization of MEV: Since smart contracts only check zero-knowledge proofs, block producers or sequencing entities cannot insert or front-run transactions.
In other words, Renegade provides the following privacy attributes:
Third parties (including sequencing entities) have no knowledge of the state of the transaction except for the global token inflow and outflow and the total number of open orders.
Counterparties (CounterLianGuarities) can only know which tokens are exchanged in the case of a match, but cannot know any other information. If there is no match, the counterparty can only know this fact.
Relayers (Relayer) managing wallets have knowledge of the contents of the wallet (balance, unfinished orders, etc.), but have no ability to tamper with the wallet.
Renegade solves the problems of pre-trade privacy, post-trade privacy, and MEV existing in current decentralized exchanges by adopting MPC matching and zero-knowledge settlement. This solution allows third parties, counterparties, and relayers to enjoy high privacy protection during the transaction process.
5. Fees and Governance
All fees and governance parameters are subject to change before the mainnet release.
- GAS fees
The GAS fee for creating a new wallet is around $10, and the GAS fee for each deposit, withdrawal, and transfer operation is around $1. If users run their own relayers in super relayer mode (see super relayer), placing and canceling orders will be instant and will not incur GAS fees. If users use someone else’s relayer or do not run in super relayer mode, the GAS fee for placing or canceling orders is around $1.
- Protocol fee
In addition to GAS fees (paid to Ethereum validators), Renegade also charges a protocol fee of 2 basis points (0.02%) from each successful match. If users run their own relayers, this is the only fee to be paid. If users use someone else’s relayer, additional relayer fees are set by the relayer operator. Public relayers charge an additional 8 basis points fee per transaction, in addition to the 2 basis points protocol fee.
- Governance Power
Renegade is a protocol with minimal governance. All contracts are immutable since deployment, and necessary changes or upgrades can only be made by a “developer key” owned by any 2 out of 3 signatures. It has the following permissions:
1) Enable a boolean flag to reject all valid matching proofs, thus stopping matching within the exchange. This permission can be used in cases of smart contract vulnerabilities or oracle manipulation attacks, although Renegade does not expect such situations.
2) Enable a boolean flag to stop all deposits into the exchange. This permission is used in cases of vulnerabilities or when migrating the exchange to a new deployment.
3) Change the global protocol fees, with a maximum of 2 basis points per transaction. Fees can be changed within the range of [0, 2] basis points, including the option to disable fees entirely.
4) Change the public key to which fees are sent within the protocol.
5) Delegate the above permissions to a new address or completely change the address with the permissions.
In addition, the developer key does not have the authority to audit withdrawals or transfers. Furthermore, after 4 years from the contract deployment date, the developer key will lose all permissions and freeze all governance parameters.
3.4 Industry Space and Potential
3.4.1 Classification
- Privacy Track
The privacy track is mainly divided into four sections: privacy computing networks, privacy transaction networks, privacy applications, and privacy coins.
- Privacy Transaction Protocols
The privacy transaction network mainly focuses on the privacy protection of on-chain transaction data (types and amounts of held or traded coins). It supports users to conduct privacy transactions natively through technologies like zero-knowledge proofs, without the need for tools like Tornado Cash, ensuring that their privacy data is not visible to the outside world. It also supports the development of more types of privacy applications within the protocol.
- Privacy Computing Protocols
The privacy computing protocol mainly protects privacy in the process of data generation, collection, storage, analysis, utilization, and destruction. In addition to common scenarios such as DeFi and NFT, it plans to integrate deeply with the big data and AI industries.
Compared to other forms of privacy projects, the privacy computing protocol is a more fundamental infrastructure. Specific transaction information (such as types and amounts of coins) can often be publicly viewed through block explorers, but it emphasizes the privacy of user data usage. Some major privacy technologies include zero-knowledge proofs, secure multi-party computation, cryptography-based learning, and trusted execution environments (TEE). Cryptography-based learning is a technology that allows parties to jointly train a machine learning model without revealing their private data to each other.
- Privacy Applications
Privacy applications refer to applications built on Layer1 or Layer2 protocols that provide privacy protection features for users or DApps in different application scenarios, such as transactions, payments, and emails.
- Privacy Coins
Privacy coins refer to native cryptocurrencies that support privacy, where external parties cannot view specific transaction types, amounts, and other information of the transacting parties. They usually do not support smart contracts and related applications, and related projects have emerged as early as 2014.
Currently, the development of privacy coins is generally average, with user base and transaction volume significantly lower than other tracks such as smart contract platforms and DeFi.
Renegade belongs to the dark pool track in the privacy track of privacy transaction protocols.
- Subtrack: Dark Pool
Dark pool trading is a common practice in network trading and has become an important research topic in the global financial field. In the traditional stock markets of the United States and Europe, dark pool trading accounts for 10-30% of the industry’s total trading volume. The main dark pool trading occurs in the financial derivatives market, which is dominated by a few brokers such as JPMorgan Chase, Goldman Sachs, Fidelity, Deutsche Bank, and Morgan Stanley, who hold a unique position and influence in the market.
Unlike the dominant position in the traditional US stock market, the dark pool market consists of multiple dark pool platforms with different characteristics. According to incomplete statistics, there were already more than 21 dark pool platforms in the US market 10 years ago. The operators of these dark pool platforms mainly fall into three categories: brokers, exchanges, and hedge funds.
Broker-operated dark pool platforms can be divided into three types: dark pools that only trade external institutional orders, dark pools that trade external orders and operator orders, and consortium-type dark pools operated by multiple brokers. There are some representative dark pools in the traditional investment industry, such as Instinet CBX, Goldman Sachs’ Sigma X, and BIDS.
3.4.2 Market Size
- Privacy Track Market
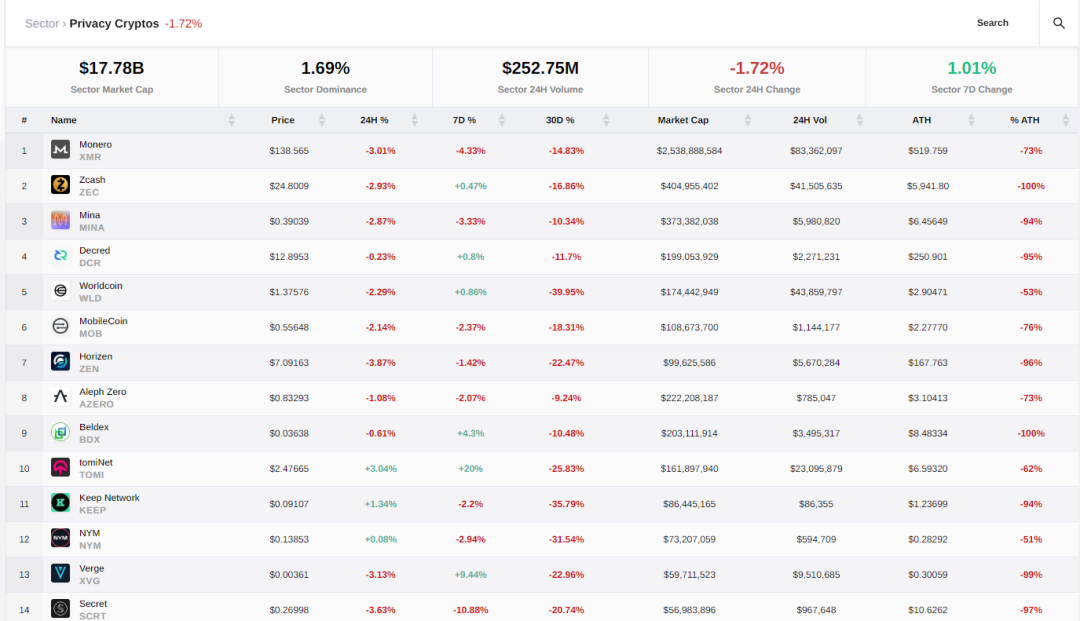
According to data from Crypto Slate, as of August 25, 2023, the total market capitalization of the privacy track is $17.78 billion, with a market share of 1.69%. The trading volume in the past 24 hours is $252 million. According to market capitalization rankings, the top three currencies in the privacy token field are currently Monero (XMR), Zcash (ZEC), and Mina (MINA). These data reflect the current scale and trading situation of the privacy token market.
- Subtrack: Dark Pool Market
In the cryptocurrency field, with the increase in the number of large holders, the demand for large-scale transactions is also increasing. Large orders have a significant impact on the market and may even cause market crashes. In order to reduce the impact on the market, large investors tend to choose over-the-counter trading, which is called dark pool trading in the cryptocurrency field.
However, due to the relatively few institutions participating in the dark pool market and the relatively few new projects during the period from 2021 to 2023, dark pool trading still belongs to a relatively emerging field. Currently, there is limited statistical data on the participation of large institutions in dark pool trading. According to a report by Aite Group, over-the-counter (OTC) trading accounted for 60% of all cryptocurrency trading in 2018, and this proportion is expected to increase to 65% in 2019. In contrast, the proportion was only 32% in 2016.
During the period from 2020 to 2023, some new projects emerged in the field of dark pool trading, such as BlackOcean and Ren. They raised $4.3 million and $3.4 million in financing, respectively.
3.5 Business Data
l Social Media Data
- Twitter: 8,016 followers;
- Discord: 2,006 members, with a daily active user count of about 249.
On Discord, although there is not much casual chat, there are relatively more and in-depth discussions about the project whitepaper. This demonstrates the community members’ interest and active participation in understanding the project and engaging in related discussions.
l Technical Data:
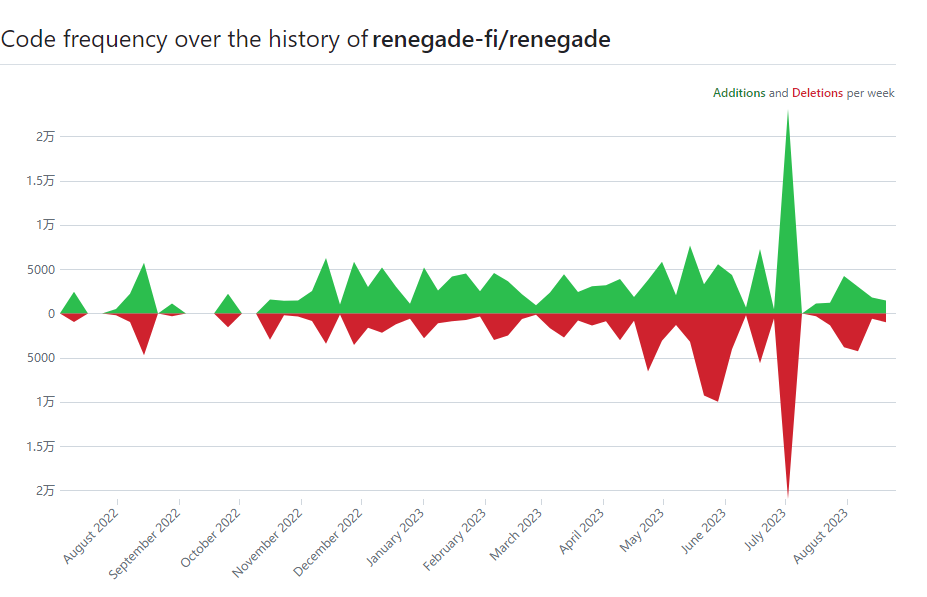
According to data from GITHUB, the project’s code commits started on July 3, 2022. Currently, the number of contributors involved in code commits has reached a maximum of 45, and the number of code commits has been maintained at about 5,000. Starting from October 2022, the number of code commits and contributors has shown an increasing trend. The highest number of code commits in a day reached 20,000 in July of this year. These data reflect the rapid development the project has experienced recently and demonstrate the active participation and contributions of community members.
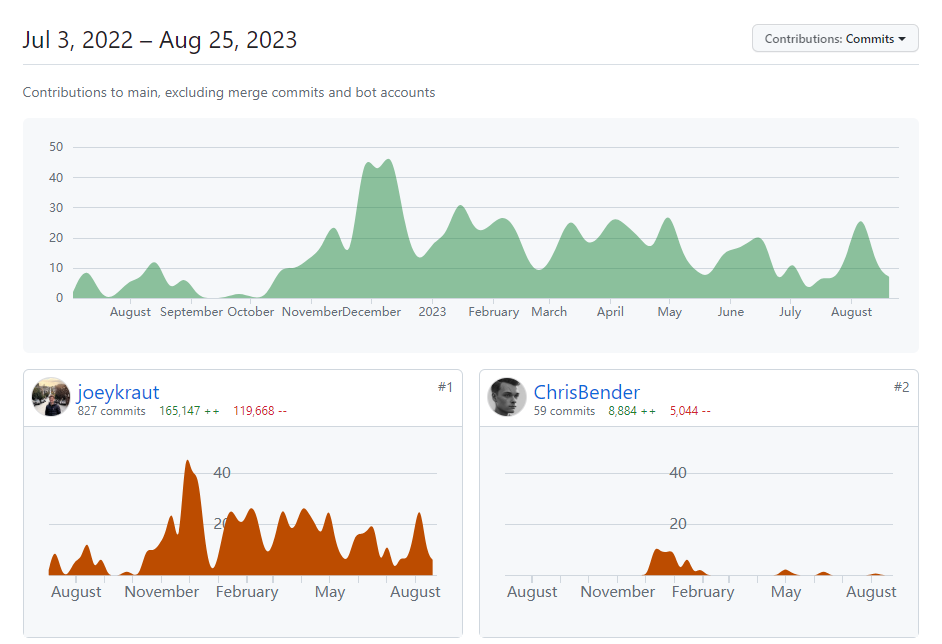
Since the mainnet of the project has not yet been launched, other operational and protocol data of the project cannot be obtained at present.
3.6 Project Competitive Landscape
In the privacy track, the sub-track of dark pool emerged mainly between 2018 and 2019. During the period from 2010 to 2022, the total number of projects launched in this area was relatively small and did not attract widespread attention from the public. It was not until 2023 that the dark pool sub-track became the focus of public attention again. Previously appeared projects such as BlackOcean and the dark pool sections of major exchanges have gradually lost their market competitiveness. The two projects selected this time, the popular dark pool trading protocol REN with a high market value and the recently launched Enclave Spot project, stand out.
3.6.1 Project Introduction
- Ren
Republic Protocol (REN) is a cryptocurrency designed to achieve a protocol for decentralized dark pool trading. It allows for anonymous trading of a large amount of crypto assets (such as BTC, ETH, and ERC20 tokens) in a distributed network. Republic Protocol uses atomic swap technology to trade without exposing order details and matches orders through a multiparty computation protocol engine. This design protects the privacy of transactions and provides convenience for traders. The goal of REN is to provide a decentralized trading system for large transactions, allowing for transactions between ERC20, Ethereum, and Bitcoin with minimal price slippage. It adopts an open-source decentralized dark pool exchange protocol to hide transaction details on the order book.
- Enclave
Enclave Markets is a fully encrypted exchange (FEX). The platform is built entirely on secure enclave technology, preventing any party, including the exchange operator, from reading order activity and protecting assets through a mechanism that eliminates the possibility of a single point of failure. The first product, Enclave Enclave Cross, provides users with an institutional-level, fully confidential intermediary matching platform, allowing participants to trade digital assets in blocks at a given market price without market impact.

3.6.2 Project Comparison
- Republic Protocol (Ren)
The system relies on a carefully designed incentive system to ensure that players adhere to the rules. RenEx “Dark Nodes” run matching engines to ensure the operation of dark pools, and the presence of multiple dark pools mitigates counterparty risk. To prevent malicious attacks, network nodes (Darknodes) must pay 100,000 Ren, which is the token of the Republic Protocol.
- Enclave
Enclave Markets uses secure enclave technology to provide hardware-based memory encryption. This means that critical trading software is encrypted within a walled-off code, known as an “Enclave.” The Enclave is protected by encryption and cannot be tampered with or leak data.
Any changes to the Enclave codebase alter its cryptographic hash value, so no party can insert a hidden code update without the approval of the certifiers.
This setup is a significant improvement over traditional exchange infrastructure as it ensures that no one can control the exchange codebase or customer funds without the approval of the certifiers of the decentralized network.
- Renegade
Renegade maintains anonymity throughout the entire lifecycle of a trade by using Commit-Reveal Schemes, Multi-Party Computation (MPC), and zero-knowledge proofs for an efficient matching engine. This ensures that no third party, including block proposers, can access any user’s token balance, pending orders, or transaction history. This is because zero-knowledge proofs allow Renegade to prove the validity of a transaction without revealing any information about the transaction itself. Once a match is found, the settlement of token exchange is done through zero-knowledge proofs, hiding all transaction information while maintaining system consistency. Apart from the inflow and outflow of global tokens, third parties who are neither end-users nor managing relayers cannot obtain any information about pool activities.
3.7 Token Model Analysis: Token Supply and Distribution
Currently, Renegade has not disclosed any token-related information and is still in the internal testnet stage.
4. Preliminary Value Assessment
4.1 Core Issues
Does the project have a reliable competitive advantage? Where does this competitive advantage come from?
1) Privacy protection: Renegade provides users with high transaction privacy protection through the use of multi-party computation (MPC) matching and zero-knowledge proof technology. Smart contracts never see any order or balance information, and transaction details are not publicly disclosed on the chain. This ability to protect privacy is one of the important competitive advantages of the Renegade project.
2) Transaction efficiency: Renegade adopts MPC matching technology to move the transaction matching process off-chain. This technology greatly improves the speed and throughput of transactions, reduces the waiting time for user confirmation, and provides an efficient transaction experience.
3) MEV risk reduction: Renegade minimizes the opportunity for miners to extract value (MEV) by only verifying zero-knowledge proofs without inspecting the specific content of transactions. This design prevents miners from obtaining sensitive information such as order books and using this non-public information for arbitrage or manipulation of transaction order for profit. Compared to directly processing transactions, only verifying zero-knowledge proofs does not require detailed information such as order books, so miners cannot leverage this advantage to gain additional income. This approach effectively mitigates the threat of MEV to decentralized exchanges and ensures the fairness of transactions. This design prevents miners from improperly sorting or inserting transactions based on insider information. This ability to reduce MEV risk is one of the competitive advantages of the Renegade project.
4) Usability and decentralization: Renegade aims to provide a user-friendly trading experience while maintaining decentralization. Users can choose to use their own wallets and relayers or choose to use relayers provided by others. This flexibility and user-friendliness give Renegade a competitive advantage in the field of decentralized exchanges.
5) Technological innovation: The Renegade project adopts technologies such as MPC matching and zero-knowledge proofs, which are considered advanced in the field of decentralized exchanges. By applying these innovative technologies, the Renegade project can provide a more secure, efficient, and private trading environment, giving it a competitive advantage compared to traditional centralized exchanges.
What are the main variable factors in the operation of the project? Are these factors easy to quantify and measure?
1) Number of users: The success of the project is closely related to the number of users it attracts. More users mean more transactions, higher trading volume, and more fee income.
2) Trading volume and value: The operation of the exchange is closely related to the trading volume and value. These indicators can measure the activity level of the platform, user participation, and the attractiveness of the project.
3) Liquidity: Liquidity refers to the amount of funds available for trading on the exchange. Sufficient liquidity can attract more traders and market makers, providing a better trading experience.
4) Platform Fees: The operating income of exchanges mainly comes from transaction fees. The amount of platform fees is closely related to transaction volume and transaction value.
These factors are usually quantifiable and measurable. For example, the operational status of a project can be evaluated by analyzing data such as user count, transaction volume, and transaction value. Similarly, tracking liquidity indicators and platform fee revenue can provide insights into the development of the platform. These factors can be quantitatively measured through data analysis and monitoring to evaluate the operational performance and development trends of the project.
4.2 Key Risks
1. Protocol Mechanism Risk: There is a risk or deficiency in the Renegade project, which is the failure to directly consider the impact of capital costs and opportunity costs. In Renegade, users need to deposit before conducting transactions, which will have an impact on the protocol in terms of capital costs. In addition, other costs such as transaction costs and hidden costs are not discussed in detail, which is also a shortcoming. Therefore, the project may fail to comprehensively assess and address the comprehensive costs in the transaction process, thereby affecting the interests and attractiveness of participants.
2. Protocol Mechanism Risk: In Renegade, batch auctions are a way to aggregate multiple transaction orders and execute them simultaneously. However, the lack of solid evidence to support batch auctions is a shortcoming. Although intermediate price trading can largely meet the demand, the effectiveness of batch auctions has not been fully verified. This may result in the project failing to provide clear advantages or solutions, and facing a competitive disadvantage in the market.
3. Regulatory Risk: The risk in dark pool trading lies in the lack of transparency and the possibility of non-standard trading behavior. These issues may attract the attention of regulatory authorities, and regulatory pressure may become a ceiling for dark pool trading. Once regulatory authorities launch investigations, it may lead to a series of penalties.
5. References
1. https://renegade.fi/ Renegade official website
2. https://twitter.com/renegade_fi Official Twitter account
3. https://renegade.fi/whitePaper.pdf Whitepaper
4. https://substack.renegade.fi/p/renegade-raises-34m-from-dragonfly Funding situation
5. https://www.linkedin.com/company/renegade-fi/people/ LinkedIn company information
6. https://renegadefi.typeform.com/access?typeform-source=substack.renegade.fi Whitelist testnet
7. https://foresightnews.pro/article/detail/24055 Privacy solutions on public chains
8. https://www.grenade.tw/blog/ama-enclave-markets-spot/ Enclave Spot AMA review
9. https://cryptoslate.com/cryptos/privacy/ Cryptoslate
10. https://twitter.com/renprotocol REN official Twitter account
11. https://www.enclave.market/ ENCLAVE official website
12. https://www.mmjh.net/Bitcoin-shishenme/1036.html Dark pool trading: The secret unknown to the public
13. https://github.com/ Github
Like what you're reading? Subscribe to our top stories.
We will continue to update Gambling Chain; if you have any questions or suggestions, please contact us!