Author: Kerman Kohli; Translation: Shenchao TechFlow
We are currently in a bear market in the cryptocurrency market, which has suffered a heavy blow. Everyone is asking, what are the actual application scenarios and value of the technology products we are developing? Many people have put forward seemingly good points, but none of them have clear reasons to explain why these products are more advantageous than ordinary Web2 applications. I have been thinking about this question for a while, and based on personal experience and judgment, I am cautiously optimistic about certain viewpoints. This article is not about discussing ideology, but about focusing on practical issues such as technology and standards. Before we delve into it, let’s take a look at how the existing internet works.
Web2, Data Producers, and Identity Authentication
When you register for a service on the internet, the service provider does not actually know your real identity because all your information can be forged. Your IP address, browser cookies, device fingerprints, etc. are all just forgeable approximate identifiers. Everything can be forged.
This has led to the emergence of identity authentication standards that primarily rely on the following:
- Legal Analysis of Possible Embezzlement by Employees of a Digital Collectibles Company
- Can Bitcoin Dominate the World? Famous Podcast Says So
- Bao La Bao Za, what rules can be followed for DWF Labs’ market making?
-
Email address;
-
Password;
-
2FA (two-factor authentication) schemes.
Whenever you use a service on the internet, the service provider needs a persistent and secure identity to bind your data. More importantly, it provides a way for “you” to verify “yourself”.
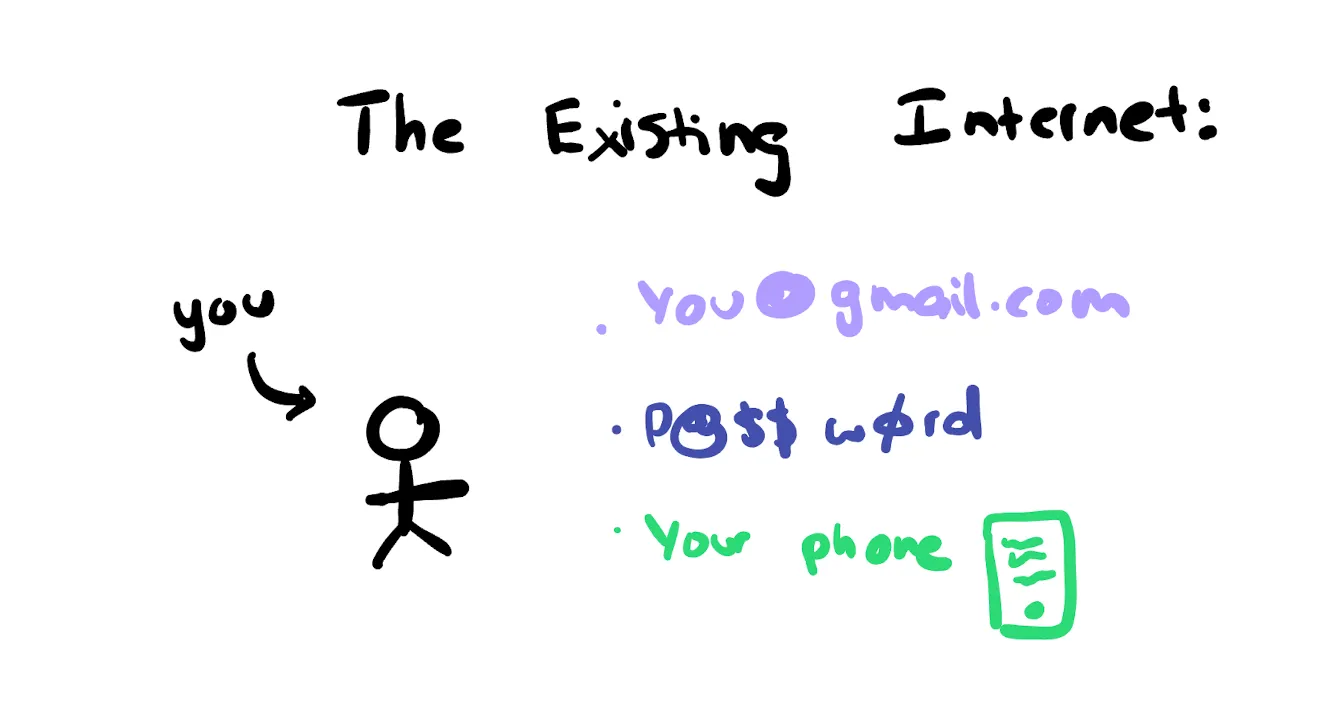
Each database creates a different identifier for you. Facebook, Twitter, Instagram will create a unique identifier for you in their databases.
When you log in to other services using OAuth, they can reference that identifier, but they will still create a new row in their own database to identify you. OAuth providers may share certain data points with external developers, but it is usually very limited. Then specific developers bind any information generated in their applications to the newly created user identifier in their database.
You may notice that in every service you use, “you” is represented repeatedly. This is not because Web2 has any malice, but it is the only logical approach given the current limitations of hardware. However, over the decades of the internet’s existence, this has brought about greater problems:
1. All your identity and reputation data is limited to the specific ecosystem you register in. Your Twitter followers are still Twitter’s data, and you cannot export it.
2. Any information created on the internet is linked to the identity within that service. Google comments can only display information about you that Google owns.
3. Every new service you register for requires you to rebuild trust and reputation within that ecosystem, despite what you have done in the past.
This is the environment we are in today:
-
Our profiles are the only things that identify us;
-
However, our information remains fragmented.
As the authenticity and credibility of all information on the Internet must be increasingly scrutinized, we are beginning to see that this is becoming a bigger problem. Whenever I read an article with strong opinions, I usually:
-
Find out who the author is;
-
Track their Twitter and any other sources I can find about them;
- Find citations of the article on other websites;
- Make an overall judgment on the author’s bias and opposing viewpoints.
However, I know that I am in the minority here. Most people unquestioningly accept the provided information without knowing the identity of the data producer (defined here as anyone who presents information in the form of articles, tweets, videos, etc.).
The key problem we collectively face is that we don’t have a clear way to definitively identify our online identities. Every time you visit a website, receive a message from someone, or receive an email, you run the risk of talking to the wrong person because we identify someone through a unique pseudonym. This has started to cause significant issues, and we can’t even identify ourselves in online communications.
I could be “XXX.eth” on the blockchain, “XXX” on Telegram, and “xxx” on another platform. However, if someone messages you on Telegram as “xxx,” you might think it’s me. Without public key authentication, trust on the internet is a mess.
Over time, the lack of stronger, persistent digital identity verification is a common problem that humans face.
Cryptography, Crypto Timestamps
Part 1: Cryptography
This may sound strange, but please bear with me. They are two different and seemingly similar concepts.
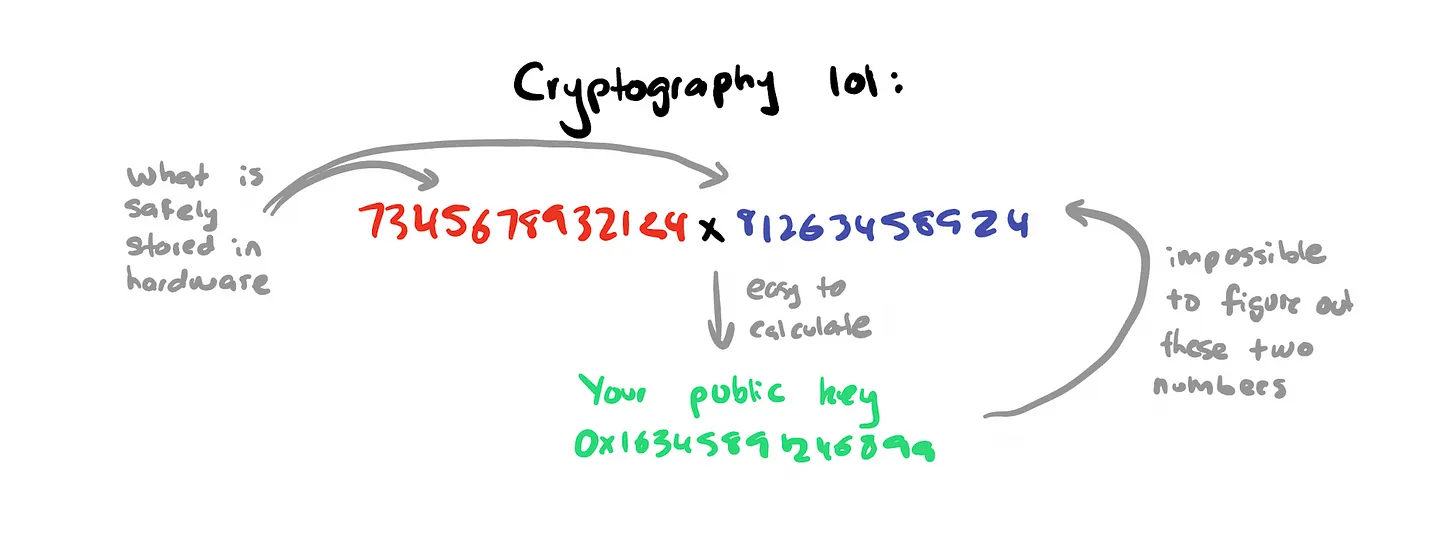
Cryptographic identity essentially involves multiplying two large prime numbers to generate a new, larger number. While this may sound simple, the complexity lies in the fact that these primes are essentially unguessable and practically unbreakable. When you authenticate with a private key, your hardware uses unique information to establish its identity. This approach represents a crucial shift in managing identity: the identity owner knows a significant number that is also recognized by the recipient’s common standards.
In contrast, traditional web infrastructure requires us to establish a new identity for every new service we use, resulting in different IDs for each database we join.
Part 2: Crypto
So how does blockchain come into play? The second tricky part of this puzzle is how do you verify when the information was broadcasted? If you simply sign a message with today’s date, how do you know you have the correct date? Perhaps you delegate the responsibility of time to another party, but what if they get compromised? You’ll end up with recursive logic.
Blockchain is, in terms of innovation, a database that records expiration date information. They do not have a human-dependent concept of time, but rely on block numbers to determine when something happens. I don’t think we fully realize how groundbreaking this is. You don’t send transactions with a “this is the transaction timestamp” field. You simply submit the transaction to the network, and when a miner mines it, it gets included in a block and assigned a timestamp.
Think about it, what system exists where you give it information and it tells you when that information actually happened. We always expect that when we say something or communicate online, that’s when it “happened”. Not in the world of cryptocurrencies. When we want to convey information on the chain, we just need to express what we want to convey, and the blockchain will tell us when it happened.
Summing it up:
-
Cryptography created shared identity verification standards that we all can agree on;
-
Crypto powered by blockchain created shared time standards that we all can agree on.
Why is identity important?
In our frenzy for wealth, we have all forgotten that blockchain represents two fundamental innovations. This also means that we can start changing the world by introducing one innovation and slowly adding the second one when it makes sense. You don’t need to apply both simultaneously to make an impact.
By 2023, with the emergence of AI, the world will need stronger identity standards. Information is the foundation of our society, but when trust and verification of information decline, we end up in some dangerous places.
Sending stablecoins and playing casino games are fun, but cryptocurrencies can address larger interests and solve bigger problems faced by society today. Due to being built on the foundation of cryptography, cryptocurrencies have a larger ecosystem in terms of cryptographic standards than anywhere else. You can already see cryptography becoming the gold standard with Apple adopting LianGuaissKeys and the rise of OTP for enabling 2FA authentication.
-
In Web2, cryptography is a second-class citizen.
-
In Web3, cryptography is a first-class citizen.
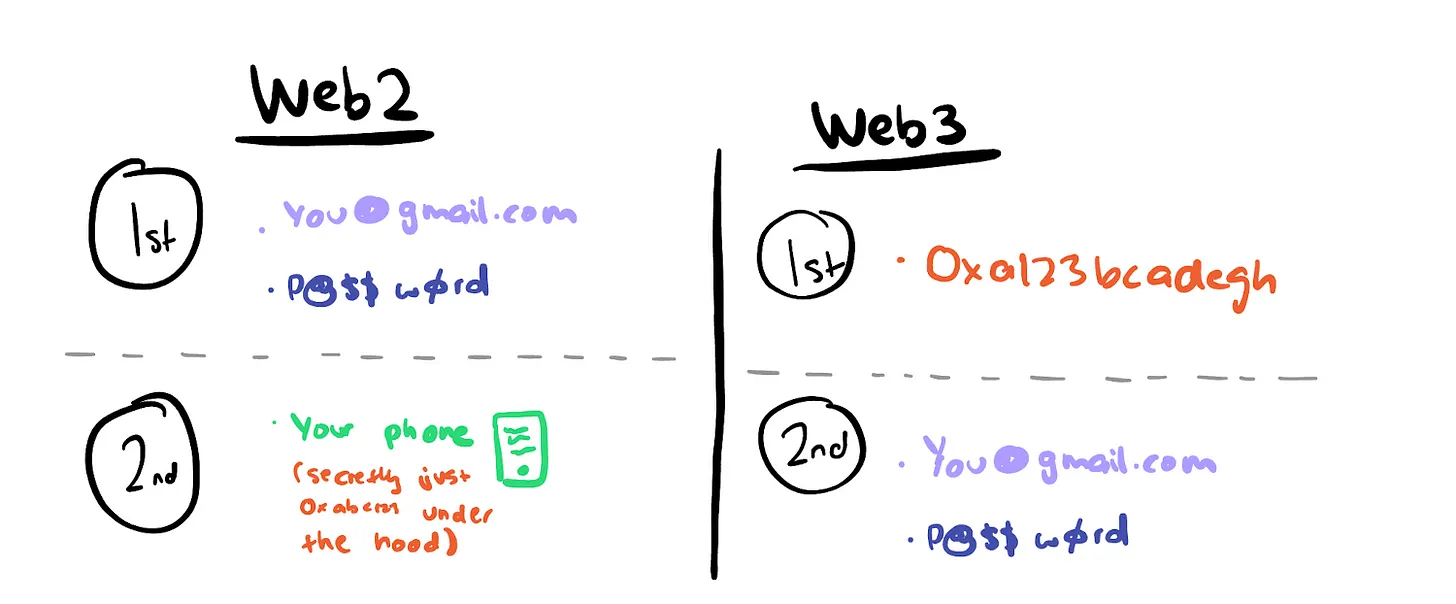
Alright, now that we’re all on the same page, let’s talk about cryptocurrencies and identity. Over the years, I have been deeply involved in this issue, and I believe I have found some key links that were not obvious before. The biggest use case of cryptocurrencies is not “decentralized identity” or some noble ideal, it involves:
-
“Owning your own data and profiting from it”
-
“Uploading your passport on the blockchain for better KYC”
-
“Linking your Twitter, Facebook, and Ethereum addresses together to create a new identity”.
These concepts are far from reality, they are just empty narratives without creating products that can help real users. These narratives are mainly used to attract massive funding from investors without adding value to end consumers. To clarify these misconceptions, it is important for us to use better language to describe what we are talking about. I think when people even say things like “on-chain identity,” they draw the wrong conclusion because it implies that you have to operate on the chain. That’s not true.
The Road Ahead
Permissionless Identity: “Portable, Persistent, Crypto-supported Identity”
They are what we know as public keys today. Whether the data is on-chain or off-chain is not important. The key point is that you can identify/authenticate yourself on digital services using your public key. All information is tied to your public key, thereby achieving interoperability.
However, this is the reason why they have clear advantages over any other Web2 systems we have today:
-
Build in one environment, use in another. All your activities and data in one ecosystem can be accessed in a completely unrelated ecosystem.
-
Permanence. Once the private keys are derived, they don’t disappear. You can’t delete private keys or on-chain data.
- Can be used on-chain or off-chain. Your identity is a combination of all the places where you authenticate yourself as a public key on-chain or off-chain. The key is innovation, not blockchain.
-
Ability to create new identities (or fragments) with a button click alongside existing identities. Unlike Web2, where all identities are ultimately tied to your passport (phone number, internet service provider), permissionless identities can be created or fragmented without permission.
-
Anyone with internet connectivity and access to the right hardware can use it. There is no “issuing” authority to generate identities. As long as you have the right infrastructure to protect your identity, you can create one. Because of its borderless nature, there are no limits to what you can do with this identity.
Conclusion
Permissionless identities fundamentally support a whole new category of applications that are 10 times better than the applications you see on the existing web. A world where one app improves the experience of all other apps. You will see the beginning of a flywheel effect, and I see its development as follows:
-
As applications like encryption consumers emerge, they will naturally rely on permissionless identities as a natural authentication standard.
-
These applications will be able to start perceiving the context of your past behavior and actions in other applications and environments.
- The ability to “import” the context from the past and elsewhere can create a better user experience.
-
Users demand more application support for public key authentication for logging in and using applications.
-
As the number of applications supporting public key authentication increases, the utility obtained from their permissionless identities also increases.
I dare to bet that the main use case of encryption has arrived: applications based on permissionless identities. The sooner we realize this, the faster we can move forward in creating applications that people actually need.
Like what you're reading? Subscribe to our top stories.
We will continue to update Gambling Chain; if you have any questions or suggestions, please contact us!