Currently, most L2 Sequencers adopt the “first come, first served” (FIFS) transaction sorting method to protect users from MEV, but this also weakens the value of the blocks.
With the BlocksLianGuaice scheme, we can achieve the best of both worlds.
The specific process is as follows: users encrypt their transactions with a “time puzzle” and simultaneously calculate a “zk proof” to prove that the time puzzle “has a solution.” Then, they send the time puzzle and corresponding zk proof to the Sequencer.
After receiving the encrypted transactions, the Sequencer:
- Opinion Blockchain relying on AWS will not bring transparency to artificial intelligence.
- World Engine A Shard Rollup Framework Designed for Full-chain Games
- Curve is attacked, making its founder Mich Will’s Aave debt vault become dangerous.
-
Verifies the validity of the zk proof, which indicates that the time puzzle can be solved after a certain period of time;
-
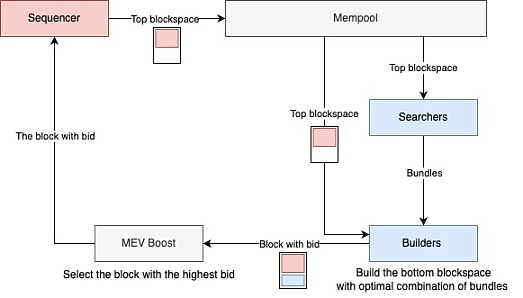
Places it in the “Top BlocksLianGuaice” and provides the “Order Committee” within the block where the transactions are located;
-
The Sequencer calculates the time puzzle for a certain period and finally obtains an answer;
-
After obtaining the answer, the Sequencer can decrypt the user’s “encrypted transaction” and obtain the “original” data of the transaction;
-
After filling all the “Top BlocksLianGuaice,” the Sequencer broadcasts the “semi-finished block” with transactions only in the “Top BlocksLianGuaice” to the L2 p2p network;
-
MEV Searcher receives the “semi-finished block” and constructs its own profitable “transaction bundle” based on the transaction order in the “Top BlocksLianGuaice”;
-
MEV Searcher sends its “transaction bundle” and “bids” to the L2 Block Builder;
-
At this point, the Builder has received the “semi-finished block” and puts the part of the “transaction bundle” with the highest bid into the “Bottom BlocksLianGuaice”;
-
Finally, the Builder needs to go through the L2 Mev Boost process, and the Sequencer will accept the “highest-value block” with the specified “Top BlocksLianGuaice”.
Summary
By dividing “BlocksLianGuaice” into two parts, user transactions can be protected in the “Top BlocksLianGuaice,” allowing the Mev Searcher to focus on the “Bottom BlocksLianGuaice,” thus protecting user transactions from harmful MEV, while the Sequencer maximizes block revenue. However, this scheme incurs additional computational costs, mainly because users need to calculate a “zk proof” for their time puzzles, and the Sequencer needs to solve the “time puzzle” provided by each user.
We can compare this approach with Arbitrum’s previous proposal to allow the Mev Searcher to prioritize transactions with a higher bid for the highest 0.5s. Compared to the approach proposed in this article, Arbitrum’s approach has the following characteristics:
-
Saves computational resources;
-
The MEV Searcher cannot see the transactions in the block (Private Mempool);
-
User transactions can still be bypassed.
Lastly, it is worth mentioning that the reason for needing “zk proof” is to prevent the sequencer from being attacked by DDOS.
Like what you're reading? Subscribe to our top stories.
We will continue to update Gambling Chain; if you have any questions or suggestions, please contact us!