Beosin EagleEye, a blockchain security audit company, monitored and revealed that on July 2nd, Poly Network, a cross-chain bridge project, was suspected to have suffered from a private key leak or a multi-signature service attack, and hackers used forged credentials to withdraw funds from the cross-chain bridge contracts on multiple chains.
This is not the first time that Poly Network has been attacked. As early as August 10, 2021, Beosin EagleEye monitored and revealed that the cross-chain protocol Poly Network was attacked, and nearly 600 million U.S. dollars of funds were stolen on Ethereum, BinanceChain, and Polygon3 chains.
The incident that year also became the largest hacking incident involving an amount in 2021. Two years ago, attackers used a logical flaw in the EthCrossChainManager contract to call the putCurEpochConPubKeyBytes function in the EthCrossChainData contract to change the Keeper to their own address. Then, the attackers used this address to sign the transaction that extracted the tokens, thus hijacking a large amount of tokens from the LockProxy contract. However, under pressure from multiple parties, the attackers eventually chose to return the assets.
This time, how did the hackers break through Poly Network’s defense? Please listen to our detailed explanation. At the same time, we will use Beosin KYT/AML to unlock more hacking tricks for you.
- Cult of Move’s Blasphemer: The mechanical structure of this building is flawed, it just hasn’t collapsed yet.
- How are ChatGPT and AI changing the podcast industry?
- MPC+AA is the path that Crypto wallets with a billion users must take for Mass Adoption.
Attack Analysis
There are multiple attack addresses in the Poly Network attack incident this time. Taking the address 0x906639ab20d12a95a8bec294758955870d0bb5cc as an example:
First, the attacker called the lock function in the LockProxy cross-chain bridge contract to lock a small amount of Lever Token.
(https://etherscan.io/tx/0x1b8f8a38895ce8375308c570c7511d16a2ba972577747b0ac7ace5cc59bbb1c4)

Note that toChainid is 6, which refers to the BNB chain and can be viewed through https://explorer.poly.network/. If it can be found on the Poly network, it means that it has been verified through the relay chain.

Secondly, switching to the BNB chain, analyze the attacker’s call to the verifyHeaderAndExecuteTx function for withdrawal, and note that the quantity here does not match the quantity of the original lock.
(https://bscscan.com/tx/0x5c70178e6dc882fba1663400c9566423f8942877a0d42bb5c982c95acc348e31)

However, when the relay chain network queries the transaction, it does not find the transaction record.

Thirdly, there is now reason to suspect that the signature may have been leaked or the keeper may have been modified (because the keeper is used to sign withdrawals for users, and as long as the keeper is controlled, withdrawals can be made using forged signatures). The attack on Poly in 2021 was caused by hackers using an attack to modify the keeper.

By analyzing the hacker’s call to the verifyHeaderAndExecuteTx function for withdrawal operations, it was found that the keeper had not been modified. Currently, the official keeper is still being used, and we have reason to believe that three of the keepers (0x4c46e1f946362547546677bfa719598385ce56f2, 0x51b7529137d34002c4ebd81a2244f0ee7e95b2c0, 0x3dfccb7b8a6972cde3b695d3c0c032514b0f3825) may have leaked private keys or the multi-signature service was attacked, allowing the attacker to withdraw funds using forged credentials.

At the same time, we have discovered that the hacker used a batch of addresses to call Poly Network’s contract, taking advantage of vulnerabilities in the UnlockEvent and verifyHeaderAndExecuteTx functions in the contract to attack the project and transfer funds to their own deposit addresses.
Source of Clues
ETH Chain
The address that called the attacked contract obtained transaction fees through a common fee distribution address.
 Figure 1 Fee distribution address transaction
Figure 1 Fee distribution address transaction
The fee distribution address obtained transaction fees through FixedFloat Exchange.
Fee distribution address:
0x0dfeb429166e629204aca66467484cd88cb9701c
Transaction hash
0x69923ea025e7684578b9cbfd7af1c862f044f8b09398234039ce9989bd55561a
The hacker’s collection address has a total of three sources of transaction fees.
1. The first transaction fee comes from Tornado.Cash.
 Figure 2 Collection address 0xe0afadad1d93704761c8550f21a53de3468ba599 transaction fee source
Figure 2 Collection address 0xe0afadad1d93704761c8550f21a53de3468ba599 transaction fee source
2. Deposit to the address through Bybit after passing through an intermediate layer.
Transaction fee transfer address:
0x4FbC021742A4664D1cf8e9d2730b8519B9Dcc523
Transaction hash:
0xb8b0626b86ed336c9c0fff56b20761438535aa06461dcca9cdc39dc10ec1c620
3. Use the stolen virtual currency to exchange for ETH as transaction fee
There are two hacker addresses that exchange the stolen USDT/USDC for ETH in the DEX, and then use it as the transaction fee for the subsequent address. Below are the initial transaction fee transfer addresses and hashes of the two addresses.
Hacker address 1:
0xdddE20a5F569DFB11F5c405751367E939ebC5886
Transaction fee transfer address:
0xD475747a4937a66Cc7D4a2c7eA7F6e827D0f7390
Transaction hash:
0x853b75b1b8a7f56c51fcba9b996af8d132b784cfa0da7162c20a48a5994d8a06
Hacker address 2:
0x8E0001966e6997db3e45c5F75D4C89a610255b2E
Transaction hash:
0x0f3cf1fe16052223e091e87c2a6f7a9a94e53a565dfac7b83eb0b9b79458ad8f
BSC Chain
 Figure 3 Transaction fee distribution address 0x1634Bf68e6b3Bb8D79388EfB3d1A5215506FBbEd source of transaction fee
Figure 3 Transaction fee distribution address 0x1634Bf68e6b3Bb8D79388EfB3d1A5215506FBbEd source of transaction fee
This transaction fee distribution address obtains and distributes transaction fees through two exchange platforms: Kucoin and ChangeNow.
1. Kucoin
Transaction hash:
0x0b0aa0d438e4f15c919e55148c87890ae0d089d036cadbdc6b87afa9e19f747b
2. ChangeNow
Transaction hash:
0x6db6c128960b7268f2bf8c199b2c0c017b3bee29bbefac0bf5d31c63b6373075
The source of the transaction fee of the hacker’s collection address is the transaction fee distribution address. The precipitation address has not transferred the transaction fee.
Polygon Chain
 Figure 4. The source of the transaction fees for the hacked address 0x09F92eDce2E46C399BFE7881a7619598AF8436d5.
Figure 4. The source of the transaction fees for the hacked address 0x09F92eDce2E46C399BFE7881a7619598AF8436d5.
The address that called the attacked contract obtained the transaction fees through a common distribution address.
This address obtained the transaction fees through FixedFloat exchange.
Transaction hash:
0xc7a25eb840718028c0d8f402d1293dcb479755d77609a7dfb616c10e90176dec
The source of the transaction fees for the hacker’s collection address is
0x09F92eDce2E46C399BFE7881a7619598AF8436d5.
The sedimentation address has not transferred the transaction fees.
Beosin KYT/AML tracks the fund details with you
ETH chain
The following is a brief chart of the stolen coin funds tracked by Beosin KYT/AML on the ETH chain:
 Figure 5. Brief chart of the flow of stolen coin funds tracked by Beosin KYT.
Figure 5. Brief chart of the flow of stolen coin funds tracked by Beosin KYT.
First, the hacker used a batch of addresses to call the attacked contract to exploit the vulnerability, using a total of 20 addresses.
The transaction fees for these 20 addresses all came from the address 0x0dfeb429166e629204aca66467484cd88cb9701c, and the transaction fees for this address were transferred through Fixedfloat.
The hacker called the LOCK function in the Poly Network contract to lock the funds, and then called the UnlockEvent and verifyHeaderAndExecuteTx functions to attack the project party with the funds stolen. The case is as follows:
 Figure 6. Record of the function called by the stolen coin hash.
Figure 6. Record of the function called by the stolen coin hash.
It can be seen that in UnlockEvent, the variable toAddress has changed to the hacker’s collection address, and the amount has also been modified to the amount of stolen funds (1,592.51818168432 ETH in this case).
 Figure 7. Record of the stolen coin transaction input information.
Figure 7. Record of the stolen coin transaction input information.
From here, it can be seen that the Proof item in the input data has been replaced with content containing the hacker’s collection address.
The transaction fees for the involved hacker’s address were mainly obtained from four channels:
1. Transfer ETH through Tronado.cash
2. Transfer ETH through Bybit exchange
3. Transfer ETH through KuCoin exchange
4. Transfer ETH through FixedFloat exchange
5. Use the stolen ETH
The hacker began attacking on July 1, 2023. So far, they have only exchanged some virtual currencies for ETH through DeFi exchanges, and transferred ETH and some other virtual currencies to other settling addresses. They have not yet laundered the stolen funds, but have prepared the transaction fees and will transfer the funds to the settling addresses immediately after confirming their safety.
BSC chain
The stolen coin path of the BSC chain is similar to that of ETH. The hacker continues to use some of the same addresses to carry out coin theft operations and uses contract vulnerabilities to transfer virtual currencies to the hacker’s collection address.
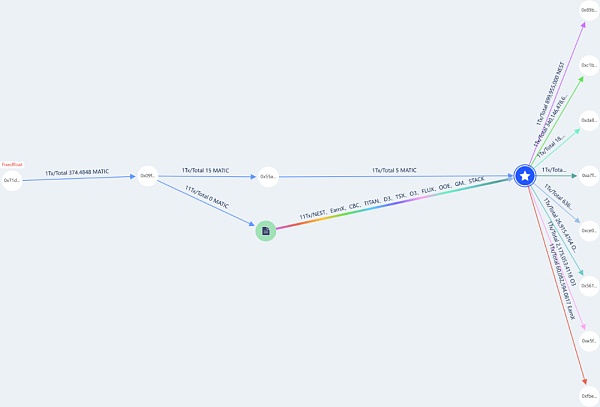 Figure 8 Beosin KYT/AML tracking of stolen funds flow chart
Figure 8 Beosin KYT/AML tracking of stolen funds flow chart
First, the hacker used more than 30 addresses to call the attacked contract to use the vulnerability. The fees of these addresses all come from the address 0x1634Bf68e6b3Bb8D79388EfB3d1A5215506FBbEd, and the fees of this address are transferred to the Kucoin and ChangeNow platforms.
Then, using the same vulnerability to attack the contract and transfer the stolen funds to the collection address, some of the funds were transferred to multiple settling addresses. <sBlockingn yes’; mso-bidi- font-size:10.5000pt;mso-font-kerning:1.0000pt;”>
Polygon chain
The stolen coin path of the Polygon chain is similar to the above two chains. The hacker continues to use some of the same addresses to carry out coin theft operations and uses contract vulnerabilities to transfer virtual currencies to the hacker’s collection address.
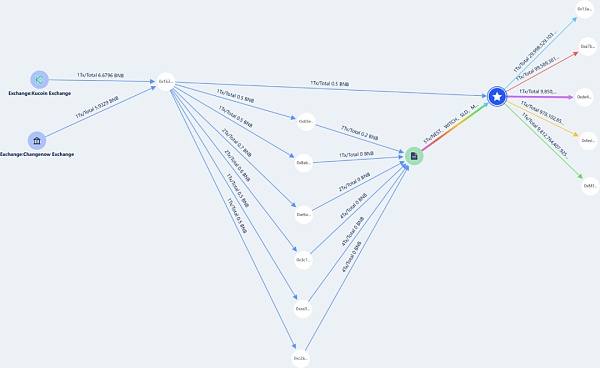 Figure 9 Beosin KYT/AML tracking of stolen funds flow chart
Figure 9 Beosin KYT/AML tracking of stolen funds flow chart
First, the hacker used a batch of addresses to call the attacked contract to use the vulnerability. The Polygon chain only used one address, 0x09F92eDce2E46C399BFE7881a7619598AF8436d5, and the fees were transferred through Fixedfloat.
Then, using the same vulnerability to attack the contract and transfer the stolen funds to the collection address, some of the funds were transferred to multiple settling addresses.
Like what you're reading? Subscribe to our top stories.
We will continue to update Gambling Chain; if you have any questions or suggestions, please contact us!