Imagine in a booming bull market, all your cryptocurrencies are stolen… This is the true story of Andrew Schober from Colorado.
In 2018, Schober inadvertently downloaded a tampered version of the Electrum Bitcoin wallet on the Reddit subforum /r/BitcoinAirdrops. This fake wallet contained malicious software: a clipboard hijacker specifically designed to phish Bitcoin. This malware would capture any Bitcoin receiving address on Schober’s machine and disguise itself as it, replacing the intended recipient address with a hacker-controlled address.
Schober had been slowly accumulating Bitcoin since 2014 and ultimately lost 16.5 Bitcoins to this phishing program, which accounted for 95% of his net worth. When he was phished, the value of these Bitcoins was $180,000, but it reached $1.1 million during Bitcoin’s all-time high in 2021. Schober considered it “life-changing money.”
“I found a link to a malicious software on Reddit and installed it on my computer, quickly realizing it wasn’t what it claimed to be,” Schober said. “So I just deleted it from my computer and didn’t think about it anymore.”
- Zhao Changpeng’s old article Why I don’t like large-scale ICOs.
- How can Blur surpass Opensea?
- Key Policy Elements for Cryptocurrencies
“Unfortunately, once this trojan program is installed on your hard drive, removing the original program doesn’t get rid of the trojan. So it has been monitoring my hard drive ever since, and it would activate whenever I copied a Bitcoin address.”
This malware pre-coded 195,112 different Bitcoin addresses. “It doesn’t just change the Bitcoin address to some random new address,” Schober explained. “It matches the first few characters of the address you copy. So visually, it looks very similar, and if you don’t pay close attention to the differences, you won’t notice.”
During Schober’s attack, four addresses received Bitcoins from unsuspecting victims, greatly narrowing down his search range.
Tracking the stolen Bitcoins through Monero
The beauty of blockchain lies in its open ledger. Almost all cryptocurrency transactions leave digital traces.
Typically, tracking these paths involves tracing transfers to determine where the currency ultimately ends up.
In Schober’s case, he traced the stolen Bitcoins to the long-serving cryptocurrency atomic exchange platform ShapeShift, which had maintained an API sharing the addresses involved in its exchanges. API data showed that the “thief” Schober encountered had converted the Bitcoins to Monero (XMR) and used the corresponding address.
Therefore, Schober posted on Reddit to ask if it was possible to trace Monero transactions. Chain investigator and asset recovery expert Nick Bax responded to his request.
“He received five replies, all saying ‘impossible’. I sent him a private message saying ‘it’s really difficult to do, but I’ve done it before. I know a lawyer who has successfully recovered funds,'” Bax said.
Bax eventually submitted on-chain evidence in May 2021, confirming the identity of the hacker in Schober’s lawsuit, which happened over two years ago. During this process, he analyzed the transactions of Monero with a high degree of certainty to determine the origin of the Monero used for Schober’s stolen Bitcoin.
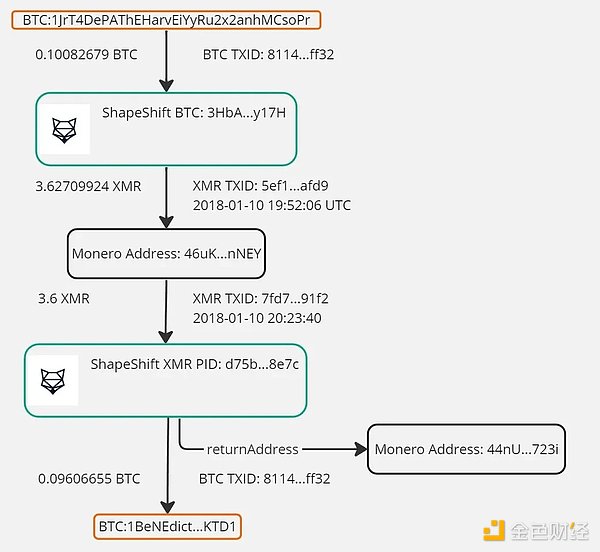
ShapeShift’s API made tracking stolen BTC easy. Source: Nick Bax
He personally wrote Monero tracking software. “You mark an output (where the Monero blockchain directs the transaction), and then look for every transaction that possibly uses that marked output. As you do this, patterns start to emerge.”
This method of breaking the Monero ring signature, now known as the Eve-Alice-Eve (EAE) attack, emerged in the aftermath of the WannaCry ransomware attack activity driven by North Korea in 2017.
“The RingCT of Monero… hides the exact consumption of UTXOs (unspent transaction outputs), but provides blockchain analysts with a list of trusted ‘ring members’ that includes one being spent and the rest being ‘decoys’,” Bax explained in a blog post detailing his investigation results.
The fixed error in Monero may have made it easier at the time to separate the real UTXOs from the decoys and track the transactions.
God’s Hand: Knocking on the FBI’s door
Bax determined that the so-called hacker of Schober converted some stolen BTC into Monero through ShapeShift and then sent it back through the protocol to convert it back into BTC.
The washed BTC was directed to a “vanity address” starting with “1 BeNEdict”. (Note: A vanity address refers to when a hash function generates a string randomly and repeatedly until the address contains the desired string, like a “fancy number”.)
As for Schober’s Bitcoin, it eventually appeared on Bitfinex. Cryptocurrency exchange hot wallets are essentially black boxes because their balances represent the pooled customer funds.
Once cryptocurrencies enter a hot wallet, it is almost impossible to determine where they are withdrawn to, unless the amounts are the same and uncommon – and even that evidence is not certain.
Schober and Bax’s investigation was stuck there for over a year. Schober had subpoenaed Bitfinex to disclose the account owners who received the stolen BTC, but was denied.
“Bitfinex will only respond to requests from law enforcement agencies for customer information, not civil requests, as Bitfinex does not get involved in civil matters, especially in the United States, as US courts have no jurisdiction over us,” said Sarah ComLianGuaini, legal advisor to Bitfinex, in an email response to Schober’s lawyer Ethan Mora.
“Cryptocurrency exchanges like FTX and Bitfinex set up companies in the British Virgin Islands or the Cayman Islands for these legal reasons, so they don’t have to comply with US or any other laws,” Schober said.
“They can stay there and act with impunity. They didn’t even give us an answer.”
Unable to directly access Bitfinex, Mora initiated a so-called Touhy request, demanding that the FBI’s cyber division provide documents and other information related to the agency’s investigation into the malware. Schober filed a report with the FBI immediately after losing his bitcoins.
“The FBI started issuing subpoenas to companies involved in the malware, such as Reddit (where the malware was distributed) and GitHub (where the malware was hosted),” Schober said. The subpoenas occurred in late 2018 and early 2019. The FBI even seized his computer for several months during the investigation.
After about 10 months, the Touhy request was successful. Suddenly, Schober’s team obtained internal data from Bitfinex, which pinpointed the exact IP and email addresses associated with the accounts that received his stolen bitcoins.
“We had no idea what the FBI’s investigation had uncovered until we received the Department of Justice’s response to the Touhy issue,” Mora said.
The Vanity Addresses Are Back
Thanks to the FBI’s subpoenas, Schober’s team was able to identify the hacker’s accounts in a series of online services: Gmail, Keybase, Reddit, Twitter, and GitHub. The malicious code required for the malware, including the Bitcoin address generator it relied on, was found in the hacker’s public GitHub code repository.
Through some accounts, Bax confirmed the 1 BeNedict address used for money laundering through ShapeShift, which he considered evidence of the hacker’s identity (the vanity address matched his name).
In an apparent money laundering process, the attacker’s return address registered with ShapeShift (where the cryptocurrency is sent in case of transaction problems) was identical to the Bitfinex hot wallet from which Schober’s stolen bitcoins were taken.
There was even a post on the Bitcoin developer mailing list, with the sender’s email address matching the alleged hacker’s real name, describing how to easily generate addresses very similar to the provided Bitcoin address. This post perfectly matched the modus operandi of the Electrum malware.
After sufficient diagnosis, Bax discovered that “every Bitcoin transaction sent by the operator of the Electrum Atom malware was sent to a target address associated with the so-called hacker being investigated by the FBI.” The addresses associated with the malware received a total of 17 bitcoins (worth $501,000), 97% of which belonged to Schober. He contacted another victim through the long-running Bitcoin forum BitcoinTalk.
Since Schober’s wallet was stolen, Bitcoin has gone through the entire bull market cycle. Chart by David Canellis
This means that Schober can file a civil lawsuit against the individuals suspected of the crime, as well as another individual who allegedly sold the same malicious software on Reddit. Both were minors at the time of the crime, so the lawsuit also lists their parents as defendants. All parties deny any wrongdoing.
This happened in May 2021, more than three years after Schober’s BTC was phished. At that time, the price of Bitcoin had more than doubled.
Adding to the complexity, the accused hacker resides in the UK. The FBI handed over the case to UK law enforcement and launched a joint investigation. Schober said that both suspects were arrested, interrogated, and their devices were seized and examined in court.
However, before their arrest, desperation (perhaps with a hint of naivety) led Schober to contact them and their parents to let them know they had been discovered. “I hoped they would confess and return the stolen items to me, as all I wanted was for them to return what was stolen, but they did not,” Schober said.
“The UK Crown Prosecution Service eventually informed me that after I contacted them, they may have destroyed their devices because they had new ones and there was not enough court evidence to pursue a lawsuit.”
(Bax said he would do the same as Schober — they believe the parents may be decent people because they work in banks and the UK National Health Service. “They should return the money, and I think all of this will end.”)
Schober’s civil lawsuit is now possibly his only opportunity to seek justice. But the case is progressing slowly, and lawyers are debating which jurisdiction the trial should take place in.
The hackers’ lawyers argue that the lawsuit should be dismissed because Schober, being in the US, has no jurisdiction over someone in the UK. They also argue that he has exceeded the statutory time limit for filing a complaint.
“But from our perspective, it’s not right because it took so much time, effort, and investigation to determine that there was a person on the other end,” Schober said.
Considering he had to wait 10 months for an FBI subpoena after being denied critical information by Bitfinex, he feels he should not be punished by the argument of statutory time limits.
An Unprecedented Case
Cases like Schober’s may be unique as it spans across the entire Atlantic.
“In fact, there are very few cases like this. In fact, I don’t know of any case where an individual tracks, legally summons (according to international law), and prosecutes hackers who steal cryptocurrencies.” Mora said.
“I have been involved in some cases where individual plaintiffs sued domestic fraudsters/hackers from other states in the United States, but those defendants have already been arrested in the United States.”
Mora mentioned cases where the government has brought criminal lawsuits against domestic and foreign hackers, as well as cases where tech giants such as Amazon and Google have sued hackers, some of whom demanded ransom payments in cryptocurrencies.
Schober is not a multinational corporation, he is just an ordinary person, unlike some high-profile and wealthy victims of cryptocurrency theft who sue their attackers.
“I believe this case is unprecedented in many ways… I don’t know how long this case will last,” Mora said.
GitHub cannot inform Schober whether law enforcement has conducted an investigation, making Touhy’s request a gamble with uncertain returns.
How exactly to resolve this issue, no one knows for sure. If a US court rules that the hacker owes Schober money, then a UK court would still need to recognize that judgment before it can be enforced in the UK. Ultimately, it could involve debt collection, liens, or even wage garnishment.
Schober said they were able to trace a large amount of Bitcoin, with the Bitcoin addresses obtained from an FBI subpoena, so it seems that the accused hackers do have funds to repay Schober.
Given that Schober seems to know exactly who stole his cryptocurrency, this situation is particularly frustrating.
Despite everything that has happened, including legal fees and the loss of 500,000 bitcoins, Schober still supports Bitcoin. “I still believe in the future of Bitcoin. That’s what initially attracted me to join. But there is no doubt that the advantage I had as an early participant has disappeared, and that is painful.”
“But I am still positive about it. And I am proud to have been able to push this case to where it is now, because I know the chances of success were very small.”
He is optimistic that the US court will recognize him as a victim of theft. If the attacker is from countries like Russia or North Korea, he has almost no recourse.
“It has been five years, and I hope to resolve this issue as soon as possible,” Schober said. “But on the other hand, I have put in a lot of effort and time, and there are people like Bax and others who support me because they heard this story and think it’s amazing.”
“So I am determined to persist to the end.”
Like what you're reading? Subscribe to our top stories.
We will continue to update Gambling Chain; if you have any questions or suggestions, please contact us!