In this article, we discuss why interoperability is needed and how to evaluate it, take a closer look at existing and upcoming solutions, and summarize our vision for a truly interoperable future.
A community-driven NFT project has failed to launch, and the luxury lineup is impeccable, why should it fail? It is recommended to read Article 2.
About Capital has acquired China’s once-popular cryptocurrency exchange Huobi Global. It is recommended to read Article 3 for specific circumstances.

Authors: 0xavarek, Defi_Maestro, j_mokwh, wyangdanand, GabrielGFoo
introduce
The crypto space is always looking for the next narrative after L1, L2, and NFTs. We believe that interoperability is the next most likely dominant narrative, as it brings together the currently segregated blockchain ecosystem, much like how globalization has brought the world economy together.
Before globalization, goods were produced and sold through localized supply chains. Such a pattern implies a lot of duplication and inefficiency. By introducing comparative advantage and international trade, globalization enables fragmented, non-localized supply chains, eliminating this inefficiency. Today, a product like a Boeing jet can contain parts manufactured by 58 non-US product specialists.
The crypto world is similar to the world economy before globalization. Ecosystems (countries or regions) are compartmentalized, and each country tries to excel on every element of the economic value chain (different DEXs, currency markets, aggregators, etc.). Interoperability is a key element needed to allow blockchains to communicate: similar to how countries open up their borders, both physically and virtually, to allow the free exchange of information and capital. We believe that new advances and technologies focused on Web3 interoperability can usher in its own “Globalization 3.0” and ignite the next wave of growth.
In this article, we discuss why interoperability is needed and how to evaluate it, take a closer look at existing and upcoming solutions, and summarize our vision for a truly interoperable future.
Why do we need interoperability?
The blockchain world is at a crossroads – it has massive adoption but lacks a catalyst for mass adoption. We believe that, fundamentally, the answer to this question is interoperability. The utopian vision of the future of blockchain encompasses the ability for digital assets and information to flow frictionlessly between professional ecosystems without creating redundant data or requiring new intermediaries. In our view, here are a few main reasons why interoperability is critical to fostering crypto mass adoption.
Interoperability brings comparative advantage to the blockchain space
The three pillars of blockchain design are: decentralization, security, and scalability. Because of the conflicting engineering requirements to implement each pillar, existing blockchains have to compromise on one or more pillars in order to excel in their chosen field of expertise, which is the blockchain trilemma. For example, on a proof-of-stake (PoS) chain, one way to improve scalability is to reduce the time it takes to reach a transaction, which can be achieved by reducing the number of validators — a design that compromises decentralization to achieve Extensibility. PoS itself is a compromise on scalability security: in the original proof-of-work (PoW) networks, validators solved cryptographic puzzles before voting on the block state, while PoS validators only needed to prove that they were in the network Shares on the board can be voted.
Interoperability could potentially solve the trilemma, as specialized blockchains would be able to focus on their strengths, rather than trying to provide full-stack services as they are now. A scalable chain with a high TPS (transactions per second) but a more centralized validator network can focus on processing high-frequency tasks with less security impact (e.g., graphics data for on-chain games), while having a lower TPS The security chain can handle low-frequency tasks with high security requirements (eg, a gamer’s in-game purchase history). These are just the surface of the endless applications that make the crypto ecosystem more accessible and efficient.
Interoperability brings simplicity to end users and fosters mass adoption
User experience (UX) is often considered the most critical success factor for software and technology products. A smooth, intuitive user experience is critical to getting the next billion people to use Web3 online. We cannot realistically expect an inexperienced user to maintain 10 different wallets and keys, each serving a specific purpose for their transaction needs.
Interoperability enables developers to build front-end applications with an easy-to-use UIUX that leverages multiple dedicated chains on the back end. If entering CEX, exchanging gas, withdrawing to CEX-backed main chain, bridging from main chain to new chain, and depositing funds to CEX can be done with the click of a button, new pools on the new chain that are user-friendly will be created.
Interoperability makes 1+1 > 2
Returning to our globalization example, the value of an integrated world economy is greater than the sum of the values of the individual economies, ceteris paribus1. We believe interoperability can do the same for the blockchain world in a number of ways.
First, developers will be freed from the urge to offer full-stack services to attract adoption (TVL) and instead focus on building core strengths that lead to more efficient solutions.
Second, interoperable blockchains lead to interoperable data, which is a huge improvement over today’s siloed and hard-to-query data scattered across chains. Better data availability and composability will catalyze Web3’s self-evolution as previously untouched ideas emerge from new observable data.
How to assess interoperability?
We think the Interoperability Trilemma 2 nicely summarizes the three pillars of a truly interoperable solution: commonality, trustlessness, and scalability. As readers will discover in later sections, current interoperable solutions often involve sacrificing one or more pillars in favor of others.
- Generalizability: refers to the ability to handle complex cross-chain interactions beyond simple token transfers, such as smart contract calls and messages
- Trustless: Refers to having the same security as the underlying blockchain
- Scalability: Refers to the ease with which any blockchain or application can be integrated into existing interoperability solutions
These three pillars can be broken down into different properties against which developers and users can assess the level of interoperability. Some key features are discussed below.
- Security: Who verifies transactions and systems? Does the solution inherit the underlying security mechanism of the blockchain? Does this solution require an external validator? If so, are they licensed or unlicensed?
- Convenience: How long does it take for a transaction to complete, and how many supporting transactions do users need to sign to execute the entire transaction? How long and how complex will it take for developers to integrate an interoperability solution? Do developers have to build additional infrastructure, or can they “plug and play” instantaneously?
- Connectivity: Refers to how many different types of target chains the solution can connect to (i.e. rollups, sidechains, layer 1)
- Ability to handle complex and arbitrary data: Can the solution handle more complex data such as message transfers and smart contract calls? Or only support cross-chain token transfer (ie native bridge)
- Cost-effectiveness: How much does it cost to transfer assets across chains and how much does it cost to maintain the solution? Some solutions require an extra transaction layer, which increases gas costs, while others cost developers millions of dollars per day just to get the solution up and running.
Interoperable Solutions
We’ve discussed why we need interoperability and the properties that evaluate the level of interoperability. The following sections will review existing and upcoming interoperable solutions, divided into two categories: non-interoperable ecosystem-based patches and natively interoperable solutions.
Patching solutions based on non-interoperable ecosystems
The solutions mentioned in this section are what we call “patches” because they are built on top of non-interoperable chains in an attempt to add some interoperable properties.
Centralized Exchange (CEX)
CEX enables users to move tokens between chains, much like banks do to facilitate the transfer of value between otherwise siloed sovereign economies. While CEXs are one of the friendliest and most cost-effective ways for users to transfer assets across chains, they also have significant drawbacks.
On top of that, most CEXs require KYC before allowing withdrawals, which adds additional complexity for regular users. Second, CEXs join tokens and chains according to their own agenda, which puts users’ access to their assets under arbitrary control – for example, top exchanges stop withdrawals to/from the LUNA chain during the LUNA-UST implosion /deposit. Degens, who bridged new chains shortly after the chain’s genesis, also found CEX to be insufficient, as smaller chains with lower TVLs were usually not added until later, if at all. Most importantly, smart contracts cannot be combined through CEX, so that exchanges can only facilitate the transfer of tokens, but not the transfer of arbitrary data.
CEX also represents the user’s counterparty and credit risk. As CEX regulation is still in its infancy, users often lose all their assets and have little legal recourse when reckless operations cause the exchange to go bankrupt.
Burning Bridges
Cross-chain asset bridges are the most widely used interoperability patching solutions. These bridges allow users to transfer their assets from the source chain to the target chain. Bridges are powered by a system that goes through locking, minting, burning and redemption. On both chains, smart contracts will be deployed to lock the native assets on the source chain and issue “packaged” assets on the target chain in a credit way.
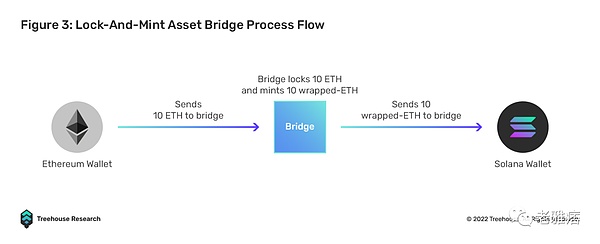
For example, Bob locks 10 ETH on Ethereum and mints 10 wrapped ETH (wETH) on Solana via the bridge. In principle, the 10 wETH minted by Bob on Solana is backed 1:1 by 10 ETH locked on the Ethereum chain. Bob can do the opposite, first burn 10 wETH on Solana, then redeem the locked 10 ETH on the Ethereum chain. In this case, the fundamental aspect is managing supply and keeping the two chains in sync.
Here are some famous bridges:
- Wrapped BTC (WBTC)
- Multichain
- Portal
- Poly Network
- Ronin Bridge
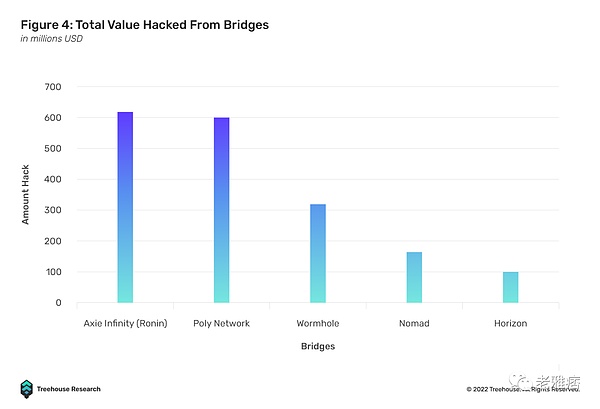
In TVL, Bridges has expanded to as high as US$12.35B. The need to transfer assets across chains is growing every day. The question is, how safe and efficient are these asset bridges? Unfortunately, due to the large amount of funds held, bridges are often targeted and exploited, resulting in more than $1.8B of funds being compromised. Some notable vulnerabilities are listed below.
- Poly Network: The $600 million Poly Network hack happened because of poor management of access rights to two important protocol smart contracts. As a result, the system was hacked and the hacker was able to add his own public key to drain the wallet.
- Wormhole (Solana): The $321 million Wormhole hack occurred because the ability to verify signatures during token swaps was deprecated. The hackers were then able to mint over 120K wETH tokens by replacing their own verification routine, which always said the signature was valid.
- Ronin (Axie Infinity): $625 million Ronin bridge fell victim to phishing attack. The private key of the Ronin validator fell into the hands of the hacker, which allowed the hacker to withdraw funds from the bridge contract.
- Horizon (Harmony): $100M Horizon Bridge is another victim of a potential phishing campaign in which their multi-signature validator’s private keys were stolen.
- Nomad: The $190 million Nomad hack was caused by a poor operational strategy that resulted in a bad Merkle root initialization, causing every message to be proven valid by default.
Judging by the prevalence of hacking, a major issue with Asset Bridge is security. Most DeFi protocols tend to inherit the security mechanisms of the underlying blockchain, but today’s bridges do not. Instead, bridges rely heavily on an independent set of validators rather than the validators of the PoS chains they serve, making them significantly less secure.
For example, under the PoA (Proof-of-Authority) consensus architecture, the Solana Wormhole bridge currently has only 19 “Guardian Network Validators”. The secure multi-party computation model relies on several multi-signature keys to authorize any transaction: for example, Ronin Bridge requires 4 out of 9 multi-signature keys to approve transactions, while Harmony Horizon requires only 2 out of 5 multi-signature keys to authorize. Last but not least, the WBTC bridge uses a single custodial approach, which creates a risk of centralization. For the above reasons, bridges are currently the Achilles heel of the blockchain ecosystem, as they are more vulnerable than the blockchain itself.
Aside from security concerns, bridges are similar to CEXs in that they cannot handle complex arbitrary data. Bridges are essentially cross-chain pawnshops — no one expects a pawnshop to pass complex instructions between the two companies.
Finally, interacting with most bridges is a tedious and tedious task for the average user. The following is an example of a typical bridging process:
To exchange ETH on Ethereum for AVAX on Avalanche requires:
- Convert ETH to USDC on DEX
- Connect USDC from Ethereum to Avalanche via AVAX Bridge
- Make sure you have enough gas to complete the final Avalanche exchange by depositing AVAX tokens into your Avalanche wallet
- Swap USDC to AVAX on Avalanche via another DEX
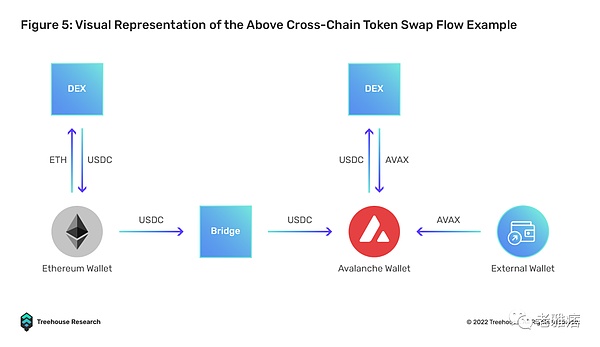
The whole process involves signing at least 3 transactions, interacting with 3 dApps, and switching chains at least once if the user is on MetaMask. To check transaction status, users need to have Etherscan and Snowscan ready. Without streamlining these processes, bridges and any cross-chain dApps will still be severely hampered by user experience barriers.
Interoperable Solutions
The patch solutions discussed above have only one interoperable property – connectivity. They fail in other areas such as security, convenience, ability to handle complex messages, and cost-effectiveness. Instead of building patches later, a new generation of solutions decided to build interoperability into their DNA.
Full chain DEX
DEX chains introduce liquidity pools on multiple chains with intermediary tokens to facilitate exchanges. Examples include THORChain and SifChain. Unlike bridges, full-chain DEXs do not wrap assets. Instead, they exchange the original assets for the intermediate tokens, which are then exchanged for the target tokens. Of course, these transactions are implemented by liquidity providers.
For example, on THORChain, when a user wishes to exchange ETH on Mainnet for SOL on Solana, the user will first send their ETH to the THORChain lock smart contract. THORChain will then perform a swap from ETH to THOR and then THOR to SOL. Subsequently, a message will be sent to the Solana liquidity pool smart contract, and the SOL will be released to the user’s Solana address.
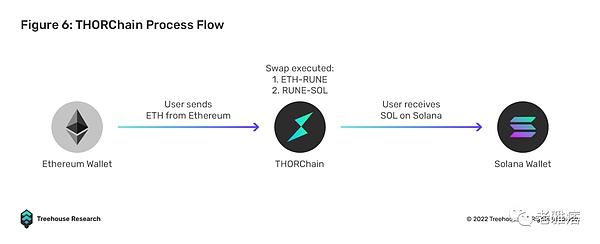
THORChain eliminates the need to create wrapped assets through a locking and minting mechanism, the protocol provides real utility in enabling users to seamlessly exchange native assets between blockchains. This simple UI/UX approach will be a key selling point in driving mass adoption and pulling users away from centralized alternatives.
Compared to CEX, full-chain DEX does not require KYC. Liquidity is unified because all chains use the same “native token” liquidity pool for transactions. Users do not rely on DEX oracles or security assumptions, as the risk of decoupling is borne by liquidity providers. Full-chain DEXs are also scalable, as anyone can add liquidity to any currency pair.
However, THORChain’s intermediate chain design brings some key risks and nuances. Since the THORChain network is protected by the bond proof network, node operators pledge RUNE bonds to underwrite assets in the DEX liquidity pool. As the TVL in the liquidity pool grows, node operators need to take more and more risks. Naturally incentivized by Incentive Pendulum, node operators must combine RUNE with pooled capital to function optimally.
This means that building a full node on the THORChain network increasingly requires more funds. Currently, the network has 95 active nodes, a TVL of over $260 million, and a full node average bond of 838,499 RUNE, or $1,468,839.90 at market prices. Of the 95 active nodes, the node with the lowest bonded capital is around 528,000 RUNE or $929,000. As a result, small node operators with relatively low capital cannot participate in securing the network, leading to a concentration of control on node operators with larger capital budgets.
Inadvertently, this begs the question of whether a THORChain or full-chain DEX with a similar design is really as decentralized as advertised. Beyond that, most, if not all, of Thorchain’s full nodes are hosted on centralized cloud computing services. Of the 95 nodes, 87 are hosted on major cloud services such as Google, AWS, and Digitalocean, with AWS taking the lion’s share at 38%. In theory, this poses a significant risk to the network, as cloud computing services could face network outages or even be regulated.
While this design for interoperability introduces many novel ways to connect blockchains to each other through great UI/UX, cleverly engineered token economics and security mechanisms, while retaining its trustless design, The complexity of the protocol makes it vulnerable to many attacks and security vulnerabilities. The THORChain protocol has been exploited 3 times in the past year, losing over $12 million in pooled liquidity to bad actors. As with any new innovation, growing pains are inevitable. Since then, the THORChain team has focused more on protocol security and introduced new improvements to increase liquidity and overall network decentralization.
network of networks
Cosmos and Polkadot are two examples of homogeneous “networks of networks”. They are considered layer 0 in the blockchain stack. Both of these layer 0s introduce a standard for any layer 1 blockchain to connect to them and form an interoperable network.
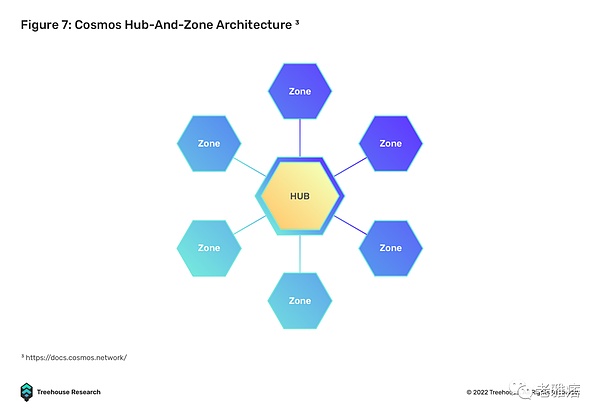
Cosmos enables interoperability through the Inter-Chain Communication Protocol (IBC). IBC allows heterogeneous blockchains to communicate in a trustless and permissionless manner by providing a dedicated relay to verify block state and communicate in Interchain Standards (ICS). With IBC, independent blockchains will not have to communicate bilaterally as they would with a bridge.
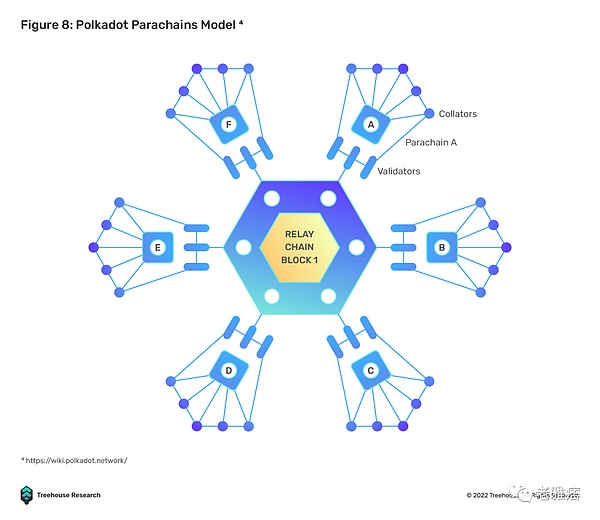
The Polkadot ecosystem consists of specialized, purpose-built blockchains called parachains. Cross-chain interoperability is achieved through a protocol based on the Cross Consensus Message (XCM) format. The XCM format is similar to IBC’s ICS, which standardizes cross-chain communication. There are two main messaging protocols used to act on XCM messages, Vertical Messaging (VMP) and Cross-Chain Messaging (XCMP). VMP allows parachains to upload/download messages to and from the relay chain, while XCMP facilitates the exchange of information on the relay chain.
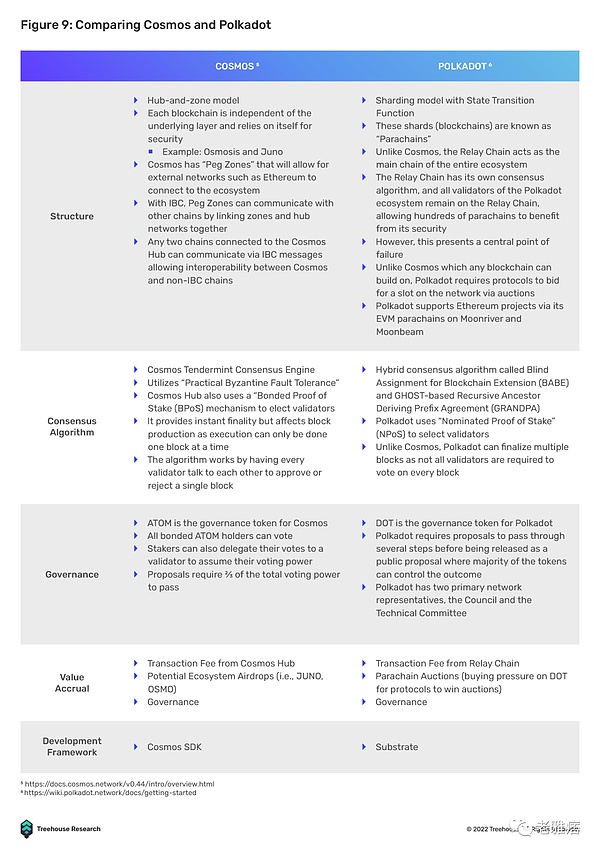
While Cosmos and Polkadot operate similarly, they differ the most in terms of connectivity and security mechanisms. Cosmos allows anyone to build on it, while Polkadot has a cap on the parachain slots available to it. Zones on Cosmos rely on themselves for security, while parachains in Polkadot can rely on the security mechanism of the relay chain.
Having said that, both Cosmos and Polkadot have their own set of challenges to overcome, as both design philosophies face some corresponding issues. The first is the question of bootstrapping. While Cosmos is built as an open network where anyone can deploy a new chain, deployers will need to look for an entirely new set of validators as security is not shared between heterogeneous blockchains.
This process can be time-consuming and inefficient, as operating a validator node can be challenging for those without the proper hardware and technical knowledge, leaving a very limited pool of potential candidates.
In contrast, Polkadot’s parachains do not require a new set of validators, as the network has opted for a form of shared security in which its parachains are validated by the relay chain’s validators. While this appears to be a plus point in bootstrapping new parachains, the process is severely hampered by requiring new chain deployers to bid for parachain lease slots in candle auctions. Since parachains are a scarce resource in the Polkadot ecosystem, the speed of network growth is limited as adding new parachains becomes a long and tedious process. All things considered, the Polkadot and Cosmos ecosystems are still struggling to gain significant adoption, with TVLs of around $380 million and $1.05 billion, respectively.
Having said that, Cosmos and Polkadot are implementing new network upgrades to build stronger infrastructure that will foster greater adoption of the ecosystem. Cosmos is currently implementing interchain security to address its bootstrapping problem, where the consumer chain can rely on the supplier chain’s validators for security. In terms of enhancing Polkadot’s cross-chain capabilities, the introduction of XCM should facilitate a higher level of cross-chain composability similar to IBC. Although projects like Evmos and Moonbeam are isolated within their own ecosystems, they try to be an interoperable bridge with EVM-based ecosystems.
In direct opposition to Fat Protocol Thesis, application-specific or specific-use chains are considered the end game for decentralized applications, as protocols are no longer bound by the general-purpose blockchain they are built on. This allows project teams to focus on building the products and applications users want to use, while maintaining full sovereignty. By design, networks such as Cosmos and Polkadot provide a way to isolate decentralized applications from censorship risks if general-purpose blockchains become more regulated and centralized in the future. Hence, through strong and scalable shared security, natively interoperable application-specific chains, fast and seamless UI/UX, trustless bridges, and overall better connectivity to other blockchain ecosystems.
Relayer-Oracle Protocol
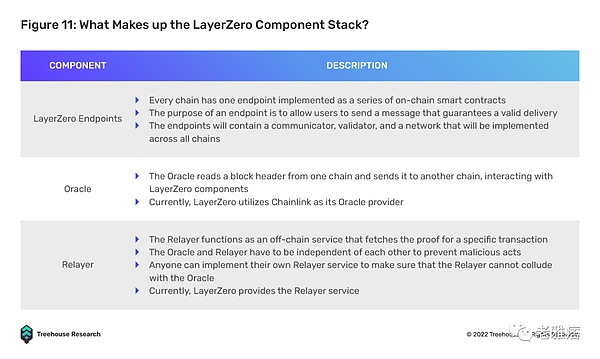
The Relayer-Oracle protocol is designed to solve the emerging problem of the Relayer-Light Client protocol, namely low cost effectiveness. LayerZero is one of the most prominent contenders in this space, leveraging on-chain light nodes to facilitate cross-chain information exchange. The endpoints of the sender chain communicate with the specified Oracle and Relayer and the receiver chain. The oracle message blocks the offending header to the endpoint of the receiver chain, while the relayer validates the transaction. Compared to Polkadot XCMP which relies on a single relay chain as an intermediary and introduces a bottleneck risk (if the relay chain fails, interoperability fails), LayerZero’s Relayer-Oracle solution leverages existing endpoint light nodes for security, compared to Relay chain model.
To ensure scalability, LayerZero endpoints are lightweight client nodes. Unlike current Repeater-Light client solutions that store and replicate block headers in the client, this process is outsourced to Oracles to fetch block headers from the chain, significantly reducing costs by eliminating the need, especially on gas-heavy chains, every few days. Sync block headers every second. Operationally, LayerZero endpoints can be used as cost-effective on-chain smart contracts. Current endpoint builds are easier to integrate with EVM, but still require custom builds for non-EVM chains.
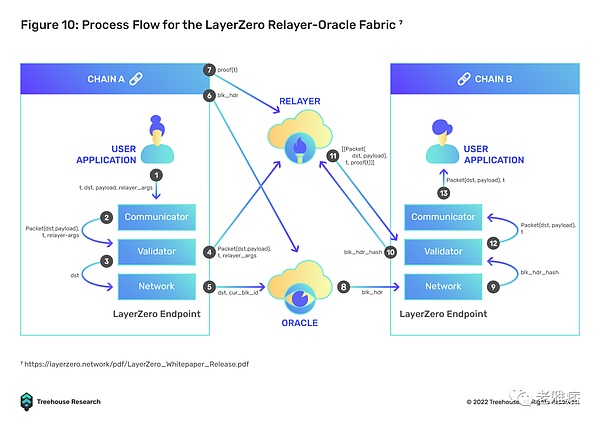
LayerZero can nurture multiple use cases such as cross-chain DEX (Stargate Finance), multi-chain yield aggregators, and multi-chain lending, all without going through multiple asset hops on different chains. This feature will effectively solve the main problem of UI/UX in a multi-chain environment by providing users with a very seamless experience, as users will be able to interact with DeFi applications on other sovereign blockchains, while only on the source chain own assets. For example, deposit ETH as collateral into the Aave lending pool on the Ethereum mainnet, while receiving borrowed USDC on Avalanche.
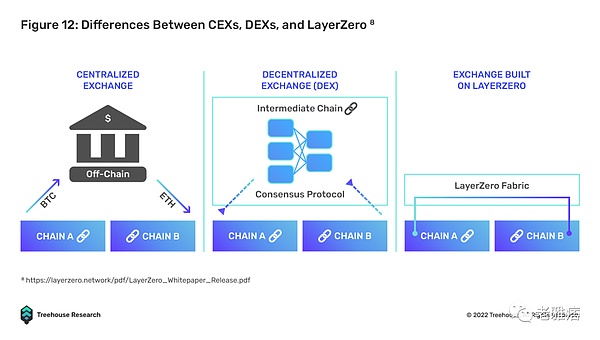
At its core, LayerZero provides a trustless general message relay mechanism that focuses on efficient delivery, which can be achieved if relayers and oracles are independent of each other. There is no need for cross-chain state machine replication or intermediary-wrapped tokens, which greatly reduces bottlenecks and costs.
Notably, LayerZero achieves “trustless” by choosing a weaker trust condition, namely “independence”. As long as the Oracle and Relayer are run by independent parties (currently Chainlink’s Oracle, LayerZero’s Relayer), malicious collusion is statistically impossible.
To further secure the transport layer, LayerZero also introduces the concept of “pre-crime”, allowing relayers to stop a hacking attack before it happens. Essentially, the pre-crime mechanism checks the blockchain state relative to the target blockchain to verify that no malicious act has been performed. If a malicious state is detected, LayerZero is able to fork the target chain before delivering generic messages and executing transactions.
LayerZero’s implementation of a natively interoperable solution looks the most promising, with an elegant, secure, and cost-effective design with significant moving parts compared to traditional lock-and-mint bridges, full-chain DEXs, and even web networks Reduce design. Cross-chain messaging becomes more efficient by outsourcing the data retrieval process to independent off-chain relayers and oracles. To scale, LayerZero only requires the connected blockchain to enable smart contracts to deploy its smart contract endpoints.
While some may argue that LayerZero is not fully decentralized in its current state, as Relayer is run by the LayerZero team, the long-term vision is to eventually allow anyone to independently set up Relayer to support the platform. Compared to the above design, this will significantly reduce the time to bootstrap and connect to a new chain, as there is no need to acquire a new set of validators like Cosmos and Polkadot-based chains.
Honorable Mention
Here are some of the interoperable solutions we looked at for this article. We can’t cover all of them in one article, but each of them has unique advantages for the interested reader.
- Synapse: Cross-chain AMMs and Bridges
- Hop Protocol: Rollup to Rollup Universal Token Bridge
- Axelar Network: A chain-agnostic interop layer connecting layer 1
- Connext: A liquidity network for transferring assets across chains using atomic swaps
- Router Protocol: Cross-chain messaging protocol, built as a mesh network of chains connected by nodes
- ICON Network: Universal Cross-Chain Messaging Using On-Chain Light Clients
- Across: Layer 2 Cross-Chain Bridge
- Bungee Exchange: Bridging Aggregators
Why are outdated interoperability designs still more widely used?
According to DeFiLlama’s Bridge and Cross-Chain category, of the $13.52B in TVL, $12.49B is locked in traditional lock-and-mint bridges like Wrapped BTC, Multichain, and Portal. While not taking into account the various chains in the Cosmos and Polkadot ecosystems, the data suggest that there is a huge difference between adopting bridges and natively interoperable protocols, although the latter brings innovation and security enhancements. Which begs the question: “What’s preventing better interoperability solutions from being widely adopted?” Here are three reasons we think:
easy to use
The MetaMask wallet remains one of the most widely used wallets in the crypto industry. This is because MetaMask is compatible with all EVM-based chains and allows seamless switching between EVM chains where all chains use the same address. While many newer native interoperable solutions such as Stargate (LayerZero), Synapse, and Hop Protocol integrate easily with MetaMask, most Cosmos and Polkadot chains use their ecosystem’s native wallets, such as Keplr and Polkadot JS. Users need to download new wallet apps and create new wallets, which adds a lot of friction to the user experience. This design may further deter new users from entering the ecosystem to try newer and more innovative options.
Information asymmetry
In a fledgling industry, the plethora of interoperability protocols launched over the past two years have made it increasingly difficult to track and determine the best path for users to engage in cross-chain activity. Therefore, the protocols that attract the most users tend to be those that have a formal partnership with the respective blockchain’s development team or foundation. In the case of Evmos, Nomad Bridge is the official gateway recommended for new users to bridge assets from other chains.
Despite the clear DYOR warning, official partnerships are often viewed by users as an endorsement of the security and trustworthiness of the recommended protocol. In the case of Evmos and cNomad, the Nomad bridge attracted the most transaction volume, with over $445.3 million in inflows, as users trusted Evmos’ advice, but was exploited only on August 1, 2022, losing over $186 million.
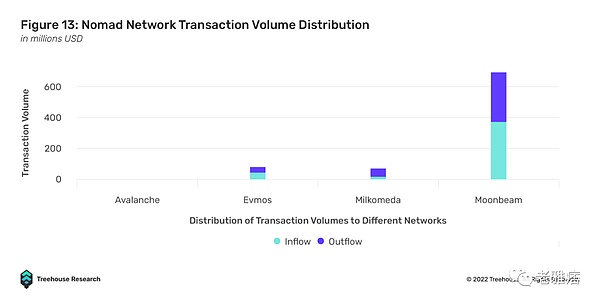
This brings us back to the problem of information asymmetry. While there may be more cost-effective and faster bridging solutions, users tend to go with the flow and choose the most “trustworthy” and “secure” protocol. Therefore, information asymmetry may prevent new native interoperability protocols from attracting more users because they do not generate enough awareness.
Interoperability between ecosystems
Traditional locking and minting bridges remain the most accessible form of interoperability, as users have a ready path to put their assets on any chain in the EVM and non-EVM ecosystems. While interoperability solutions such as IBC transfers are applicable to Cosmos, they are only applicable to the Cosmos ecosystem itself. For example, if users want to bridge their assets from Cosmos to the EVM chain, they will need to use another solution such as Axelar’s Satellite Bridge.
Regarding LayerZero, the protocol currently only enables cross-chain messaging for most major EVM compatible chains and Ethereum Layer-2 such as Arbitrum and Optimism. The protocol has yet to extend its connectivity to non-EVM chains, such as those in the Cosmos ecosystem and Solana.
The lack of interoperability within the ecosystem may also be partly due to the way these projects are funded. Different VCs support different ecosystems and are unlikely to open up their fields to others unless there is a material financial interest. It’s a prisoner’s dilemma among VCs, as narrative is still about building an ecosystem that rules everything — and the first ecosystem to transition to collaborative narrative takes a lot of risk.
Interoperability between ecosystems is still very fragmented, and the space is sorely lacking in bridge aggregators that can seamlessly aggregate liquidity across all bridges, liquidity networks, and cross-chain messaging protocols. As such, traditional locking and minting bridges remain the most popular options as they provide the highest degree of interoperability and convenience when moving assets between different blockchains.
Lack of interoperability use cases
Another reason the native interoperability protocol TVL is slow is that there are not many additional interoperability use cases other than bridging tokens. Therefore, ordinary users will not be incentivized to use the Stargate, THORChain or Cosmos ecosystems, as the added complexity will not give them additional benefits.
As we discussed in the LayerZero paragraph above, natively interoperable protocols can lead to interactions with other sovereign chains without having assets on them – the use case would be for users to migrate from bridges to new native An important impetus for a mechanistically interoperable solution, like simple bridging around tokens will become far less convenient than staking on one chain and immediately borrowing from other chains.
We realize that this leads to the causality dilemma, or rather, the “chicken and egg” problem between protocols building interoperability use cases and interoperability solutions becoming available. However, as more native interoperability designs surface, we believe developers at the application layer will innovate faster.
The future is multi-chain
In its current state, no single blockchain can dominate the industry in an efficient and user-friendly way. Each chain has its own niche design, but developers and VCs are blinded by the short-term urge to excel at everything and attract TVLs to offer users a similar but independent product. New projects, such as the nascent L1 chain, claim to solve the blockchain trilemma, when in reality they are only secretly sacrificing a pillar or two for other projects.
We believe that the real answer to the blockchain trilemma is interoperability, and that the answer to the interoperability trilemma is a natively interoperable solution, not a patch built on a mutually exclusive chain. The previous winner-takes-all crypto VC model is actually not conducive to building projects that are inherently interoperable. But as more people realize the potential of a truly interoperable blockchain world, talent and money are starting to flow into natively interoperable solutions.
The potential network effects in generalized cross-chain networks may be stronger than the narratives we’ve seen before. Being awarded an interoperability project is a chain-agnostic approach to betting that the blockchain industry will overcome barriers to mass adoption. Web 3.0 is at an inflection point and we look forward to a future where builders and users thrive in an interconnected blockchain world. Wagmi.
Like what you're reading? Subscribe to our top stories.
We will continue to update Gambling Chain; if you have any questions or suggestions, please contact us!